 Figure 2 |
||
This is the professional version of the original File Cleaner, named FileCleanerPro. It is now available under the GNU-GPL Ver. 2, and is a much improved, debugged, and memory checked version of the original application. Primarily developed for the Microsoft® Windows XP platform, it addresses concerns over the security of information on any Microsoft® Windows compatible computer system. Full documentation is included with the download package (actually it's this web page!).
This application is targeted to anybody who requires absolutely secure
deletion of information from a hard drive short of physical destruction of the
media itself. Private individuals, legal firms, corporate patent offices, law enforcement
agencies, local and county governments, state governments, the federal government, and
military clients will get the most use out of this application.
FileCleanerPro will
securely overwrite folders and their content, with both the random character
generation and wipe patterns designed to permanently erase information from the
media. Both methods employ and are scrambled by long period random
number generators that pass all of George Marsaglia's DieHard1 random number generator tests.
If you're a pederast, or are engaging in any kind of criminal activity that you wish to erase from your computer, then this application isn't really for you. Though this application is designed with the idea of secure erasure of information from a computer's hard drive, it actually doesn't erase all of the tracks of your Internet transactions, and wasn't designed to do so. It will also not erase the tracks of your Internet transactions from your Internet Service Provider (ISP). Your ISP may record where you visit on the Internet, and what you download, above and beyond any record of your transactions on your machine. Though this application will erase some of the tracking, and anything you may download off of the Internet, neither Happy Cat Technologies nor this author are responsible for your arrest and subsequent imprisonment if you are visiting child pornography sites or soliciting criminal activity!
If you are intending to securely wipe a whole hard drive, then you probably shouldn't use this application either. It would be very time intensive to securely wipe a 70 GB hard drive, in example, as the secure wipe pattern entails 35 separate writes to every file that you wish to securely wipe. Conservative estimation of the time required to securely wipe a 70 GB hard drive is about 4.9 million seconds, or 56.71 days! Obviously not for you!
Finally, this application is also not intended for Flash Drives (Lexar,
Sony, etc.). Flash drives operate on the principle of charge tunneling,
and are not susceptible to analysis via magnetic force microscopy, nor are the
write patterns optimized for Flash type media. However, FileCleanerPro will work on your Flash Drive, at a reduced speed as
compared to a hard drive.
It's a relatively fast (for the processing involved), and very efficient piece of code that does something none
of the others do, and that is actually wiping the information from your hard
drive so that it is unrecoverable via even magnetic force microscopy, at least
in theory (The author doesn't have the lab resources to prove it, that's up to
you if you're up to the challenge). There's no extra bells, whistles, or packaging, and it uses some very
sophisticated coding to insure that the data you wish to destroy is actually
irrevocably denied. You should use this application if you have critical
information that encompasses a folder or set of folders, at most, and you don't
wish to physically destroy the hard drive.
FileCleanerPro works by insuring that the data is actually erased from your hard disk, rather than just placing it into the Recycle Bin, or just simply deleting it from your directory structure with low level commands. Further, FileCleanerPro uses proprietary methods to insure that the information is unrecoverable by implementing the methods described in Secure Deletion of Data from Magnetic and Solid-State Memory2 available from SourceForge.
FileCleanerPro, with Operate on Temporary Internet Files checked, starting from the folder "C:\Documents and Settings", recursively searches for the following folders:
FileCleanerPro further insures that no folder names are duplicated in the search, as in example, "Content.IE5" is a subfolder of "Temporary Internet Files".
There are four modes of operating to FileCleanerPro:
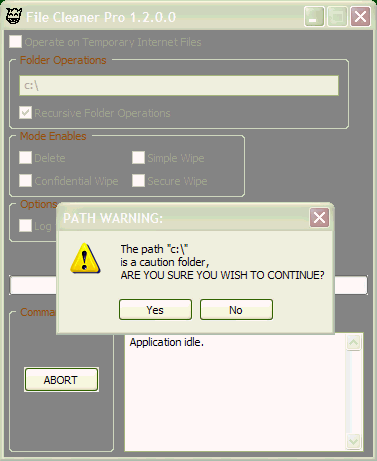
The user interface is straightforward. Figure 1 shows the user interface as it appears on startup, scanning mode, before processing any folders. Figure 2 shows the user interface as it appears during operation, with a warning box showing, due to the fact that the user has requested a caution folder, i.e. the root of the C:\ drive. Figure 3 shows the user interface during an actual Secure wiping operation on the temporary Internet file area on a Dell Optiplex GX280 running Windows XP Professional. This is a worse case scenario, time-wise, and is used as an example of the processing time required to handle secure wiping. Figure 4 shows the completion of the Secure wipe cycle, showing that out of 451 files found, only 392 files where able to be deleted due to ownership and access errors. Figure 4 also shows the estimated time computation bug mentioned below, with the estimated time being reported as 11 min. 36 seconds, and the actual completion time being ~9 min. 34 sec. The difference between the count of files found vs. the count of files deleted (and securely wiped, which doesn't show on this picture but is reported on the line above the top line) is due to not running under full ownership privileges. Some of the files and folders operated on where in areas outside of the ownership of the user, or where locked due to IE still being active, hence the 55 ownership errors. The eight access errors indicated in Figure 4 result from Internet Explorer crashing during execution of this application, for the reasons listed below, and those files where no longer available for wiping with respect to the file list that is generated after the Start button is pressed. This is an issue resolved by closing all IE windows prior to clicking the Start button on FileCleanerPro.
The user interface detailed description is as follows: (all user inputs have tool tips associated with them, and please use the browser Back button to return from following a link.)
Please be cautious with the use of FileCleanerPro. At minimum, you could delete data you actually want to keep by careless, negligent, or malicious use. It is recommended that if you are operating in a folder, that you first view the folder with Windows Explorer (synonymous with the My Computer icon), and right click on the folder name to get the Properties window open. Observe the count of files reported in the Properties window for the folder, and then use FileCleanerPro in scan mode to verify the count of files. Any discrepancy in the file counts between the folder Properties window and the count of files found reported in the File Cleaner Status/Results text box probably indicates files with the hidden attribute set. These hidden files may also be system files and wiping or deleting them could have significant effects on the operation of your computer. Deleted files sometimes may be recovered, however FileCleanerPro does not use the Windows Recycle Bin, and it will take a low-level file utility to recover deleted files. That is provided that they haven't been wiped!
Again, I must reiterate that wiping in any mode is an unrecoverable process except possibly by those technologies mentioned reference [2]. Wiping in Secure mode is an absolutely unrecoverable process. Implementation of file recovery based on the techniques covered in reference [2] will probably not be cheap. Further, neither this author nor Happy Cat Technologies will be responsible for careless, negligent, and/or malignant use by any individual who uses FileCleanerPro.
Finally, with the above two paragraphs in mind, please be sure that you actually want to do what you configured FileCleanerPro to do before you press that Start button!
A good way to test the operation of this software is to, first of all, download the package and install the executable in an appropriate folder. Then go onto a website with images and browse around. After that select the File -> Work Offline option from the Windows dropdown menu bar on your browser. Use FileCleanerPro with delete enabled, and then attempt to refresh the page while staying offline, which will give a warning window titled "Web page unavailable while offline." Select the "Stay Offline" button and you should see significant differences in the web page! This is because files being used by the webpage have been deleted and when it attempts to refresh the page from the temporary Internet file cache, those files are no longer present.
This author would recommend that Linux/Unix users not attempt to use FileCleanerPro, as it's designed with Microsoft® Windows operating system in mind. Results of it's use on Linux/Unix systems, are to say the least, unknown!
FileCleanerPro has been verified on the following operating systems and machines:
The un-recoverability of information after using File Cleaner Pro using magnetic force microscopy has not been verified. Please feel free to test it out for yourself if you have the technical expertise and required equipment. Though I do have the technical expertise, I lack the required equipment. If after doing 35 data overwrites the data is still present on your hard drive, then your only option is to physically destroy the media. Please notify the author in that event.
Timing tests on a test file set of 1000 files containing 996,481 bytes of data, created with Test File Generator, indicate the following average data:
Random number generation is a complex topic, with many references and papers available on the subject. There is no such thing as a truly random number generator, at least with respect to computer applications not dealing with quantum computation. Therefore, all random number generators are actually pseudo-random number generators.
Research into random number generation using standard library functions showed that while the library random number generator was very fast, it was extremely poor as a pseudo-random number generator, having severe deficiencies in period, spread, etc. The random number generators used in this application where researched and tested for long period, repeatability, and most importantly, that they pass the Diehard1 tests. They have both been statistically tested to insure that they fit the criterion for randomness. However, they are slow, with respect to the standard library random number generator.
A problem with pseudo-random number generators is that if you know the seed value, you can reproduce the random number sequence. This is a flaw in any pseudo-random number generator due to its very nature, that being that its output is the result of deterministic computations. Therefore, to insure that the seed value is irreproducible, steps where taken to make the seed value indeterminate.
The primary random number generator used, Mother, is an implementation of the ideas proposed in George Marsaglia, "The Mother of All Random Generators"3 This implementation of it has been significantly tested via Diehard1, and also via Microsoft® Excel (with a reduced size dataset), on data sets of 300,000,000 16-bit integers. As opposed to the C++ standard library function rand(), it is excellent, albeit rather slow. It comprises 17 lines of C++ code in integer math, and has an execution time of ~200 nanoseconds per number on a Dell Optiplex GX280. Statistics are available on request (Excel file: ~6.6MB, Diehard results: 49KB text file.), as well as the code used to generate the data files. On a given sample run (~300MB data file size), it's overall p-value after applying KStest on 269 p-values is 0.321958, with an average p-value of 0.490444. The exact results of the Diehard tests appear to be seed dependent, and do vary, however the values are always within acceptable ranges for both Mother and Secure I, below.
The secondary random number generator, named Secure I, is used to scramble the wipe pattern sequence, and is an implementation of the Wichman and Hill procedure4. It comprises 11 lines of C++ code in integer and double precision math. Secure I has been tested in the same fashion as Mother, and has an execution time of ~975 nanoseconds (i.e. very slow, on the same machine as above). The statistics information and generating code is also available on request (Excel file: same as above, ~6.6MB, Diehard results: 49KB text file). Secure I's (with an ~300MB data file size) overall p-value after applying KStest on 269 p-values is 0.771651, with an average p-value of 0.494344.
Finally, as an example, the C++ standard library random number generator, rand(), has an overall p-value after applying KStest on 269 p-values of 0.000000, with an average p-value of 0.561792. This is a significant failure of randomness! With respect to Diehard, George Marsaglia's DIEHARD Test Suite is very complete and has been used by companies such as RSA to evaluate their cryptography products. The test suite includes around 14 tests. A description is included with the program and makes an amusing read: not only because of the funny names (e.g., the Parking Lot test) they have but also because they seem surprisingly convoluted. Most of them return a p-value that should be in the range [0,1]. Occasional values could be near 0 or 1. For a very bad sequence you might see a p-value like 1.000000 or .00000."5 (authors italics and underline) The best possible p-value is 0.500000. An example is a DNA test from the Diehard test suite for the Mother implementation, using an ~350MB data file. The test line identified that it was using bits 9 to 10, where the expected mean number of missing words is 141909, and Mother came up in this instance with a value of 141910. The z-score that resulted was 0.0020, with a p-value of 0.500789.
Further documentation on random number generators is available by
Googling for them, and from references [6] and [7].
As of the time this release FileCleanerPro has no other bugs known to the author. Please contact the author if you find a bug. The beta version will have free debugging for its lifespan. Also, if you wish to see this application updated for previous versions of Microsoft® Windows that is inoperable on (if that is the case), please again contact me with the issue, and I'll modify the software to suit that operating system version.
If you experience any type
of memory error warnings from Internet Explorer (IE) or other browser during any operation of
the browser after using FileCleanerPro in Operate on Temporary Internet Folders
mode, or your browser crashes, this is not a bug
in FileCleanerPro. What has occurred is that a file necessary to the
browser has been
overwritten with random data and/or deleted. It could be annoying, in that the
browser
crashing will cause all open browser windows to close. Therefore, if you experience this
kind of error, please close all browser windows before using FileCleanerPro.
So far, it's only an issue with Internet Explorer, and depends on the web page code, such as
JavaScript's and Java applications.
This demo version of File Cleaner Pro is freeware, and is unrestricted. It is released under the GNU General Public License, Version 2 as the source code is now included in the release.
Download
FileCleanerPro
1.2.0.0-20060320.zip (~1,107KB) now. The executable CRC-32 (WinZip) is FF10FF34, the size
2,509,824 bytes.
FileCleanerPro took approximately 150 hours to develop. Hopefully, you found or will find FileCleanerPro useful. If you did, then a small voluntary donation would be appreciated for the hours expended developing FileCleanerPro.
