DIFF = 1/50
TOOLS USED = OllyDbg 1.09b
AUTHOR = Zephyrous
I though there should be some tutes for very beginner to use this very cool debugger.
Because it is windows application debugger, we can take all needed
screenshots for more understanding. It has many useful functions to be explored and used.
This is my 1st tutorial in english and pls forgive me for bad english. But i hope you can understand it. If you dont.. WHO CARES!!!!!
First at all.. run the target to examine what part to be cracked. It is a nag screen and a disabled menu.
If you satisfied what to be attacked, open the crackme.exe with olly or u can press F3 to bring open dialog box out.
To find the location for code of the nagscreen.. we can find it through 'Reference text strings'.
For this function, u can right click at the code window. After that we would find strings in the .exe

Ok.. great.. The nag screen message is listed in the box. Just double click on the line and olly will bring you
to the target asm codes.
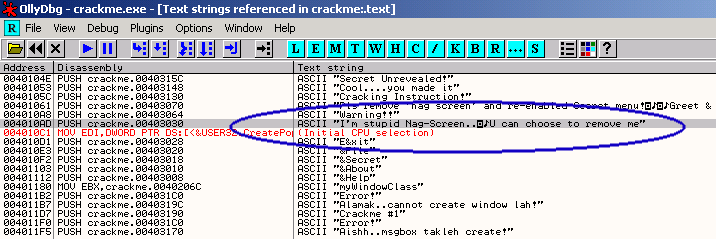
This thing need little explanation... The nagscreen box is just a MessageBoxA function, the most basic dialog box.
You need to refer win32.hlp or MSDN library to learn about MessageBoxA. By the way, i want to explain the basic here. Before MessageBoxA could been called, it need some arguement to be pushed.
int MessageBox(
HWND hWnd, // handle of owner window
LPCTSTR lpText, // address of text in message box
LPCTSTR lpCaption, // address of title of message box
UINT uType // style of message box
);
Refering to the win32.hlp, the 1st must be pushed is style value of the
messagebox, then Title for the message box followed by text message and
lastly handle window (hwnd). For you acknowledgement, the arguement value
will be pushed from right to left according to 'C calling convention'
nature.
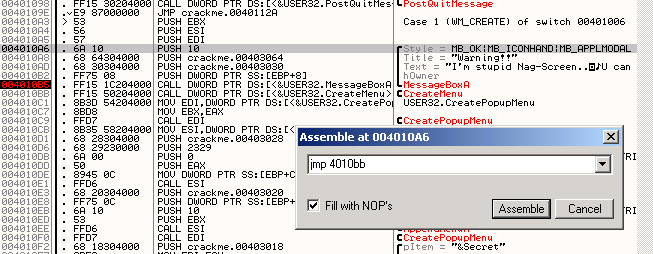
After the crackme program has been runned, it will reach at relative virtual
address(RVA) 4010A6 where it started to push MessageBoxA parameter.
To get rid off the nagscreen.... we have to skip this lines from be executed
'computer'. The best way to do it is make a jump at first paramater of
MessageBoxA will be pushed. There is 4 lines of asm code to be skipped.
At 'PUSH 10', we have to double click on it to bring Assemble dialog.
We will change the code to JMP 4010BB as shown in the screenshot below.
At 4010A6 we will jump to 4010BB and the nag permanently will be removed
;-)))).
You will see the code at
004010A6 | 6A 10 becoming
004010A6 | EB 13
The olly assembler saves our time again...don't need to refer Hex Opcode
tables.....What a joy. ;-))))
The finding of 'Secret' Menu
This part is very easy compared to previous cracking work even it is a
secret menu. The trick here is just make the menu grayed and cannot be
access.
Once again... we have to use 'Reference text strings' to locate the code
for it. Similar to previous step :-)
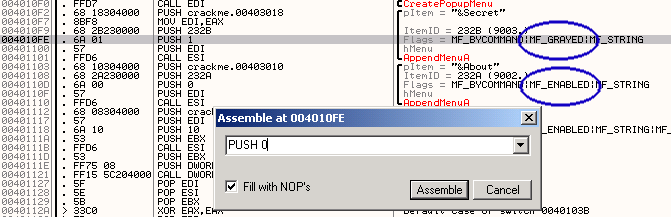
BOOL AppendMenu(
HMENU hMenu, // handle to menu to be changed
UINT uFlags, // menu-item flags
UINT uIDNewItem, // menu-item identifier or handle of drop-down menu or
submenu
LPCTSTR lpNewItem // menu-item content
);
refering to win32.hlp
MF_ENABLED Enables the menu item so it can be selected, and restores it
from its grayed state.
MF_GRAYED Disables the menu item and grays it so it cannot be selected.
the hex value for MF_ENABLED = 0 and MF_GRAYED = 1
I bet you what you have known what to do next :P
The .exe actually has been patched on memory.. but we have to make another
.exe with modified asm codes.
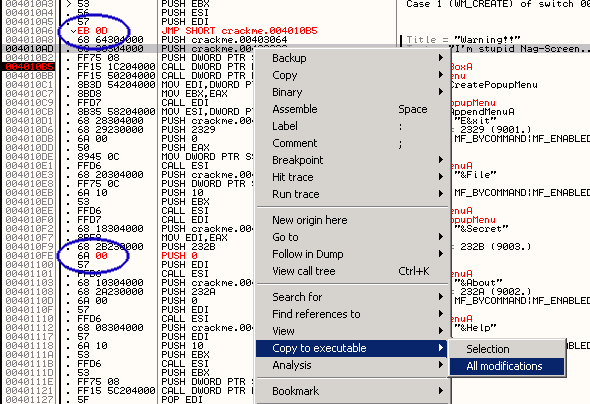
All we have to do is right click in the code [C] child window and find
the menu as shown above. When asked.. press 'copy all' since we have 2
line of patches.
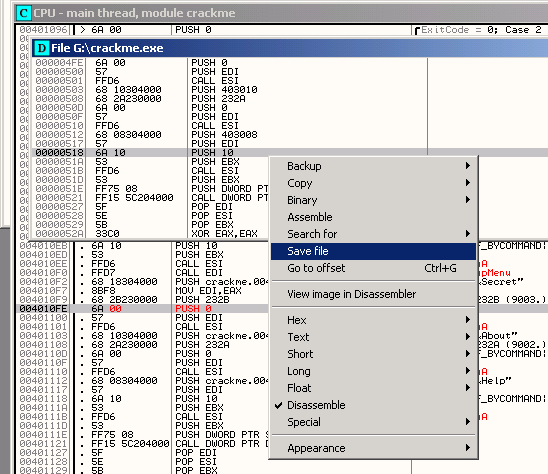
Lastly... right click in File [D] window... save the .exe file with other
name like patched.exe or fucked.exe or my1stcrack.exe :D
Bingo!!! We finish this cracking task..Congrats dude.
Greetings and respect list: (not in specific order)
Cik Siti, Ancient_One, Kwai_Lo, ManKind, Bengaly, ytc, snaker, fuss, Detten, chainie, stingduk, _pusher_, evileuA, X-Lock, kiyo, BiW-Reversing team, and all crackers/reversers out there..(You know who you are)...errrk.. you too Bor0 :P
I can be reached at r_etarded::at::yahoo::dot::com