|
| Registration Troubleshooting for Activity and Authentication Analyzer |
The Activity and Authentication Analyzer is now copy-protected in two ways:
 |
| Current registration scheme |
Beginning from the 1.61 version of Activity and Authentication Analyzer the copy-protection scheme was changed.
- The place, where the new registration key is stored, can be found in the system registry in the following key: HKEY_CURRENT_USER\SOFTWARE\AAAnalyzer.
One can open the system registry by the Regedit.exe to see all values created and used by Activity and Authentication Analyzer while performing common routine.
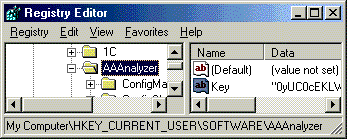
One can extract the system registry content corresponding to the AAAnalyzer to the text file with .reg extension. It may be needed to send the key, which is seemed to be valid, to the author for verification procedure.
One can export the relevant AAAnalyzer system registry branch by selecting the AAAnalyzer key in the left pane of Regedit, and opening the Registry menu item, later clicking the Export Registry File, and at last entering the generic file name in the dialog box for the reg-file with AAAnalyzer content. After clicking OK button in dialog box the needed system registry branch will be saved in text file.
- Now, one substantial parameter Hardware ID was added while creating the registration key.
The Hardware ID is brief ciphered form of the unique label of the hardware present in PC where Activity and Authentication Analyzer used to be launched.
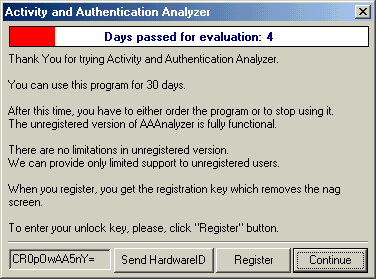
One can press either Ctrl+F9 hot key combination to see the Hardware ID string.

or see Hardware ID string on initial nag screen box:
 |
| Installation |
There is no particular requirements or additional routines for the installation of AAAnalyzer to your system. Simply, unpack file containing installer of Softwrap™ version and follow offered by installer questions.
 |
| The changes made in comparison with old GlockSoft scheme |
The support of old registration keys given by GlockSoft is removed since the release of the 1.61 version of Activity and Authentication Analyzer.
Such keys are treated as shareware keys.
 |
| Three shareware modes |
There are three headers for the Activity and Authentication Analyzer application showing what the shareware mode is used in Activity and Authentication Analyzer.
Header: Activity and Authentication Analyzer - Shareware version means that this is either launch with no key or key is not valid.
Such a situation can appear when no corresponding value with registration key is present in the Windows system registry, or value storing the registration key was changed or deleted and not fit for the valid registration.
Such a situation can also occur when the hardware is changed where Activity and Authentication Analyzer has been launched.
There can be some ways to solve such a problem:
If the value was deleted simply reenter it. If the hardware was changed, your present registration key is nor more valid and you need a new one for your PC.
Header: Activity and Authentication Analyzer - Obsolete GlockSoft key version means that you are using the old registration key provided by GlockSoft.
Such a registration key is treated as not valid and one need new key to remove shareware limitations. This key is considered as Shareware one.
Header: Activity and Authentication Analyzer - Conterfeit key version means that key was tried to get faked using internal cipher scheme, but such a registration key is treated all the same as not valid. This key is considered as Shareware one.
 |
| Problems with the legal keys |
If some problems occur while registration and you are convinced that you have the valid key provided by the author, it seems reasonable to turn to the author with next steps:
You can send your current registration key together with the Hardware ID to the author of Activity and Authentication Analyzer to check the key. Your previous Hardware ID is stored in the Legal Users database and can also be compared with the one you sent to reveal the situation when the hardware has been changed. Your registration key can also be examined to prove the integrity and identification by the author using special software used for the shareware copy protection.
|