Planning pedagogy for i-mode: from flogging to blogging via wi-fi
Colin Lankshear and Michele Knobel
IFTE Conference, Melbourne July 7 2003 (35+ pages)
An issue of context
It is often observed that a wide and widening gulf exists between the forms of literacy students engage in within school settings, and the manner in which they engage in them, and those they encounter in their worlds beyond school. Just what follows from this observation, however, is less clear so far as implications for school curriculum and pedagogy are concerned.
It does not follow that because some practice is widely engaged in outside of school that it should be addressed, or even taken account of, within school. Determining the extent to which, and manner in which, school learning should respond to social and cultural practices from the worlds beyond school involves consideration of complex educational, ethical and policy issues. Such issues are especially vexed around "new literacies" mediated by new computing and communications technologies. To explore some aspects of what is at stake in the relationship between various new forms of literacy emerging in the world beyond school and literacy practices within the school curriculum we will address three main questions here.
A telling case
The key issues are not confined to schools alone. They apply to formal education at all levels. Steve Thorne (2003) has recently written about tensions between learning pedagogy and cultural practices and values integral to young people's identities in the context of a French course at a U.S. university. The course had been designed to incorporate use of a range of CMC tools and activities, including in-class synchronous exchanges between French and US key pals using MS Net Meeting software and a video conferencing link. The U.S. students were also required to engage in email communication with their French key pal counterparts. Unlike the chat and videoconferencing, however, the email component was integral to course assessment.
Interestingly, emailing proved very unpopular with some of the students. In conversation following the final Net Meeting session and a follow up interview, two 19 year old female students spoke disdainfully of email as a friendship communication medium. Grace and Stef associated email with "communication between power levels and generations" (ibid.).
Researcher: Can you all follow up with e-mail or? [in reference to the final few minutes of the last chat session of the term]
Stef: Yeah, but I hate writing e-mails.
Researcher: Really?
Researcher: So are the e-mail exchanges just not as dynamic as this, or=
Stef: No [they aren't]=
Grace: =But I think it's also because we have, like we communicate with a lot of people now through AOL [instant messenger]. That's so like that's how I talk to all my friends at different colleges=
Stef: =and here=
Grace: =We don't send e-mails back and forth to each other to like catch up. Like we just talk [using IM]. It's very like=
Stef: =Yeah, it's just, like, what we're used to.
Researcher: So you don't use e-mail that much normally?
Stef: I almost never do. I just use it for teachers and stuff=
Grace: =teachers, yeah. Or my Mom [laughs]. (Thorne 2003: 5)
In a brief interview Grace elaborates further as follows:
Interviewer: Do you e-mail much?
Grace: No not that much. Just mostly for communicating with professors.
Interviewer: And for your key-pal?
Grace: I just e-mailed him a couple of things in English … and then I was like, I'm not talking to him any more except in the NetMeetings. And then [the Instructor] was saying how like we have to do that, but then I didn't [laughs]. I didn't e-mail him any more .... Like I just, it just wasn't very convenient I guess. Like if you had AOL Instant Messenger I would just, you know, type in something every so often or whatever, but it's different than e-mail .... It's like, "Oh God, I have to write an e-mail now." Like it's just like, you don't want to, it's like an effort. Interviewer: So how many times a week do you e-mail friends?
Grace: Never.
Interviewer: Never?
Grace: Never. (Thorne 2003: 6)
These power and cross generational associations connoted the inappropriateness of email as a medium for "age-peer relationship building and social interaction". Yet, these were the teachers' main purposes for the intercultural exchanges. For Grace and Stef there were "right" (appropriate) and "wrong" (inappropriate) cultural tools for the kinds of exchanges occurring between them and François, Indeed, Grace's belief that email was an inappropriate medium for mediating interpersonal age-peer interaction and relationship building meant that even though Grace (and Stef) liked Francois, their French key pal, and overall enjoyed the intercultural exchange project, she chose not to participate in the email component: notwithstanding "the coercive force of the graded assignment given by the instructor to continue e-mail exchanges" (ibid.: 7).
Through particular forms of cultural participation we all help to construct particular patterns of norms and forms for the use of specific artifacts (in the present case, software tools for communicative practices). These constructions have existential force. They mobilize certain kinds of personal "identity-related investments" and discourage others.
The meaning of cultural tools, and their perceived acceptability or appropriateness as media for teaching and learning activities are often closely linked to how individuals see themselves--their affinities, identities, etc.--and these associations may run deep. Grace, particularly, saw email as an unacceptable medium for social age-peer exchange: even within the context of artificial social interactions that had been induced for curricular purposes. Part of the way Grace saw herself was as a person who does not communicate socially in close and friendly ways by means of email. She would, however, have been prepared to use IM for the curriculum activities, had it been available as an option.
Of course, it does not follow from this that other (let alone all) students would be prepared to have IM used as a communication mode within formal educational settings. Many young people prefer to maintain a strong demarcation between modes and forms of communication (and other social and cultural practices) they associate with their lives outside of school--which are often the lives they experience as most authentic and meaningful--and what they do and how they do it within school.
Here today, gone tomorrow
Thorne notes that Grace and Stef represent a third generation of computing technology users within societies like our own. They are the first generation to have been socialized from an early age into using the Internet and have now reached an age where they are "active as keystone species in the production of digitally mediated knowledge and culture" (ibid.: 7). Their computer-mediated communicative practices mark a sharp break with what we have known since the earliest times of the internet. For the first time in the history of CMC, says Thorne (ibid.), "email is no longer a generic tool that most Internet users employ for everyday social and work interaction.New tools, like IM, now mediate social and age-peer interaction for a young generation of users".
In fact, for many young people in many parts of the globe, IM is already no longer where it's at. Grace's generation and the one following her are currently experiencing the transcendence of IM by tools and practices that are even more immediate, as well as far more complex and multifaceted. The current change involves the proliferation of mobile telephone "texting" augmented by an increasingly elaborate convergence of wireless information and communication applications.
The rapid development in the scope, uses and convergence of mobile handheld communication and information devices during the past five years has ushered in the moment of what Howard Rheingold (2002: xi) refers to as "i-mode" and the proliferation of "smart mobs" (ibid.).This involves the convergence of mobile telephony, radio chips, the Internet, location awareness capacity, and similar processes and capacities. Echoing Jeff Bezos' (Spector 2000: 16) distinction between first and second phase automation, Rheingold argues that Mobile Internet will not just involve doing old things while moving but, instead, it will involve people doing (inventing) all kinds of things that simply could not be done before.
i-mode: The mobile net and "smart mobs"
We are already familiar with mobile phones that have texting and, perhaps, camera imaging capacity. Texting--whether by mobile phone or two-way pager--has become widespread among young people across diverse social and economic groups. To date, outside of Japan, perhaps, full Internet wireless connectivity has not arrived on a scale close to that of phone texting. Nonetheless, "always on", large scale, full internet wireless connectivity is just around the corner. Rheingold refers to this as the coming of "the mobile Net". Much, if not most, of the world will experience the conjoining of mobile communications and the information processing power of networked computers during the current decade (2000-2010). In the very near future the number of mobile (wireless) devices connected to the Internet will surpass the number of internetworked personal computers.
Drawing on observations in leading edge telephony cities like Tokyo and Helsinki, and on trends he has tracked in North America, Britain and Western Europe, Rheingold argues that "the personal handheld device market is poised to take the kind of jump that the desktop PC made between 1980 and 1990" (xv). This is the jump from merely being "a useful toy adopted by a subculture to a disruptive technology that changes every aspect of society" (Rheingold 2003: xv). Today's mobile phones, says Rheingold, "have become tiny multimedia Internet terminals" (xiv), and the "infrastructure for global, wireless, Internet-based communication is entering the final stages of development" (xv). We are looking at the imminent convergence on a large scale of "portable, pervasive, location-sensitive intercommunication devices" that are useful to groups and individuals alike (ibid.).
In this context, "smart mob" behaviour will become increasingly prevalent and dominant within everyday life. Smart mobs are people who "cooperate in ways never before possible because they carry devices that possess both communication and computing capacities" (ibid.). Even though the individuals who constitute a smart mob may not actually know each other they are able to act together for shared purposes. The mobile devices that galvanise and mediate their efforts to act in concert are devices that "connect them with other information devices in the environment as well as with other people's telephones" (ibid.: xii).
The sheer pace of change within the realms of text production, distribution, and exchange make us extremely cautious about talking of "21st century literacies" in any comprehensive sense. We will try to deal here with some common examples of current phenomena that seem likely to influence social practices in more or less foreseeable ways over the next few years. These reflect various trends and tendencies that can already be differentiated from practices we have known in the recent past. Beyond such examples, however, we personally have little conception of what 21st century literacies might be, or turn out to be. Nonetheless, the phenomenon Rheingold refers to as "i-mode"--deriving from "Japan's singularly successful wireless Internet service" (ibid.: 3)--looks likely to impact our lives in massive ways during the years ahead, and is worthy of being made the focus of this paper.
Specifically, Rheingold's question about how human behaviour is likely to change when we hold in our hands (or otherwise "wear") gadgets with super computing power that communicate with each other through "a wireless mega-Internet" (ibid.) is timely, to say the least. Furthermore, it throws huge weight onto the issue about how literacy education within the formal curriculum can and should intersect with contemporary literacies in the world beyond the school. Pedagogy and curriculum cannot be "hostaged" to every change in cultural tools and uses that appears on the horizon. At the same time, as Thorne's case shows in miniature, if certain limits to learners' affinities, allegiances, identities and prior experience are transgressed, even "successful" learners (with the right cultural and social capital) will decline the offers made by formal education.
Changes in the making
Some early clues about the scale of behaviour changes likely to occur are provided in the anthropological studies of Japanese and Finnish adolescents' practices involving ubiquitous mobile telephony, and similar studies from other cultural contexts--such as ways in which electronic game playing in cities like Stockholm has morphed into literal chases through the physical landscape to shoot down electronic bots created and maintained in cyberspace. While, from some perspectives, these kinds of changes in social practices and their associated values may seem frivolous and trite, they are indicative of much larger and far-reaching possibilities, and often spill over into other domains of life, influencing changes in social practices there as well.
Mizuko Ito's studies of Tokyo youth using mobile phones to talk and text, trace how many young people "use the parts of the city between their schools and homes [where they may not have a lot of private space] as the stage for their alternative social space" (Rheingold 2002: 5). Ito has found that Japanese teenagers and twentysomethings "usually do not bother to set a time and place for their meetings. They exchange as many as 5 to 15 messages throughout the day that progressively narrow in on a time and place, two points eventually converging in a coordinated dance through the urban jungle" (2003: 2). In this way, they arrange to meet "on the run", turn shopping expeditions into contexts for group communications, and generally stay in touch with the members of their personal community (often 4 or 5 very close friends). As Ito explains, for young people in Japan "[t]o not have a keitai [mobile phone] is to be walking blind, disconnected from just-in-time information on where and when you are in the social networks of time and place" (Ito 2003: 2). In i-mode, time and place become fluid and flexible--negotiable on the fly: if you have a phone you can be late; much worse than being late is to forget your phone or allow the battery to die (Ito 2001, 2003; Rheingold 2002: 5).
In Finland, researchers report that a major feature in teenagers' text messaging "is the extent to which it incorporates collective behavior … text messages are circulated among friends, composed together, read together, and fitting expressions or entire messages are borrowed from others … Text messaging is a way to share relationships" (Kasasiniemi and Rautianen 2002, cited Rheingold 2002: 16) Earlier, Mäenpää and Kopomaa (Mäenpää 2001: 107-124) had observed that the kind of chatting and texting that goes on via mobile phoning has little to do with the exchange of real information, or even serious conversation. Instead, it has much more to do with just "sharing one's life with others in real time … living in the same rhythm or wave with one's closest friends [and] feeling … a continuously shared life … [the process of opening] another world of experience beside, or instead of, the one inhabited at the moment" (ibid., cited Rheingold 2002: 16-17).
Similarly, "Botfighting" emerged as a popular male cultural form among 12 - 30 year olds in Sweden during 2001. This madcap activity employs location detection capacities on phones that provide information on where other "phone-bearers" are. Players use the Botfighter website (www.botfighter.com), their credit card and laptops to create "bots" (in this case, small, animated characters) on the internet. They purchase arms and defence shields, as well as "battery power" for their bots. Rules are established on what counts as shooting down an opponent's bot, and are based largely on the physical proximity of players in meatspace. Teams of players decide to stay put at their computers, or set off by car, foot, subway, etc., with their phones on, trying to get within strike range of an opponent's phone. If they send a "got you" message before the opponent sends one, and if they have the right combinations of weapons and defences, they are credited with knocking out an opponent's bot. They can then send facetious or mocking phone text messages to celebrate the momentary win. Each hour or so a team will stop, eat, connect laptops to mobiles to check the state of health of their bots, to recharge their bots' "batteries" online, and carry on again--long into the night. Junk food, cars, phones, teamwork and sociality are combined in forming and operating cooperative "mobs".
Of course, "like every previous leap in technological power, the new convergence of wireless computation and social communication will enable people to improve life and liberty in some ways and to degrade it in others. The same technology has the potential to be used as both a weapon of social control and a means of resistance" (xviii). Smart mobs can cooperate to spy, surveill, intrude, and prey just as they can cooperate for sociality, harmless fun, to create business edge, to research, and so on.
Tendencies evident in the practices of "smart mobs" include:
Far from advocating and calling for uncritical adoption of what seems imminent, Rheingold points out we have a chance now to consider (potential) implications of a new technological regime before it reorders every aspect of social life. At the same time, however, Rheingold maintains that a new kind of digital divide ten years from now will separate those who know how to use the new media to band together from those who don't (2002: xix).
We are convinced that the trends, patterns, and tendencies Rheingold describes are fast becoming global (cf. Jones 2001, Plant 2001, Pritchard 2001). Our interest here is in possible educational responses to the kinds of trends and tendencies Rheingold describes. In particular, we are interested in how schools might build on what already exists and seems likely to further grow and evolve to promote progressive educational and social purposes.
Many and diverse social practices in which young people participate out of school on a daily basis partake of the logic described by Rheingold--even though many of these practices have originated prior to the degree of mobility--access that Rheingold speaks of being a reality. The evolution of social practices and new technologies is always a "both ways" rather than a "one way" affair. Hence, the development of mobile nets can be seen as responding to--every bit as much as "pushing" or "driving"--the tendencies toward cooperation, relationship, networking, affinity, pro-activity and enterprise emphasized by Rheingold.
Young people's out-of-school practices in developed countries are increasingly mediated by wearable, communication and information technologies. This in turns means that social practices for young people are becoming less and less "land locked" in the sense that they are always "plugged in" to the internet and/or other communication systems in ways that are highly portable, mobile and flexible. This has profound implications for schools in terms of decisions to be made about new technology investments for students, the integration of new technologies into classroom practices, professional development for teachers, and so on. We have used the terms "flogging" and "blogging" as referents for realms of literacy-mediated social practice in which we expect many young people to invest vast amounts of energy in their lives beyond school in the foreseeable future. We will describe aspects of these, beginning with flogging, as a platform for addressing our "so what?" questions with respect to curriculum and pedagogy.
Some aspects of "flogging"
I-mode has not developed within a vacuum, but builds on previous technologies and practices, and in turn, will continue to generate new technology innovations and social practices. For example, a video camera hookup to a coffee pot which regularly fed updated photographs to researchers' computers in a large, multi-storey building on the Cambridge University campus (U.S.) so that they could check the levels of coffee in the pot so that trips down long corridors and flights of stairs would always yield a fresh cup of coffee led to the explosion of webcams and live video streaming over the internet in the late 1990s. Research into wearable computers began in earnest in the early 1980s (cf., Gershenfeld 1999) and peer-to-peer interactions have always been a key aspect of the internet (Rheingold 1994, Rushkoff 1994). Mobile computing and communication takes these existing applications and in many ways turns them on their heads by freeing users up from landlocked home, school and workplace computers and enabling them to interact, associate and cooperate virtually and physically with friends and relative strangers on a more or less moment-by-moment basis. Rheingold argues that i-mode ways of operating lend themselves organically to mobilising mutually-beneficial collective action through affinity groups, online services, recommendation and reputation systems, and so on. Increasingly within i-mode, knowing who to trust will be a keystone in tapping into collective action. One telling example of the radical shift in ways of cooperating with others and organizing "mutual aid" currently underway is given by Rheingold, who describes the possibility of mobile device services that enable subscribers to log on, describe their route to work and ask, "Who is on my route and is looking for a ride in my direction right now--and who among them is recommended by my most trusted friends?" (2002: xx). Another example already in place is Friendster.com, a much-hyped match-making service whose organising principle is friends' recommendations of each other. The sign-on process asks the new user to invite as many friends as they want to join Friendster (who, in turn, invite friends of their own). Completing this list enables the new member to access each friend's own list of friends and to scroll through the profiles of each friend-of-a-friend in order to evaluate potential romantic possibilities. The new member then contacts each person he or she is interested in, explaining their friend-of-a-friend connection and implying a similarity of interests and a general trustworthiness (or, at the very least, opening up an avenue for verifying the new member's physical world reputation and integrity).
Rheingold defines "reputation" as the "histories each of us pull behind us that others routinely inspect to decide our value for everything from conversation partners to mortgage risks" (Rheingold 2002: xix). Reputation systems always have been a key element of social groups, spanning everything from dowry systems, to hosting community fiestas at great personal expense, through to medals, titles and awards systems, credit ratings systems, and so on. Online reputation systems in the form of publicly-accessible points, ratings and feedback are already in place and used by affiliates to evaluate everything from the trustworthiness of an online seller or buyer, through to judging whether or not to read a particular person's comments and postings in a discussion forum.
Flogging stuff and the usefulness of online reputation systems
eBay, the popular person-to-person online auction venue, owes much of its success to a relatively simple ratings and feedback system that assists members with making decisions about who to cooperate with in terms of buying and/or selling items. Thus, in terms of flogging--that is, selling--things online via eBay, one's reputation as a trustworthy buyer or seller (or both), and being able to "read" feedback properly when evaluating the fairness of the ratings an eBayer gives and receives are crucial elements of participating effectively within this online community.
eBay's reputation system involves a three point rating scale that serves as a public judgement of a person's trustworthiness and reliability. Once an auction transaction has been completed (the winning bidder has paid for and received the item) the buyer can leave feedback about the seller and vice versa by means of the item number. Only the buyer and seller are authorized to comment on a particular transaction. Feedback consists of the actual rating (positive, neutral, negative), and a written recommendation (up to 80 characters in length). eBay's website reminds eBayers that "[h]onest feedback shapes the community" (eBay 2002: 1) and eBay rarely intervenes in rating and feedback disputes--even when the rater admits to having made a mistake. The higher the positive ratings a person has, the more "reputable", "trustworthy" and "reliable" they are in eBay community terms. eBay ratings are summarised in the form of numerical tallies (i.e.., the number of positive, negative and neutral ratings awarded by unique others), as well as in terms of an overall percentage of positive ratings in relation to the volume of sales and purchases accrued by each user. Users are also able to access the ratings and feedback left by an eBayer for others (and not just the ratings and feedback they have received from others). Users are able to use this feature of the reputation system to evaluate a user's comments overall when he or she has left a negative comment for a seller from whom they planned to buy something. In short, the feedback received and the feedback left by a user can be scrutinised and judged to be trustworthy or otherwise in terms of online conduct, cooperation, and fair evaluations.
eBayers are very clear about the importance of their ratings. Many go to extraordinary lengths to obtain positive ratings. Some individual eBayers have constructed elaborate processes that aim at ensuring as many positive feedback statements and ratings as possible; this can include keeping track of who has and has not left feedback by means of meticulously kept spreadsheets, inserting "how to leave feedback" instructions inside the parcel sent to the winning bidder, and sending email reminders that feedback has not yet been left, among others.
The online eBay discussion board devoted to issues and questions concerning feedback practices and perceived injustices is always a lively space, with long-term eBayers offering advice or condolences to other users who demonstrate they have a genuine case of inappropriate negative or neutral feedback (see netgrrrl (12) and chicoboy26 (32) 2002 for more on this). A small-scale study of eBay social practices we conducted during 2000-2002 confirmed the importance of the reputation system for eBayers. Having even one negative feedback is perceived by the eBay community as bad for business. For example,
[Ratings] are extremely important. I don't want to buy from vendors with negative feedback, and I don't expect people to want to buy from me if I have any. Those comments are listed in red, and they show up like a neon sign!! (bea1997 email interview 25/09/2000).
Reputation ratings have actually become a "currency" for the eBay community, assuming the kind of role local community networks and character references have in physical space. One of our interviewees, susygirl, declares:
I really take pride in [my ratings]. […] And so I get pissed [off] if someone doesn't send me a positive feedback (email interview 1/02/2001).
Reciprocity in ratings is likewise important to arkanoid2020:
I have also had the problem of people not giving me a rating after a successful transaction, which is a shame because I always make the effort (email interview 12/02/2001).
Reciprocity between buyers and sellers is valued highly within the eBay community in relation to reputation building, and eBayers in general express their feelings about a lack of reciprocity very strongly (see Lankshear and Knobel 2003a: Ch. 6). For example, much of the eBay-based discussion about ratings is taken up with who should leave feedback and a rating first, and why. New terms have become common parlay within eBay discourse as well, and include words for describing practices such as "feedback hostage taking"--where the seller (or buyer) is held hostage to receiving feedback (i.e., "I'll leave you feedback only when you've left me feedback"), "retaliatory negative feedback", which describes someone giving a negative rating in response to receiving a negative rating regardless of the quality of the other person's conduct, or the word "neg" to refer to a negative rating which can take a noun or verb form (e.g., "I have a neg", "I've been negged").
Despite the importance of reciprocity and cooperation in leaving feedback following a transaction within the eBay community, one's overall rating remains paramount. Many eBay sellers, for example, have preferred to be "duped" by buyers rather than risk negative feedback. bea1997, a long-term and very experienced eBayer, explained to us,
Sometimes I lose money from customers who break an item and ask for their money back. I just don't want to risk having my good reputation ruined for a few lousy bucks so I just take the blame and send their money back (email interview 25/09/2000).
This tallies with others reported elsewhere. Erick Sherman (2001: 63) recounts:
Both buyers and sellers get burned from time to time, but usually not badly. Shamus remembers someone who bought a $25 trading card from him on eBay then returned it, but with a corner newly bent. "He said, 'That's what you sent me,'" says Shamus, who didn't argue because the amount was too small and negative feedback would hurt his future sales.
Interestingly, Rheingold reports figures that suggest fraud on eBay is relatively low with close to 99.9 percent of all Bay transactions being successfully completed--a much better rate than most shops can claim in terms of the ratio of completed sales to shoplifted goods (Rheingold 2002: 124; see also Powell 2003). This is not to say that eBay is an harmonious community--far from it in fact (see Lankshear and Knobel 2003a: Ch. 6). Pundits attribute eBay's relatively low fraud rates to the reputation system in place on eBay, where people are judged publicly on their ability to conduct themselves in trustworthy ways.
Flogging point of view, cooperation and reputations
A second form of online flogging whose robustness depends heavily on reputation systems concerns flogging--or promoting--opinions and point-of-view. Reputations in these contexts stand or fall on the quality of one's thinking and expression rather than on one's business conduct. Slashdot.com was the earliest discussion forum to make use of a peer-moderated ratings system to highlight comments worth close reading (and those not worth reading at all). Slashdot is an eclectic forum that mainly targets the computer geek community. It hosts discussions on computer programing, popular culture and news items. Each day, official Slashdot editors select relevant content and items reported on the internet and summarise each in a short blurb that includes a hyperlink to the entire story online. Slashdot members discuss each story by posting comments to the website (Rheingold 2002: 122). Each comment is rated on a scale of -1 to +5 by a revolving team of moderators selected from regular Slashdot readers. Slashdot members can then set their Slashdot interface filter to screen out comments that fall below a certain rating (e.g., the member chooses to read only those comments rated at 2 and above).
Targetting a wider audience, but using a reputation system strikingly similar to that used by Slashdot, is Plastic.com. Plastic began in January 2001, with the aim of being a "new model" of news delivery that turns "push media" news websites on their head by having members themselves propose content and comment publicly upon it: "Plastic's original contribution is a forum to discuss the diverse news pieces it promotes. At Plastic, readers' comments are what it's all about" (Barrett 2001: 1). Plasticians themselves tend to be self-styled members of an erudite, ironic and humorous "plugged in" crowd, interested in quirky takes on anything newsworthy--particularly anything connected with popular culture--as well as in serious and informed discussion of current events. Estimates place the number of regular Plastic users at around 15,000 (McKinnon 2001: 1).
Items for discussion are written up by users and can be posted to 8 topic categories: Etcetera, Film&TV, Games, Media, Music, Politics, Tech and Work. Those whose news items are accepted by Plastic's editors for posting and/or who post comments on the website are awarded ratings on two dimensions. One of these is "karma", which is used to rate a participant as an active member of the community relative to the number of newsworthy postings--both in terms of submitting stories and posting comments on stories--she or he has made to the site overall. A karma rating of 50 or over generally elevates the poster to (volunteer) submissions editor status.
The second dimension of the rating system--and linked directly to karma--is peer moderation that operates on a scale of -1 to +5 for a posting overall. Non-registered posters are allocated a default initial rating of "0" when they first post a comment, while the rating baseline for registered users is +1. Moderation points are awarded by Plastic's editors and by a changing group of registered Plastic members who have been randomly assigned a moderator role by Plastic's editors. Each moderator gets 10 moderating points to award to posted comments across all news items, and the possible ratings each moderator can allocate per comment are:
- Whatever 0
- Irrelevant -1
- Incoherent -1
- Obnoxious -1
- Astute+1
- Clever +1
- Informative +1
- Funny +1
- Genius +1
- Over-rated +1
- Under-rated +1
The moderation points awarded to each post are tallied and the final score is automatically updated and posted in the subject line of the message for readers to see. In other words, "if four or five moderators think a comment is brilliant, it may end up with a +5; useless comments are moderated down to a -1" (Plastic 2002a: 2). What is valued most by Plasticians is commentary that is written from a well-informed and concisely articulated point of view, and a member's Plastic reputation stands or falls on the quality of his or her contributions. Point of view becomes paramount within Plastic postings. That is, taking an informed, well-articulated position that draws on a careful reading of multiple sources, backing up one's position with embedded hyperlinks to online evidence that supports this position, and the like, are always highly rewarded ratings-wise.
Plastic's ranking system is based on formal recognition by the site that users cannot read everything that is posted on a topic. With a peer ranking system in place, users can set filters to screen out postings that fall outside a ranking range of their choice. For example, setting the filter threshold at +3 means only those comments that have been moderated and score at or above +3 will be displayed. Conversely, setting the filter threshold at -1 means every comment posted will be displayed. Plastic offers this ranking and filtering function as a means for helping users practise selective reading and to help enhance the quality of postings to the site. Thus, in many ways, Plastic's reputation system answers questions concerning whose comments to trust the most as being useful, clever, insightful and the like. There is also a keen element of plausibility or credibility associated with each Plastician's karma and comment rankings.
Despite some posters loudly and repeatedly protesting that they don't care about their overall karma, karma ratings--and the moderation system--are indeed "a new arithmetic of self-esteem" on Plastic (Shroedinger's Cat 2002: 1). At stake is public recognition of a poster's incisive mind, informed point of view, keen-edged humour, "innate hipness", and of being "plugged in" (Plastic 2002b: 1)--all of which can be judged on the run as it were using karma and comment ranking tallies in place of traditional character references and personal referrals.
Rating reputations
Both eBay and Plastic tend to attract members aged 18 years and older. However, there is sufficient anecdotal evidence to suggest that younger people are participating in these kinds of online communities (e.g., buying and selling on eBay-using their parents' accounts). Ratings systems are also very much in place and valued on collaborative computer troubleshooting websites, where the majority of troubleshooters appear to be in their mid-teens. When users subscribe, they are given a certain amount of free points that can allocate to a question they have concerning some computer problem they have--the higher the number of points they allocate, the more likely they are to attract troubleshooters' attention and have the problem solved. These points are then "won" by the person deemed to have solved the problem and added to his or her overall reputation ranking. In short, the higher the rank a troubleshooter has, the more he or she is recognised as being a "technology expert". Most online multiplayer games include formal and/or informal reputation systems that affect the extent to which people are prepared to cooperate with each other in completing quests, killing monsters, and the like (cf., Jakobsson and Taylor 2003). Many computer and video game related content websites make use of reputation systems as well, with contributors to the site ranked by peers according to the quality of the game-playing tip or "cheat" the contributor has shared, etc. We hazard a confident guess that participating in reputation systems already will be a familiar practice for many highschool aged youth and even younger students.
The increasing ubiquity of wireless access to social and cyber networks means online reputation ranks, ratings and feedback can only gain in importance as "character currency" in an i-mode world.
Key tendencies visible in this shift to collaborative peer assessment of one's character and trustworthiness include:
As more and more people come together in cooperative, yet distributed, collective action around popular causes (e.g., voting in government elections), affinity groups (e.g., tracking celebrities in New York City), and a range of social needs and services (e.g., offering a relative stranger a ride to work), they will need to rely more and more on being able to make character evaluations on the run. As Rheingold succinctly puts it, "[r]eputation marks the spot where technology and cooperation converge" (Rheingold 2002: 114). The often temporary nature of collective action--such as the short-term relationship between buyers and sellers on eBay, or between news item and comment posters and readers on Plastic--means there is little time for establishing trust via traditional methods that in the past have included observing someone's actions and interactions over time. Instead, other people's collective feedback on the quality of interaction with someone or the integrity or usefulness of a point of view espoused by a person will become the principal means by which to judge whether or not a person, or what they have to say, is trustworthy or not.
Rheingold points ahead to the emergence of distributed reputation systems that are used to form mobile ad-hoc communities on the run (what he refers to as "smart mobs"; p. 169). He predicts these communities will be similar in nature to groups of friends brought together after school by text-messaging and mobile phone calls to congregate in the one meeting place, but will be organised around interests (e.g., affinity groups), issues (e.g., voting, protesting), completing tasks collaboratively or reciprocally (e.g., dropping off a stranger's drycleaning while they return a book to the local library on your behalf; Rheingold 2002: 173), and the like. Invitations issued to join ad hoc groups will be governed by one's subscription to a group or collaborative service, by one's geographic proximity and online interest profile accessed by a group in the making, or by one's online reputation(s) (as a good person to do business with, as someone who is erudite and incisive, as someone trustworthy to share a car with, etc.).
This change in the way in which people (will) manage their online and offline social relations with strangers who are potential cooperative partners has important implications for schooling. At present most education administrators and policy makers appear concerned most with a "police and protect" approach to the internet (cf., Lankshear and Knobel 2002). This includes producing tailored and carefully screened and monitored online content for school students to use. It also includes putting in place mechanisms that constrain internet access. This includes imposing filtering and surveillance software on school networks, outlawing individual student email accounts, adding tracking software to internet browsers that keep tabs on websites visited by users, setting up firewalls that disable access to certain school sites from outside the school network, and so on (ibid.).
Of course, young children can be, and have been, vulnerable to online predators. Pop-up advertising on many popular types of websites aimed at young people, such as video-game related sites, is often explicitly sexual in nature and clearly lies outside the bounds of what is acceptable in school-related contexts. Some students do want to test the boundaries of what they can get away with at school by setting out to track down pornographic pictures, or how-to books on bomb making etc. However, in general, when it comes to interacting with others online it seems that schools seem to assume an inherent delinquency in students and tend to emphasize external measures of containment and "protection" rather than concentrating on equipping students with the wherewithal to make informed judgements concerning their online conduct and engagement with others. And, ironically, the advent of i-mode ways of using computing and communication technologies means that schools may well have to rethink their role in helping students to become responsible, trustworthy and "safe" network users and participants in a world where the dividing lines between the virtual, social and face-to-face are becoming increasingly blurred.
The growing need for young people to be able to critically and effectively read a person's reputation ratings and feedback requires serious school-based engagement with reputation systems and what they signify within different communities. At present, reputation systems tend to be community-specific, as is the case with eBay and Plastic. That is, the reputation rankings used by each community mean little outside these contexts. Students will need to be able to read and analyse different reputation systems and quickly ascertain the ontological focus of the ratings and ranks within each in order to make effective judgements concerning who to trust and why (e.g., Do they measure the trustworthiness of someone within business transactions? Do they measure the extent to which this person is endorsed by people I know and already trust? Do they measure the quality of ideas expressed by this person? And to what extent is this system useful to my immediate purposes?).
People interested in "being (thoroughly) digital" will need to know how to participate efficaciously in reputation systems as these systems become more and more integral to online and ad hoc i-mode communities. This will include tacit agreements to participate actively in the system, taking responsibility for leaving a rating score and feedback comment following each successful transaction or engagement, knowing when to cut one's losses in order to protect one's positive reputation scores, and so on. Perhaps most importantly, participating in a reputation system calls for knowing how to judge the credibility of feedback comments others leave about a person. For example, the eBay discussion board dedicated to feedback and ratings issues provides an excellent apprenticeship in how to evaluate the credibility of the person leaving feedback for others. As one example among many, participants in a discussion board have shown via links and comment tracking how a particular new member did not understand the eBay process properly and had left negative feedback for all of the transactions he had been involved in simply because the item he had bought had not arrived the next day. In this case, although the negative rating could not be erased, its sting was lessened and serious buyers would be unlikely to be deterred from bidding once they, too, had evaluated the (non)credibility of a negative rating given to a seller by this "newbie".
Being literate in reading reputation systems includes being alert to instances of reputation cheating and fraud. As another example, eBay users on the feedback discussion board have shown how a small group of eBayers has bid on and won each other's items numerous times and left glowing feedback and ratings for each other in order to boost the apparent robustness of their reputations (a practice known as "shilling", and outlawed on eBay; cf., Rheingold 2002: 127). As with any social innovation, the eBay reputation system has attracted any number of folk who have tried to cheat the system by, among other things, getting two or three friends to bid on one person's goods and then leaving only negative feedback regardless of the quality of the final transaction ("feedback bombing"), setting up two eBay accounts and using the second one to bid on one's own goods in order to leave positive feedback and comments under the first account ("feedback padding"), and so on (see netgrrrl (12) and chicoboy26 (32) 2002). Knowing that reputation systems can be manipulated, and in what ways, is just as important as knowing how to participate in, read and use reputation systems.
On the flipside, Rheingold reminds us that reputation systems can be used perniciously to surveill and control members of a group or community (2002: xxii). In response, young people would be well served by knowing to what is entailed in participating within each of the reputation systems they encounter and being able to judge to what extent they are willing to participate cooperatively within this system.
Blogging: Hive brains, back up brains, and point of view
Weblogs are another example of a truly new literacy which has emerged from online social practices. Weblogs--or "blogs" for short--have taken the internet by storm. Whether comprising a regularly updated list of hyperlinks and commentary or chronologically ordered journal entries, blogs are extensions of their owners' identities and mindsets, they celebrate point of view, and coalesce around affinity groups and the process of constructing a plausible presence online.
Blogging history
Weblogs began in the early 1990s as regularly updated websites that listed annotated hyperlinks to other websites containing interesting, curious, hilarious and/or generally newsworthy content located by the publisher of the weblog. These blogs generally are the result of wide-ranging online and offline research and often provide an alternative perspective on a topic or issue to that available in the mainstream media. Rebecca Blood--a popular and long-time weblogger--describes this use of weblogs in terms of skilled researchers filtering internet content in "smart, irreverent, and reliably interesting" ways (Blood 2002a: ix).
The release of online publishing tools and web hosting services, such as Pitas.com and Blogger.com, in 1999 made weblogging much more accessible to internet users not overly comfortable with working in hypertext markup language (HTML) to code and publish their own weblogs. While early blog publishers--generally known as "bloggers"--were largely from the tech world, this new generation of bloggers was much more diverse. Many began using weblogs as something more akin to regularly updated journals than to indices of hyperlinks. Entries in these weblogs document everything from what the blogger had for lunch that day; to movie and music reviews; descriptions of shopping trips; advice for bachelors; through to latest illustrations completed by the blogger for offline texts; and the like. Many weblogs now are hybrids of both types, or a mix of musings or anecdotes with embedded hyperlinks to related websites. Blood describes this new use of weblogs as one concerned with creating "social alliances" (Blood 2002a: x). These weblogs are largely personal interest-driven and attract readers who have (or would like to have) similar, if not the same, interests and affinities.
Recent estimates suggest there are now half a million active weblogs online, with some analysts claiming tens of thousands of new weblogs were launched around the world in 2002 (Manjoo 2002). At present, a weblog is best defined as "a website that is up-dated frequently, with new material posted at the top of the page" (Blood 2002b: 12). There are no hard and fast rules for weblogs. In general, each weblog entry is short and accompanied by the date (and sometimes the time) it was posted, in order to alert readers to the "currency" or "timeliness" of the log. Some bloggers choose to update several times a day, while others may update every few days or once a week or so.
Anatomy of a weblog
There are no hard and fast rules for what a weblog should look like; nevertheless, most weblog front pages are divided into at least two columns (see Figure 1). One column hosts each weblog posting, ordered chronologically from the most recent entry to the least recent entry with entries archived after a given period (e.g., a few days, a week, a month). The second column acts as an index of hyperlinks to the blogger's favourite, somehow related, or recommended websites and weblogs. This index is usually divided into sub-categories and generally runs along lines of interest. For example, Aaron Swartz--a popular teenage and long-term blogger--has organised his index of links into the following categories: quick links, more me (linking to additional websites published by Aaron), friends, art, news, and tech news.

Figure 1: Typical weblog layout (weblog.quartzcity.net)
Blog posts tend to be relatively short--in general, no more than a few lines to each post. There are basically two types of posts: those that include hyperlinks to other blogs or websites, and those that don't. Those posts that do include hyperlinks may begin with a link and post comments beneath it, in a form very similar to an annotated bibliographic entry. Hyperlinked posts may also include quotes from the information or text to which they are linking--in the manner of a "sound bite"--in order to give readers a sense of what they will find when they follow the link. Most blogs include a "comments" option at the end of each post, where readers can comment on the item linked to. This facility acts very much like the online message boards of old in that reader comments are listed one after the other, subsequently archived along with the post they pertain to, and can be read by anyone who clicks on the "comments" link
Typology of blogs
Part of our ongoing analysis of weblogs as new literacies has included drafting a preliminary typological map of weblog types (see Lankshear and Knobel 2003b). There are at least four popular categories of weblogs currently practiced online (see Figure 2). These include the two types discussed above--website hyperlinks with commentary and journals--along with those that comprise a hybrid between the two. The fourth type can be called "meta-blogs". These are weblogs about or concerning weblogs, and include hypertext indices of weblogs, weblog aggregators that calculate the most popular blog posts each day based on the number of links made to that post by others, and so on.

Figure 2: Four main categories of weblog types.
The basic taxonomy presented in Figure 2 breaks down into complex diversity to include a plethora of sub-categories. For example, the "links with commentary" category can be sub-divided into at least four sub-categories (see Figure 3), with sub-sub-categories discernible within each of these.
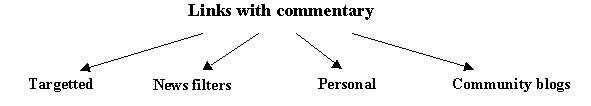
Figure 3: Four sub-categories of weblogs that comprise links with commentary.
Targetted weblogs of the links-with-commentary type have very clear audiences and a specific topic area that guide the selection of links to be posted and commented upon. Perhaps the most famous example of a targetted weblog is Dave Weiner's long running Scripting News (www.scripting.com). As its name suggests, Scripting News is chiefly concerned with keeping interested readers up-to-date with programming language, software and protocol developments in the tech world. His blog also includes some anecdotal snippets from his personal life and about his friends' online endeavours. This type of weblog is often a labour of love on the part of an expert in the area or field targetted by the blog. Maintaining targetted weblogs usually costs the publisher much in terms of time and energy--especially when the weblog is popular and requires regular and careful updating to keep readers satisfied--and the blog is offered more as a community service to interested others or to a relevant affinity group than anything else.
News filters are weblogs that are the product of wide-ranging research across the internet and physical space in order to construct, or to track down, perspectives on current events other than those offered by mainstream, commercial broadcast media. Blood explains the allure of this kind of weblog:
By highlighting articles that may easily be passed over by the typical Web user too busy to do more than scan corporate news sites, by searching out articles from lesser-known sources, and by providing additional facts, alternative views, and thoughtful commentary, weblog editors participate in the dissemination and interpretation of the news that is fed to us every day (Blood 2002b: 9).
In a May 2002 online archive of Wired, a writer for the New York Times, Andrew Sullivan, suggested that weblogs of the news filtering type are changing the media world. News filter weblogs transcend traditional broadcast media categories. They may be as "nuanced and well-sourced as traditional journalism" yet have "the immediacy of talk radio" (Sullivan 2002: 1). Sullivan goes so far as to suggest that blogging could "foment a revolution in the way journalism functions in our culture" (Sullivan 2002: 1). Sullivan's weblog--whose tagline reads, "The revolution will be blogged"--is an eclectic mix of annotated links to online reports, stories and commentaries on news events, homosexuality, religion and popular culture. Sullivan, whose blog reaches an estimated quarter of a million readers monthly and has become economically profitable, claims that Net Age readers are increasingly skeptical about the authority of big name media. Many readers know that the editors and writers of the most respected traditional news media are fallible and "no more inherently trustworthy than a lone blogger who has earned a reader's respect" (Sullivan 2002: 1). A key characteristic of news filter weblogs is that they invoke a viscerally personal touch, putting the character, temperament and point of view of the writer unapologetically out front rather than disguising it behind a façade of detached objectivity underwritten by the presumed editorial authority of the big formal newspaper or network.
Personal blogs tend to be the most idiosyncratic of the links-and-commentary type of weblogs. Their themes and content depend entirely on the publisher of the blog, although content patterns and preferences do tend to emerge over time. For example, Incoming Signals (www.wherethreadscomeloose.com/links.html) is heavy on links and well-crafted, albeit laconic, commentary. Incoming Signals is published by Christopher Bahn, a self-described "writer, editor, radio dramatist, DJ and chronic websurfer" (Bahn 2003: 1). The blog is updated a number of times a week and contains links to an eclectic mix of online artefacts, topics, events and trends. Recent blog postings have linked to a fully searchable online edition of The Proceedings of the Old Bailey London 1674-1834, an online gallery of A.C. Radebaugh's mid-century futurist illustrations, a dictionary of sailing terms for Viking ships and other ancient sea craft, an online Garfield random comic generator, and a panoramic view of the lost city of Petra. Personal, link-based blogs can also be informally collaborative, with regular readers forwarding hyperlinks they have come across that a particular publisher might be interested in blogging (i.e., posting on his or her blog). These kinds of contributions are often acknowledged by naming in the blog post the person who forwarded the link, which serves to enhance the sense of belonging to an affinity group when reading a blog that resonates with one's own personal interests.
Finally, community blogs are a relatively recent development within the blogosphere. They grew out of like-minded people wanting to work collaboratively on a weblog in order to include multiple voices and perspectives in their blog. Community blogs fall into roughly two categories: those that have a set list of people who can post to the blog, and those who allow just about anyone to post. The operating principle of community blogs is one of collaboration and cooperation and they aim deliberately at a "many to many" configuration. A pertinent example here is Howard Rheingold's Smartmobs collaborative weblog (www.smartmobs.com). While this blog was established as a deliberate extension of his book, Smart Mobs (2002), it has developed its own distinct weblog character thanks to the 11 formal contributing bloggers that form the core of this blog community. The blog is updated a number of times of day, with blog postings related to and organised around 10 key themes in the book, including: reputation systems, technologies of cooperation, and wireless network(ing) quilts, always-on surveillance issues and distributed computing networks. Recent posts include an update on always-on, sentient computer systems in workplaces, an update on a news delivery service that scans blog postings for items of interest and which includes a relevance and reputation system for judging relevance and quality, and news about a videorecording device that operates via a pair of glasses and hip-pack worn by the user, rather than via a traditional video camera.
Point of view and self-expression
Point of view is central to what blogging is about. A blog without point of view is almost a contradiction in terms (cf., Dibbell 2000). While most weblogs are collections of the curious, the bizarre and the groundbreaking in varying amounts, each one is inarguably an extension of the blogger. Reading a blog over time will reveal key elements of the blogger's interests, politics, theories (formal and informal), likes and dislikes, pet projects, habits, tastes in music, movies and literature, pastimes, and so on. The stances on issues, mindsets and "takes" on events offered by many blogs--even those most introspective and diary-like--offer readers a rich array of alternative, even competing, perspectives on the world from which they in turn can craft their own positions and opinions. For example, during the recent U.S. invasion of Iraq, reliable first-hand accounts of what was happening in Iraq could be had from a range of "warblogs" kept by independent journalists present in Iraq (e.g., kevinsites.com). In particular, a blog written by a young Iraqi university student--titled, "Where's Raed?"--sprang to prominence around the world due to his evocative and often heart-wrenching eye witness accounts of the capture of Baghdad. Although at the time writing anonymously due to media bans in Iraq at the time, the author of "Where's Raed?" managed at times to post to his weblog via a complex route that took him to servers outside Iraq, or by emailing his postings to a friend in New York for uploading to the blog site. His accounts were widely cited in the mainstream media itself, including in the BBC news and the New York Times. At the same time, other bloggers, like Andrew Sullivan and Glenn Reynolds of Instapundit.com for example, used their blogs to present a rabidly gung-ho pro-invasion point of view and provided alternative stances for a readers from a range of political persuasions to digest and ponder.
Point of view enables distributed affinity groups to form around a given weblog and across weblogs. Affinity groups are best described as a group that coalesces around shared interests, ways of thinking, interacting, valuing, believing, speaking and the like (Gee 2003: 27). For example, people interested in retrofuture accounts from the 1950s and 60s of what the 21st century would be like, regularly find useful hyperlinks to online retrofuture archives on BoingBoing (www.boingboing.net), A Joshua Tree in Every Pot (weblog.quartzcity.net), or Incoming Signals (www.wherethreadscomeloose.com/links.html). Similarly, readers interested in architecture and design might find themselves drawn regularly to Derek Powazek's weblog (www.powazek.com) or to archlog (archlog.editthispage.com). Blogs are also driven by purpose. Unless its creator has an authentic purpose--however whimsical this might be--a blog is unlikely to survive the demands on time, energy, resourcefulness, affiliation and other forms of identity work inherent in maintaining an enduring and effective blog.
In tandem with a well-presented point of view, high quality self-expression is paramount within the blogosphere as well. Advice to novice bloggers usually emphasises the need for good quality, accessible writing: "Readers [of weblogs] come from a variety of backgrounds. Write to the point, be simple and short. … Usually I spend a minute or two on a weblog to see if there is anything new and interesting. You probably have 30 to 45 seconds to get a user's attention" (Shanmugasundaram 2002: 143).
Matters of design and style--seen by the bloggerati as tightly interwoven--are also emphasised. The majority of bloggers themselves take the writing quality of blogs very seriously. The "Bloggies", for example, are annual awards that were established by Nikolai Nolan (www.fairvue.com/?feature=awards2003) in order to give due recognition to outstanding weblogs, or elements of weblogs. Key categories within the Bloggies include: "Best meme", "Best topical weblog", "Best article or essay about weblogs", and "Best tagline for a weblog".
Hive brains and back-up brains
Community blogs are sometimes referred to as "hive brains"; that is, they are a form of networked collective intelligence (cf., Levy 2001, Pritchard 2001) made possible through the collaborative efforts of the group participating in the construction and maintenance of the blog. Knowledge production as enactive projects are becoming more popular as online software interfaces become more user friendly and open to cooperative efforts (cf., the development of online collaborative wiki environments). And, increasingly, blogs are becoming internet touchstones for the i-mode generation, where mobile and distributed affinity groups use their wireless handheld computing devices to transmit text and images and, more recently, even sound and video to a community or personal blog. HipTop Nation (www.hiptop.bedope.com), for example, is a community blog open to the public and comprises in the main postings from members sent via wireless devices. Many of the posts include images of everyday life (e.g., friends sitting and having lunch, someone's toothlessly grinning baby) taken with mobile camera phones and emailed directly to the website via the phone itself. Although much of what is blogged on this website would fall into the trite and banal category, it nevertheless points ahead to the significant multimodal possibilities of blogging useful news and information on the run. Other bloggers are experimenting with streaming sound and video via wireless devices to their blogs, which holds important implications for "just in time and just in place" peer-to-peer or DIY journalism that may well scoop broadcast media time and again--especially when personal news event oriented blogs internetwork to form a hive brain repository for breaking news stories. A hive brain or "smart mob" approach to news reporting may well serve as an "always on" critique of mainstream broadcast media coverage of news events--indeed, media critiques already abound on community weblogs (see, for example, nyc.indymedia.org; and Lankshear and Knobel 2003b).
Individual blogs can also act as "audit trails" for one's personal research into a topic, issue or theme. By blogging internet websites related to one's research focus, and personal reflections on the topic or theme being pursued, it is possible at use weblogs as "back up brains" for storing important content, ideas and developments in the process of becoming more knowledgeable about something.
When Google bought Blogger.com in early 2003 some technorati speculated on the significance and smartness of this manouever. Matt Webb (2003) and Steve Johnson (2003) independently observed that search engines have become extremely efficient as means for obtaining information. They argued, however, that other than the blog there is no efficient digital tool for archiving and tracking information in ways that can narrate paths taken in the systematic exploration and development of a theme, topic or point of view and thereby reveal a structure of knowledge. Blogging lends itself to this kind of memory extension work in ways that produce useful audit trails of ideas that emerge and develop as one searches the internet for information on matters of personal interest.
Johnson argues that the acquisition of Blogger--perhaps the premier free blog publishing service available online--means that "[i]nstead of just helping you find new things, Google could help you keep track of what you've already found" by managing users' "surfing histories" (2003: 1). This augmentation of human memory recalls Vannevar Bush's conception of the "memex" in the mid 1940s (Bush 1945). Bush's memex machine comprised a desktop with inlaid screens and levers from which the user could access, among other things, the entire Encyclopedia Britannica, complete books, personal documents, and the like. According to Bush (1945: 1),
A memex is a device in which an individual stores all his books, records, and communications, and which is mechanized so that it may be consulted with exceeding speed and flexibility. It is an enlarged intimate supplement to his [or her] memory.
The memex resembles the modern computer--with one important difference. Bush emphasized the importance of being able to annotate texts accessed via the memex, which would effectively constitute a record of the path the user had taken through the information space and that these records or "trails" would be useful in "amplifying the signal of human memory" (Johnson 2003: 1).
Johnson suggests how Google's acquisition of Blogger could actualise the vision of the memex. It could mean that in the near future every time one conducts a search, each link clicked on is automatically "blogged" (that is, entered into a weblog and date stamped), "storing for posterity the text and location of the document" (ibid.: 2). Users could choose whether to make these blogged entries public and available for comment or not. Johnson also envisages Google generating a list of pages that link to the pages in one's blogged archive--making a useful, searchable subset of the internet that has been tailored specifically to meet the user's interests and information needs or wants.
Matt Webb (2003) describes the Google-Blogger process in terms of Google documenting what users see and what users do when searching via their service. In Webb's conception of the Google memex, Google searches would return information on information trails that were "well worn" or usefully uncommon, or would distinguish between trails people suggested and trails people actually followed when searching a similar or related topic, and so on.
In a similar kind of vein, Torill Mortensen and Jill Walker (2002) are currently documenting the development and use of blogs as academic research tools. Mortensen and Walker both conduct much of their own research online, and each began a weblog as a way of reminding themselves what their respective study focus was at the time. These weblogs, however, soon "developed beyond digital ethnographer's journals into a hybrid between journal, academic publishing, storage space for links and site for academic discourse" (250). Thus, blogs may well become important indices to and evidence of personal and collective knowledge structures by both recording and unveiling an individual's or a group's knowledge or epistemic effort over time.
Weblogs are in many ways instantiations of traditional practices associated with indexing and archiving information and documenting personal experiences, thoughts and ideas in meatspace. They are also uniquely digital in that without the internet they simply would not have developed. The expansive nature of weblogs also means they are highly adaptable, flexible and open to innovation and hybridizing. Key tendencies at present within the blogosphere include:
Backup brains for school
Given the epistemic potential of blogs, it is not difficult to imagine how blogging could become a potent dimension of school-based learning. This would require getting beyond the kinds of "pretend" research activities (classroom "projects") that typically prevail in school curriculum work, and beginning from significant problems that call for serious data collection and analysis. In such contexts blogging could be made into a highly sophisticated form of learning that engages directly with systematicity in searching for noteworthy or useful information. This would include being able to differentiate among types of data--such as well-used, quirky but useful, outdated, misleading, etc. Blogging as learning/Learning as blogging could also become an integral component of processes involved in developing point of view in relation to new topics, events and issues, of auditing this development in ways that are visible to the user and relevant others, and of generally pursuing meaningful purposes characteristic of expert-like research.
In relation to using new technologies effectively for informational and intellectual purposes, Chris Bigum (2002: 136) argues that what ultimately matters "is expertise, point of view, a place to stand from which to make sense of information." So far as formal learning contexts are concerned, this will at the very least involve learners and teachers beginning with authentic problems and questions to investigate (Beach and Bruce 2002). From such a starting point they will better be able to see the links between effective research strategies, social events and phenomena, and the process of becoming knowledgeable about something (cf., Lankshear and Snyder 2000).
Consequently, if school weblogs were approached from the standpoint of providing potential audit trails of knowledge built up over a period of time, they could contribute powerfully to promoting knowledge production, as well as enabling reflection upon and evaluation of how this knowledge was arrived at. A blog that records links, commentaries, and informed analysis, and that is open to being read by and commented upon by interested others, can become an objective artifact of collegial activity: one that is mediated by experts and learners in mutually beneficial ways. Blogs have much potential for promoting reflection on one's knowledge trails across the internet. Understanding where one went in an online search and why one went there thus becomes a key component of a blog, in ways that are not so evident and are not necessarily available in 5-part essay writing. Interested others could suggest to the blogger alternative trails or routes through a knowledge structure built around an interest in a particular topic, field or issue. This kind of engagement defaults to encouraging the blogger to regularly update and evaluate his or her point of view on a topic or issue when feedback or comments from others challenge the blogger to produce persuasive arguments, crisp analyses, and so on. At the same time, these interested others could also feed alternative angles and perspectives into the mix that can then be followed up on by the blogger. In these and other ways research as blogging, and blogging as research, could potentially become potent pedagogical approaches to writing.
So what for curriculum and pedagogy?
Having outlined what we see as some very significant trends and practices involving young people in their worlds beyond school, we turn now to the tricky questions we raised at the start of our paper about the extent to which formal pedagogy and curriculum should take account of these, how they might take account of them, and on what basis (which principles, what criteria, etc) the decisions should be made. Some things seem reasonably clear from the outset.
To advance our argument we need to identify some educationally appropriate principles and criteria on which to base judgments and decisions. These must reflect the status of formal education as ethically informed practice--such that education does not become simply a reflex of the values and interests of the most powerful social groups--while simultaneously holding education accountable to a society's legitimate claims upon it. The entire history of educational thought is, of course, nothing less than the collective record of the search for such principles and criteria. So we won't pretend to resolve the matter here! On the other hand, several educational principles and related criteria derived from a sociocultural perspective and to which we are committed seem especially relevant to our concerns here. Four stand out in particular. These are
We will describe these briefly in turn.
The principle of efficacious learning
According to this principle, for learning to be efficacious it is necessary that what somebody learns now is connected in meaningful and motivating ways to mature or insider versions of Discourses. Discourses are understood as sets of related social practices composed of particular ways of using language, acting and interacting, believing, valuing, gesturing, using tools and other artifacts within certain (appropriate) contexts such that one enacts or recognises a particular social identity or way of doing and being in the world (Gee, Hull and Lankshear 1996: 4). This involves thinking of education and learning in terms not of schools and children (place-related and age specific) but, instead, in terms of human lives as trajectories through diverse social practices and institutions (ibid.). To learn something is to progress toward a fuller understanding and fluency with doing and being in ways that are recognised as proficient relative to socially constructed and maintained (proper) ways of "being in the world". Participating in Discourses are things we get more or less right or more or less wrong. Mature or insider forms of Discourses are, so to speak, "the real thing": the way a Discourse is "done" by "mature users" who "get it right". They are "authentic" rather than "pretend" versions of the social practices in questions. In this sense, for learning at times to be efficacious it must involve doing something that genuinely puts the learner on the right track toward becoming a competent participant in "the real thing"--whatever the Discourse in question might be.
The principle of integrated learning
From a sociocultural perspective, learning is integrated to the extent that three conditions are met. These all relate to the key idea that learning is inseparable from Discourses.
The first condition is that integrated learning occurs inside a practice rather than at a distance (as where one learns something about a practice at remove from participation in the practice itself, with a view to applying the learning in situ at some subsequent time). This is not to say that worthwhile learning cannot be decontextualised and subsequently applied; only that to this extent the learning is not integrated in the sense intended here.
The second condition extends the first. Learning is integrated when the various "bits" of social practices that go together to make up a practice as a whole--and where the various "bits" of related social practices that go together to make up a Discourse as a whole--are learned in their relationships to one another, as a consequence of learning them inside the practice(s). In integrated learning we learn to put the various "bits" (the speaking bits, tool and artefact--using bits, action/behaviour bits, valuing and believing and gesturing and dressing, etc., bits) "whole" and "live". We learn them organically in their relationships to each other, not as "chunks" to be articulated later.
The third condition is that our learning is the more integrated the less it clashes with who and what we are and do in the other discursive dimensions of our lives. The less the "identity" we are called to be in this learning instance is in conflict with the identities we are called to be--and are at home with--in the rest of our lives, the more integrated the learning can be. Thorne's example of Grace is apposite here. Trying to get Grace to learn conversational-friendship French by means of email could not be integrated in this sense. Grace was, in effect, being asked to "mean against" some of her other social identities and values that were important to her. Other things being equal, the less conflict learners experience with their other social identities, the more effectively and willingly they learn.
The principle of productive appropriation and extension in learning
This principle is partly an extension of the integrated learning principle, and partly the time-honoured principle that learning should build on what learners already know and have experienced. With respect to the first aspect, this principle involves looking for ways to reduce or ameliorate conflict between social identities during learning. For example, if an educationally acceptable appropriation of Grace's cultural construction of age-peer/friendship communication (e.g., via IM) could be made within the French course, this would help integrate and strengthen learning by putting cultural, personal, technological, and epistemological aspects in sync.
With respect to the second aspect, if learners already know how to perform discursive roles and tasks that can legitimately be carried over into new discursive spaces, this can be used to advantage to enable learning and proficiency in a new area. For example, knowing how to archive downloaded music onto an MP3 player like an iPod for personal entertainment purposes can readily be transferred to archiving interview data that has been recorded digitally for research purposes, without compromising either practice. The kinds of clash between cultures of use evident in the example of Grace are not likely to arise in this case. Of course, this aspect of the present principle-building learning on, and integrating into present learning, relevant knowledge and competence the learner already has--is practically self-evident. It is certainly widely recognized by educators. At the same time, it is systematically ignored or subverted on a massive scale within classroom learning.
The principle of critical learning
In various places, Jim Gee (1996; Gee, Hull and Lankshear 1996) states very clearly a major dilemma with respect to effective learning construed socioculturally as processes of achieving fluent mastery of Discourses. This concerns the fact that becoming fluent in a Discourse is best achieved through processes of learning inside the Discourse. But the more effective this learning is, the less critically reflective the learner's perspective on the Discourse will be. The more effective learning inside a Discourse is, the more deeply "indoctrinatory" it is likely to be. As Gee notes, Discourses cannot countenance criticism from within, since that would be to invite their own demise or transcendence.
This is problematic if we believe education should help prepare learners to understand the limitations and constitutive nature of each and every Discourse, and to be committed to and capable of playing active roles in trying to shape social practices in progressive and expansive ways on the basis of what they believe and value. From this standpoint it is necessary to create spaces for developing and negotiating differing points of view on social practices, social identities, social institutions, and the like. This means creating spaces for experiencing different and competing Discourses and deciding how to handle this divergence.
Toward criteria for decision making
These principles suggest a number of criteria for helping us decide on the extent to which and manner in which characteristically contemporary literacies--comprising technologies, artifacts, practices, and cultures of use--engaged by young people beyond the school might become integral components of school-based learning in ways that strengthen education. These include (but are not exhausted by) criteria like their conduciveness to "promoting approximations to expert practice", "authentic/non contrived uses", "collaborative activity", "recognition of distributed knowledge and expertise", "efficacy for in situ use", "capacity to mediate whole practices", and so on. If some of these criteria are not immediately apparent as derivations from our principles, the links become readily apparent when we acknowledge that Discourses are distributed networks of knowledge, expertise, competence and so on. Without collaboration and expertise there can be no Discourses, and without Discourses there can be no learning.
This brings us to a crucial point in the argument we are trying to develop, which concerns the purposes of school-based learning and participation in school-based Discourses and the relationship between school-based learning and participation in the "mature" Discourses to which the school Discourses are presumed to relate. Apart from when it is a senseless activity, learning is always "a process of entry into and participation in a Discourse" (Gee, Hull and Lankshear 1996: 15). School learning certainly involves entry into school Discourses, but the further question is: "To what end?" If school learning is simply for initiation into school Discourses, that is one thing, and we are left without a significant problem here--since there is no reason why school learning should have to take account of non-school practices.
If, on the other hand, we believe that school-based Discourses of learning (school projects, school history, school science, physical education, etc.) should contract significant relationships to "mature" Discourses beyond the school, we have an issue of major proportions. This is because schools "separate learning from participation in "mature Discourses" and, moreover, "render the connection entirely mysterious" (ibid.). Hence, our immediate questions about whether and how aspects of practices like "flogging", "blogging", "text messaging", and generally being in "i-mode" can, with integrity, be taken into account in school-based learning becomes a subset of a much larger and more fundamental question.
In the remainder of this paper we will take the view that school Discourses of learning can and should relate transparently and efficaciously to learners' lives as trajectories through diverse social practices in myriad social institutions and, therefore, should relate to "mature" or "insider" versions of Discourses.
A digression
While there is not space to address it in any detail here, we want nonetheless to raise a possibility for consideration. This is that there are good grounds at present for thinking that school Discourses of learning are currently being reconstituted to a large extent around purposes besides school learning for participation in school Discourses or for participation in "mature" versions of Discourses beyond the school. These other purposes include what Lyotard (1984) calls "performativity" and for purposes of managing young people's time and energies. Neither of these, of course, is a novel suggestion. But we think it is timely and important to take these suggestions very seriously.
Elsewhere (Lankshear and Knobel 2002, 2003) we have discussed what we see as a sociotechnological monstrosity in the form of Britain's National Grid for Learning (recently renamed as the ICT in learning initiative (or some such). On the one hand, when harnessed to the British system of "Standards for Education" via endless homework on line or online literacy activities that mesh neatly with constructions like the Literacy Hour, the Grid becomes part of the state's performativity web. Everything "educational" becomes "measurable", "reportable", and "accountable" under the sign of "efficiency". To this extent, schooling serves the longevity of politicians and state bureaucrats by enabling them to shower statistics on their political constituencies to show how things have "improved" in education.
Conjointly, when we focus on the paranoid concern of the Grid for its particular construction of "security" and "safety on the information superhighway" it is easy to read the Grid as a ham-fisted attempt to manage kids' online behaviour--not least, by preying on the ignorance and susceptibility of parents and other caregivers with respect to internet environments. The Grid would pretend to extend school-style surveillance and management of bodies into the spaces of home computing. We see it as doing this in the interests of purposes that at their worst are profoundly anti-educational in any expansive sense and, at the very least, are inimical to participation in "mature" versions of constructive and productive social practices involving new computing and communication technologies.
Knowledge producing schools: a grassroots initiative on the side of education
In looking for clues as to how school-based learning might take educational account of the kinds of examples we have described in the core of this paper we find some exciting possibilities inherent in a new initiative being developed in Australia (Bigum 2002, 2003, Lankshear and Knobel 2003a: Ch 8). The initiative began from work by Chris Bigum with principals, teachers and students in a small number of schools in regional and remote parts of Queensland. The protagonists shared an interest in two related questions. One was how learning might become more about producing rather than consuming knowledge (and, to this extent, more connected to the everyday lives of school communities). The other was how to deschool classroom uses of new technologies--to move away from trying to find things for CCTs to do within the established routines and ways of classroom learning.
A key premise underlying the development of knowledge producing schools (KPS) is that school uses of CCTs are based on a mindset that understands new technologies in terms of information (Bigum 2002, Schrage 2000). Bigum (2003) notes that the many changes associated with CCTs that we have witnessed in such spheres as business, entertainment and commerce have been described as a result of "the information revolution". However, as Michael Schrage (2000) suggests,
this is a dangerously myopic lens with which to view these changes. He argues, for instance that to "say that the Internet is about 'information' is a bit like saying that 'cooking' is about oven temperatures; it's technically accurate but fundamentally untrue.' Schrage goes on to argue that "the biggest impact these technologies have had, and will have, is on relationships between people and between organizations". Seeing CCTs in terms of a relationship revolution is perhaps not as catchy some of the other descriptions in common use but it provides a way of thinking about CCTs in schools that opens up some useful possibilities (Bigum 2003: 5).
From this standpoint, schools can consider how CCTs might be used productively in terms of new relationships that could be developed and mediated using these technologies, rather than in terms of information delivery or of doing old things in new ways. The model of KPS builds on the idea that, as knowledge producers in a new and significant sense, schools can develop and consolidate new kinds of relationships within and without the school.
The concept of knowledge producers/production in question here needs clarifying. There is a sense in which students have always been involved in producing knowledge within the classroom. But this is almost always an artificial, "pretend", non expert-like production of "knowledge". It is dominated by what Bigum calls a "fridge door" mindset for student work--the idea that the teacher sets a task, students complete it, the teacher assesses it, and the student takes it home where it might be "published" temporarily on the fridge door. There is no real problem, no real demand, no real need, no real knowledge product.
The KPS model actively tries to move beyond the fridge door approach. The schools in question have begun to develop new and interesting relationships with groups in their local communities, by engaging in processes that generate products or performances that are valued by the constituencies for which they have been produced. An important part of negotiating the production of such knowledge is that the product or performance is something that students see as being valued by the consumer or audience of their work. The students know their work is taken seriously, and that it has to be good or else it will not be acceptable to those who have commissioned it. The level of engagement and the quality of work and student learnings to date have been routinely impressive. These are not teacher projects with peripheral student involvement. Rather, they are projects--in the sense in which developing and producing commercial movies or motor cars are described as projects--that are given to students as problems to solve or, as has frequently been the case, problems the students have raised with a view to solving them.
The following examples are typical.
It is important to briefly note four points here.
First, these examples come from the primary school level. The KPS initiative involves learners from their first year at school onwards to Year 7. Obviously, engaging in knowledge production with such young learners would be extremely difficult if it rested primarily on written language. Accordingly, the schools from which our examples are drawn have established practices of "writing with cameras"--recording digital visual images, still and video--alongside formal initiation into print literacy. They have invested very modestly in CCTs, with no more than two or three computers per class and a small central facility that supports image editing. Students routinely employ digital cameras to do their work.
Second, the strategy of writing with cameras has in a short time (12 months) led to the development of a broad base of expertise among teachers and students around preparing audiovisual presentations, usually stored on CD-ROM or VHS tape. This is not, however, expertise devoted to using digital imaging equipment per se. The CCTs are not the focus or purpose of the work. They are media that play useful roles in supporting student work that has genuine value to outside groups and audiences. According to Bigum (ibid.), the fact that the CCTs provide learners with an additional mode of expression has been a pivotal factor in the success of most of the projects (and not all projects employ CCTs).
Third, the KPS approach is based on a view of education as a "whole of community responsibility". It contracts deep and committed relationships between the schools and their communities. These relationships go multiple ways. It is not simply a matter of community groups having the role of being the source of problems and demand for projects. On the contrary, the community provides an essential source of relevant expertise: the expertise that is needed for the student work to approximate to proficient performance in "mature" Discourses. The beef industry does not want a "pretend documentary". It has to be good or it will be rejected. There is no space for patronising here. In fact, the entrée to digital visual media work in one of the schools came via a student teacher with a sibling who was employed in digital video production and who provided free expertise. As Bigum puts it:
Not only has community become a source of problems on which to work but also students access specialist communities for support in working on some of their projects. As Moore and Young (2001: 459) recently suggest, there are now strong grounds for "reorienting debates about standards and knowledge in the curriculum from attempts to specify learning outcomes and extend testing to the role of specialist communities, networks and codes of practice" (2003: 7).
Finally, there is a sense in which many of the components of these examples, taken individually, are not new. Neither is there anything especially remarkable about the projects. The novelty of KPS is that "all of these elements are drawn together under a new logic: that of schools as producers of knowledge as sites where serious knowledge production and research can occur" (ibid.). The invitation here is "instead of thinking of a school as a place where 300 young people attend to be provided with an education, try to think about a school as a research site populated with 300 … researchers" (ibid.: n10).
Some vignettes of non-contrived possibility: mobile, cooperative, contemporary, expert knowledge production
This account of the KPS initiative provides a springboard from which the following kinds of vignettes are but a short and plausible jump.
I
Soloranzo High School has assembled a research team of students drawn from History, English, and Social Science subjects across grade levels 8 to 12. The team is working in collaboration with three History professors at a local university. The project, commissioned by the municipal council, is to develop an oral history of long established migrant groups within the city. It involves conducting life history interviews with elderly residents, focusing on their experiences of settling in their adopted country.
Ben (Year 8) and Monica (Year 11) meet at McDonalds to go over their interview questions. Their information about the couple that they are to interview has given rise to doubts about two of their proposed questions. Unsure what to do, they call their university research partner on Monica's mobile phone and ask her advice. They talk for five minutes and revise the interview schedule accordingly. The university professor tells them she will be in her office the next 2 hours and asks them to call her back when they reach that part of the interview. When they arrive at the house Monica text messages the teacher coordinating the project to confirm that they have arrived and everything is ready for the interview.
Ben takes the digital voice recorder from his pocket and gets it ready for recording. The recorder has a built-in camera that Ben will use throughout the semi-structured interview, having obtained the necessary formal consent from the couple. On this occasion Monica will play the main interviewing role, although both will prompt and probe when appropriate as the professor has coached them to do. They call the professor at the arranged point in the interview. She talks with the couple by means of the loudspeaker function built into the mobile phone, recording the conversation at her end, while Ben continues recording the conversation in situ. When the professor has finished, Monica and Ben conclude the interview, thank the couple, negotiate a follow up if needed, and leave.
They have one hour before their next interview, so they go to a nearby public library they know has wireless internet access. Ben uploads the digital audio and visual file from the voice recorder to the small Apple notebook on loan to them from the university. When the upload is complete Monica logs on and FTPs the file to the project website for archiving. Ben simultaneously logs on using a PDA from the school set and posts a short message to the team blog, notifying that the interview has been completed and the files uploaded. He also lists the artifacts shared by the couple during the interview and records the professor's participation during the interview.
When they have finished, they text message their teacher again and set off for the next interview.
II
Karl (Year 10) oversees Soloranzo High School's project reputation system and maintains a registry of community expertise that has been made available to project teams. He and a group of peers researched a range of well-known formal rating systems (eBay, Amazon.com, Plastic.com) and developed a five point rating scale and a component for brief feedback statements. At the completion of each project Karl and his teammates email the clients, providing a brief explanation of the rating and feedback system, a reference number, and politely inviting them to log their evaluation on the automated form on the school's project website. (Karl's team developed this form in collaboration with some undergraduate university students in computer engineering.) The clients enter their project reference number into the form (feedback cannot be left without this number), select a rating from a drop down menu, and provide up to 50 words of descriptive feedback in the text window. Karl then updates the project reputation web page, which is public.
These ratings provide the formal public record of the school's level of performance as assessed by clients, as well as evaluative data on individual projects that contribute to team members' assessment portfolios. This public record of reputation is an integral part of the process by which the community develops a new perception of the nature and role of contemporary school education. Karl's school recognises that to function effectively as a KPS it (and other KPSs) needs to be "at least partially remade in the minds of the local community", and that "project by project it [is] possible to build up a repertoire of [publicly recognised] research skills and products in consultation with local needs and interests" (Bigum 2002: 139).
Karl also maintains a registry of community expertise that has been made available to the school in its project work. This registry is public and serves multiple purposes. In part it is a record of resources that might be available to the school and/or other (non-profit) community groups for appropriate future activities. It is also a mechanism for community networking. In addition, and very importantly, it provides a public statement of the community service/collaborative-cooperative dispositions of those who have demonstrated their recognition that education is a whole of community responsibility. Of course, the record of projects on the school website simultaneously identifies those community groups and organisations that have supported the reconstitution of education as "mature" knowledge production by commissioning projects.
III
At Soloranzo High the research teams have each been assigned server space for project blogs and websites. Sarah (Year 10) is "responsible" for the oral history project blog. This blog works in tandem with the project's archival web site (for which Sarah is also responsible). The blog is used to document the team's research process as it unfolds. As we have seen, student interviewers in the field can use the blog to update their teammates in real time (e.g., by PDA from a wireless hotspot).
Sarah has general oversight of the blog, although all team members are registered and can post to it. Sarah follows up on comments, organises the structure of the blog, edits spelling, maintains the URL lists, and generally performs the kinds of tasks undertaken by webmasters. The blog serves as an audit trail for the project and as a repository of the team's thinking over time. For example, team members blog ideas about patterns they are starting to see in the data, post links to online resources relevant to an aspect of the study, and list brief summaries, citations, and location details of relevant offline resources (books, newspaper articles, artifacts in people's homes) etc. The blog also accommodates ideas, information and suggestions (e.g., things to follow up on, other people to interview, locations of documents and artifacts) relevant to the study posted by members of the public at large.
The website is a password-protected database containing all digital archival material generated in the project. It can be accessed by all team members for the various research purposes from any location with internet access. These purposes include uploading new data, keeping tabs on what has already been collected (and not), to prepare data for analysis and printing out data to be analysed, and generally maintaining a record of progress to date. It is not only the main digital database for the project, but also a potential future source of secondary data for subsequent projects upon approval subject to ethical consideration. Sarah maintains this website, in collaboration with her counterpart in the university and her History teacher (who is the staff member assigned to this project).
Concluding remarks
These vignettes are by no means farfetched. At the same time, they show how a range of characteristically contemporary CCTs and out of school social practices and cultures of use can be incorporated into learning on terms that satisfy the kinds of principles and criteria identified above.
References
Anderson, C. (2003). Wi-Fi revolution. Unwired: Special Wired Report. New York: Conde Nast. 6-19.
Bahn, C. (2003). About this blog. www.wherethreadscomeloose.com/linksarchive.html#About (accessed 27 June 2003).
Barrett, A. (2001) Plastic.com Invites Visitors to Shape the Site. PCWorld.com. Monday, 22 January. www.pcworld.com/news/article/0,aid,39013,00.asp (accessed 10 February 2002).
Bigum, C. (2002). Design sensibilities, schools, and the new computing and communications technologies, in I. Snyder (Ed.), Silicon Literacies. London: Falmer-Routledge.
Bigum, C. (2003). Knowledge producing schools. Geelong: Deakin University. Mimeo
Boglet (2003). Many to Many: Group Voice. Tuesday, 3 June. Email newsletter. Received from www.corante.com/many (3 June 2003).
Blood, R. (2002a). Introduction. In Editors of Perseus Publishing (Ed.). We've Got Blog: How Weblogs are Changing Culture. Cambridge, MA: Perseus Publishing. ix-xiii.
Blood, R. (2002b). Weblogs: A history and perspective. In Editors of Perseus Publishing (Ed.). We've Got Blog: How Weblogs are Changing Culture. Cambridge, MA: Perseus Publishing. 7-16.
Bush, V. (1945). As we may think. Atlantic Monthly. July. www.theatlantic.com/unbound/flashbks/computer/bushf.htm (accessed 19 April, 2003).
Dibbell, J. (2000). Portrait of the blogger as a young man. In Editors of Perseus Publishing (Ed.). We've Got Blog: How Weblogs are Changing Culture. Cambridge, MA: Perseus Publishing. 69-77.
Doctorow, C. (2001). My blog, my outboard brain. Blogged 31 May 2002. www.oreillynet.com/pub/a/javascript/2002/01/01/cory.html (accessed 27 June 2003).
eBay (2002) Frequently Asked Questions about Feedback. pages.ebay.com/help/basics/f-feedback.html (accessed 10 Feb. 2002).
Gee, J. (2003). What Video Games Have to Teach Us About Learning and Literacy. New York: Palgrave.
Gee, J. P., Hull, G. and Lankshear, C. (1996). The New Work Order: Behind the Language of the New Capitalism. Sydney: Allen and Unwin.
Gershenfeld, N. (1999). When Things Start to Think. New York: Henry Holt and Company.
Heim, M. (1999). Transmogrifications. www.mheim.com/html/transmog/transmog.htm (accessed 21 January 2001).
Ito, M. (2003). A new set of social rules for a newly wireless society. Japan Media Review. March 13. 1-4. www.ojr.org/japan/wireless/1043770650.php (accessed 14 March, 2003).
Jakobsson, M. and Taylor, T. (2003). The Sopranos Meets EverQuest Social Networking in Massively Multiplayer Online Games. MelbourneDAC2003. 81-90.
Johnson, S. (2003). Google's memory upgrade. Slate. 6 March. slate.msn.com/id/2079747 (access 19 April 2003).
Jones, R. (2001). Beyond the screen: A participatory study of computer-mediated communication among Hong Kong youth. Paper presented to the American Anthropological Association Annual Meeting. 12 November-2 December.
Lankshear, C. and Knobel, M. (2002). Young Children and the National Grid for Learning. Journal of Early Childhood Literacy. 2(2): 167-194.
Lankshear, C. and Knobel, M. (2003a). New Literacies: Changing Knowledge and Classroom Learning. Buckingham: Open University Press.
Lankshear, C. and Knobel, M. (2003b). Do-It-Yourself Broadcasting: Writing Weblogs in a Knowledge Society. Symposium paper presented to that American Educational Research Association Annual Conference, Chicago. 21 April.
Lankshear, C., Peters, M. and Knobel, M. (2000). Information, knowledge and learning: Some issues facing epistemology and education in a digital age. In N. Blake and P. Standish (Eds.), Enquiries at the Interface: Philosophical Problems of Online Education. Oxford: Blackwell. 19-44.
Lévy, P. (2001). Meta evolution. Unpublished manuscript. www.mit.edu/~fca/levy/meta_evolution.html (accessed 6 June, 2003).
Lyotard, J-F. (1984) The Postmodern Condition: A Report on Knowledge. Trans. Geoff Bennington and Brian Massumi. Minneapolis: University of Minnesota Press.
McKinnon, M. (2001). One Plastic Day. Shift Magazine. 9(4): 1-3. www.shift.com/toc/9.4 (accessed 10 Feb. 2002).
Manjoo, F. (2002). Blah, blah, blah and blog. Wired. 18 February. www.wired.com/news/culure/0,1284,508443,00.html (accessed 19 April 2003).
Mortenson, T. and Walker, J. (2002). Blogging thoughts: Personal publication as an online research tool. In A. Morrison (Ed.), Researching ICTs in Context. Oslo: Intermedia Report. 249-279.
netgrrrl (12) and chicoboy26 (32) (2002). What am I bid?: Reading, writing and ratings and eBay.com. In I. Snyder (Ed.) Silicon Literacies. London: Routledge-Falmer. 15-30.
Plant, S. (2001). On the Mobile: The Effects of Mobile Telephones on Social and Individual Life. Report prepared for Motorola. www.motorola.com/mot/documents/0,,296,00.pdf (accessed 27 June 2003).
Plastic (2002a). Guide to Moderating Comments at Plastic. Plastic. www.plastic.com/moderation.shtml (accessed 13 February 2002).
Plastic (2002b) www.plastic.com (accessed 21 March 2002).
Powell, A. (2003). Putting a dollar value on a good name. Harvard Gazette Archives. www.news.harvard.edu/gazette/2003/02.27/17-ebay.html (access 27 June 2003).
Pritchard, R. (2001) "I never leave home without it": Personal Information appliances, virtual learning communities, and the global cyborgian educational appliance. In J. Suoranta, M. Ylä-Kotola, M. and S. Inkinen (Eds.) The Integrated Media Machine, Vol. 2. Hämeenlinna: Edita & University of Lapland. 59-68.
Rheingold, H. (1993). The Virtual Community: Homesteading on the Electronic Frontier. Reading, MA: Addison-Wesley.
Rheingold, H. (2002). Smart Mobs: The Next Social Revolution. Cambridge, MA: Perseus.
Rushkoff, D. (1994) Cyberia. Life in the Trenches of Hyperspace. San Francisco: HarperSanFrancisco.
Schroedinger's Cat (2002) First Plastiversary-Happy Birthday, Plastic! Plastic. plastic.com/article.pl?sid=02/01/09/0235209&mode=thread&threshold=0 (accessed 15 Jan. 2002).
Shanmugasundaram, K. (2002). Weblogging: Lessons learned. In Editors of Perseus Publishing (Ed.). We've Got Blog: How Weblogs are Changing Culture. Cambridge, MA: Perseus Publishing. 142-144.
Sherman, E. (2001) The World's Largest Yard Sale: Online auctions: The sale of collectibles is migrating to the Web. It's the place where niche buyers meet niche sellers. Newsweek. March 19. 62-4.
Sullivan, A. (2002). The blogging revolution. Wired. May. 10.05. www.wired.com/wired/archive/10.05/mustread.html?pg=2 (accessed 20 Apr. 2002).
Spector, R. (2000). Amazon.com: Get Big Fast. San Francisco, CA: Harper Business.
Thorne, S. (2003). The Internet as Artifact: Immediacy, Evolution, and Educational Contingencies, or " The Wrong Tool for the Right Job?" Paper Presented to the American Educational Research Association Annual Meeting, Chicago, Il. April 21.
Webb, M. (2003). Google buy Pyra 2. interconnect.org. February. interconnect.org/notes/2003/02/Google_buy_Pyra_2txt (accessed 19 April 2003).
back to work index / back to main index