
Active Directory (Part 2)
As I said earlier, the Active Directory is a HUGE topic that can span upto a website all by its lonesome. In this section, I'll cover some of the topics related to managing multiple domains within the Active Directory and managing the Active Directory replication.
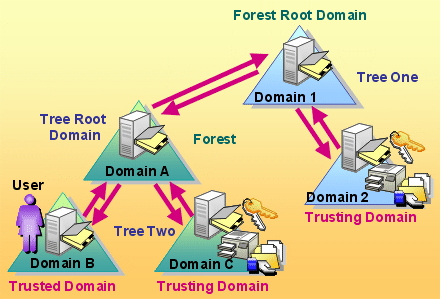
First of all, you may wonder why we need a separate domain. Some organizations that may need separate account policies(account policies apply to the domain only and not to the OUs) or require a large number of objects in the Active Directory may opt for a multiple domain structure. This reduces replication traffic as the domain partition of the Active Directory does not have to be replicated outside the domain. Windows NT administrators may recall that a Windows NT domain had a maximum recommended number of objects for a domain at 40,000 but the Active Directory provides greater scalability allowing a single domain to contain millions of objects; however, replication traffic could become an issue in large domains.

Windows 2000 implements what is known as a two-way transitive trust covering all the domains in the forest. Even if a Windows NT infrastructure is upgraded to Windows 2000, it is, by default, converted to a two-way transitive trust. This trust allows users in one domain to access resources in other domains. The transitive trust in Active Directory infrastructures with large branches would cause a slowdown in access rates because each domain controller will have to refer the user to the immediate parent to obtain a session key until the domain from where there is a branching or link to the destination domain is reached. To work around this problem, Windows 2000 allows the creation of shortcut trusts, which are one-way trusts that can be created to optimize performance by shortening the trust path for authentication purposes. The most effective use of shortcut trusts is when there is a number of users frequently accessing resources in another domain in the forest and the number of domains in the trust path that the client needs to connect to are numerous.

Apart from the shortcut trusts, Windows 2000 also allows the usage of non-transitive one-way trusts for connecting a Windows 2000 domain with a Windows NT domain or for connecting two domains in separate forests.To create a nontransitive trust, you must know the domain names to be included in the relationship and have a user account with permission to create trusts in each domain. Each trust is assigned a password that the administrators of both domains in the relationship must know. If you create nontransitive trusts, you may sometimes need to verify and delete, or revoke, the trust paths you created. You verify a trust to make sure it is working correctly and can validate authentication requests from other domains. You revoke a trust to prevent that authentication path from being used during authentication. You can use Active Directory Domains and Trusts or the netdom command to verify and revoke trust paths. Netdom is a command-line utility that you can use to manage Windows 2000 domains and trust relationships from a command prompt window. You can use netdom to perform the following tasks: View all trust relationships, Enumerate direct trust relationships, and Enumerate all (direct and indirect) trust relationships. The usage of the netdom command is as follows:
netdom trust trusting_domain_name /Domain:trusted_domain_name /verify
netdom trust trusting_domain_name /Domain:trusted_domain_name /remove

Active Directory automatically resolves conflicts in replication. To aid in conflict resolution, Active Directory maintains a stamp that contains the version number, timestamp and server globally unique identifier (GUID) created during an originating update.
Replication within a site occurs through a change notification process. When an update occurs on a domain controller, the replication engine waits for a configurable interval, which is five minutes by default, and then sends a notification message to the first replication partner, informing it of the change. Each additional direct partner is notified after a configurable delay, which is 30 seconds by default. Thus, the maximum propagation delay for a single change, assuming the default configuration and the three hop limit (hops means moving data from one domain controller to another domain controller), should be 15 minutes, which may include the 30 second configurable delay. If no changes occur during a configurable period, which is one hour by default, a domain controller initiates replication with its replication partners to ensure that no changes from the originating domain controller were missed. Attribute changes in Active Directory that are considered security-sensitive are immediately replicated by urgent replication, which occurs immediately.
Update Sequence Numbers
To govern which data needs to be replicated(propagation dampening, the process of preventing unnecessary replication data from being transmitted), each domain controller maintains an array of vectors made up of a pair of data combining a GUID that is unique to each domain controller. This data is called an Invocation ID and a corresponding update sequence number (USN). When an object is updated, the domain controller assigns the changed USN. There is a USN on each attribute and a USN on each object. USNs are used to determine what needs to be updated in a replica. Each domain controller maintains its own distinct USN table for both originating and replicating updates.
Up-To-Dateness Vector
One of the vectors that is used by Active Directory replication is called the up-to-dateness vector. The up-to-dateness vector consists of database-USN pairs that are held by each domain controller, and represents the highest originating update received from each domain controller.
Replication Topology:
When you add domain controllers to a site, the Knowledge Consistency Checker (KCC), a built-in process that runs on each domain controller, generates the replication topology for the forest. The KCC runs at specified intervals and designates the replication routes between domain controllers on the basis of the most favorable connections that are available at the time. To automatically generate a replication topology, KCC uses the information on sites and subnets that belong to sites (a subnet is the portion of a network that shares a common address component), the cost of sending data between these sites, and the network transports that can be used between the sites. The default replication topology in a site is a bidirectional ring, which is made up of two complementary unidirectional connection objects. The ring is constructed with sufficient connections so that the maximum number of hops it takes to replicate an originating update to all replicas of the given partition is never more than three.

An administrator can create connection objects manually in Active Directory Sites and Services, though the KCC automatically creates connection objects in pairs, making two domain controllers sources for each other. Replication can also be initiated by right-clicking a connection object and then clicking Replicate Now.
When you separate domain controllers into sites, you can create site links that allow domain controllers from one site to replicate with that of another site. You can specify settings such as the cost of the link(priority - the lower cost link will be used first; the value can be between 1 and 32,767), replication interval(15 to 10,080 minutes), intersite transport(RPC or SMTP) and other such details. A site link bridge consists of two or more site links. The site link bridge enables transitivity between site links. By default, all site links are transitive; you do not need to create any site link bridges. You can turn off the Bridge all site links feature and manually create site link bridges that you require. You can do this in one of the following situations:
To monitor replication, Windows 2000 provides a command-line utility, repadmin, and Replication Monitor.
With Replication Monitor, you can:
On deleting an object from the Active Directory, the entry is not removed from the Active directory database, but it is tombstoned so that other domain controllers can be notified of the deletion of the record. These tombstoned records are then removed by the Garbage collection process that runs on every domain controller after every 12 hours of continuous operation, which also defragments the database.
Windows 2000 can back up the Active Directory database as part of its system state data. If you would like to undo a change, you can perform an authoritative restore of this data. However, the schema partition of the Active Directory cannot be marked as authoritative. You can also perform a non-authoritative restore to allow a domain controller to perform its regular operation after having obtained updated from other domain controllers. System state data can only be restored to the computer it was backed up from.