Smart
Cards
By Alicia Murphy
Abstract
A smart card is a credit-card sized plastic card that is embedded with a computer chip. The two primary types of smart cards are contact cards and contactless cards. Contact cards
have an embedded micromodule on the plastic of the card. These cards have to be inserted into a reader with direct contact of the micromodule for transmission of data to take place. Contactless cards have the micromodule sandwich in between two plastic cards. It uses antennas to communicate with the reader. A contactless card only has to come into close proximity of the reader for transmission to occur. There are two other types of cards that are derived from the contact and contactless card: the hybrid card and combi card. The hybrid card has both the contact and contactless interface but the two chips are not connected. The combi card has a single chip with a contact and contactless interface. There are two types of chips used in smart cards: memory chips and microprocessor chips. Memory chip cards are non-rechargeable stored value cards; they can be viewed as removable read/write disks with optional security. Microprocessor chips are similar to those chips found inside all personal computers and when implemented in a smart card manages data via a card operating system.
The key to having a completely secure smart card is to have security procedures followed all the way through the life cycle of the card. This starts with the manufacture and ends with the user. The fewer individuals involved with the development and handling of the smart card the less likely the data will be tampered with and the less likely bugs will occur. There are prevention measures put in place to help protect the smart card from attacks, such as the card is implemented with strong cryptographic protocols to increase tamper-resistance. Another prevention measure that should be put into place is to limit the number of times a person can enter an invalid PIN before denial of service occurs. A more aggressive measure would be to program the card to store the history of the use of the card and detect any pattern change. A flag of some sort can be raised if unusual usage is detected, such as requiring the user to notify the issuer before additional use is allowed.
Attacks on smart cards take place for many different reasons but mainly for financial gain. Attackers of smart cars have a slight disadvantage to attackers of PC's because they have to gain physical access to the card. Even after the attacker gains access to the card they still do not have access to any secret information required to activate the card. Another disadvantage is the attacker is on a tight time constraint. It will not take long for the card holder to realize the card is gone.
What is a Smart Card?
A smart card is a credit-card sized plastic card that is embedded with a computer chip that stores information. "You can think of a smart card as a credit card with a brain on it, the brain being a small embedded computer chip" (DiGiorgio). The chip can be either a microprocessor with internal memory or a memory chip with nonprogrammable logic. The data on the card is read through a reader that is part of a computer system. A reader is the device the smart card is inserted into and is the unit that interfaces with the PC for the majority of its processing requirements. Smart card readers interface with a PC through a serial port, USB port, PCMCIA slot, floppy disk slot, and keyboards.6 The number one advantage of using a smart card is that "it can execute cryptographic algorithms locally in their internal circuitry; this means that the user's secrets never have to leave the boundaries of the tamper resistant chip" (Naccache).
History
Smart
cards where first introduced in
Types of Smart Cards
There are two primary types of smart cards: contact and contactless cards. A contact smart card has the micromodule embedded into the plastic of the card. The contact card requires insertion of the card into a reader with a direct contact to the conductive micromodule on the surface of the card. Through this connection transmission of data takes place.
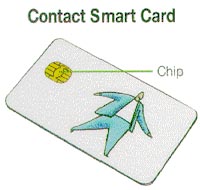
This diagram shows the
micromodule embedded
into the plastic of the
card. Prior to embedding,
a cavity is formed into the plastic card. Then
either a cold or hot glue
process bonds the
micromodule to the card. [8]
A
contactless card has a top and bottom card that sandwich the micromodule. A contactless card only requires the card to
come into close proximity of the reader.
The card and the reader both have antennas; it is via this link that the
two communicate. The card must be within
2-3 inches of the reader. This makes
contactless cards ideal for mass transit which requires very fast
interface.
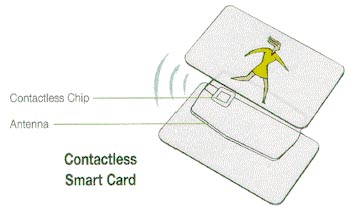
This diagram shows the top
and bottom card
layers which sandwich the
antenna.
The antenna is typically 3
- 5 turns of very
thin wire, connected to the contactless chip. [8]
There are two other types of smart cards that are derived from the contact card and contactless card. They are the Hybrid card and the Combi card. The Hybrid card has both the contact interface and the contactless interface. These two chips are not connected on the card. The Combi card has a single chip card with a contact and contactless interface. With a Combi card it is possible to access the same chip via a contact or contactless interface, with a high level of security. The Combi card seems like the ideal card because you can use it on any interface.
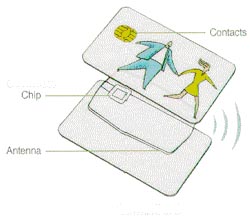
This shows both the
contact and contactless
elements of the card. A
Combi Card has only
one chip while a Hybrid
card has two. [8]
Types of Chips
There are two types of chips used in smart cards: memory chips and microprocessor chips. Memory chips can be viewed as small floppy disks with optional security. [8] There are three primary memory cards: Straight memory cards, protected/segmented memory cards, and stored value memory cards. "Straight memory cards just store data and have no processing capabilities. These cards cannot identify themselves to the reader, so the host system has to know what type of card is being inserted into the reader" (Smart Card Basis, 3). Protected/segmented memory cards are sometimes referred to as intelligent cards. These cards can protect some or all of the memory. They can also be divided into logical sections for planned multifunctional. Stored value memory cards are designed for specific purposes of storing value. These cards can either be disposable or rechargeable. Memory cards are cheaper then microprocessor cards but not as secure. Memory cards depend on the card reader for their processing.
Microprocessor chips allocate card memory into independent sections assigned to a specific function or application. A microprocessor chip manages this allocation. It can add, delete, and manipulate information in the memory. This type of chip is similar to the chip found in personal computers. When it is used in a smart card it manages data in an organized file structure through a card operating system (COS). [7]
Standards
A standard is a protocol used to allow the applications to communicate with the reader which in turn communicates with the smart card. The basic contact smart card standard is the ISO 7816 series, part 1-10. The contactless cards standard is governed by the ISO 14443 standard. These standards are derived from the financial ID card standards and detail the physical, electrical, mechanical, and application programming interface" (Smart Card Primer, 3)".
Reliability
Reliability of the smart card depends on the contents of the card. There is a greater chance of failure if the card is a combi card, which has a contact and contactless chip, an individual's photo, biometrics, and a magnetic strip. The failure is higher for these multifunctional cards because there are so many different components and if one component fails the whole card is seen as invalid.
Security
In each smart card there is an operating system which contains the manufacturer's identification number, type of component, serial number, profile information, and most important different security keys. All of this information should be kept secret through the life cycle of the smart card, from the manufacturer all the way to the card holder. At each phase of the life cycle of the smart card different security measures are taken. The first phase is the fabrication phase. In this phase the silicon integrated circuit chip is created and tested. A fabrication key (FK) is added to protect the chip until it is placed into the plastic card support. The second phase is the pre-personalization phase. In this phase the chip is mounted onto the plastic card and the fabrication key will be replaced with a personalization key. The third phase is the personalization phase which is done by the card issuer. The card issuer adds the data files and application data to the card along with information on the card holder and their PIN to the card. The fourth phase is the utilization phase. This is the phase of normal use of the card by the card holder and all applications and files will be activated. The final phase of the smart cards life cycle is the end-of-life phase. There are two ways to get the card into this phase. One way is to have the operating system to disable all the operations including writing and updating. The only thing that may remain active is the read instructions. The second way to get the card into the end-of-life phase is to have the control system irreversibly block access by blocking the PIN, and then all the operations will be blocked including reads.1
"Smart cards greatly improve the convenience and security of any transaction. They provide tamper proof storage of user and account identity. They protect against a full range of security threats, from careless storage of user passwords to sophisticated system hacks" (Smartcard basis, 2). Smart cards are self contained which makes them resistant to attacks. The only way an individual has access to the information on the smart card is if they get access to your card. Then they would need to know your PIN to access any secret information on the card. This is very unlikely. Many cards only work with a particular reader, so not only do individuals need control of your card and your PIN, but they also need access to the reader. In order to be 100% secure the reader and any other components of the system need to take security precautions.
There are some prevention measures in place to help protect the smart card; such as not using a multi-application card. Although using a multi-application card can be handy, not using one reduces the number of individuals involved in creating the card, which limits the complexity of the card and the potential for bugs. The card should also be implemented with strong cryptographic protocols to increase tamper-resistant. According to the Learning Network cryptography, "the procedures, processes, methods, etc., of making and using secret writing, as codes or ciphers" (www.infoplease.com ).
Another prevention measure is most smart card terminals only have access to the card for a short period of time; this reduces the risk of any attacks or damage to the card. The card could also limit the number of times a person can enter an invalid PIN before denial of service occurs. Lastly a more aggressive measure would be to program the card to store the history of the use of the card and detect any pattern change. A flag of some sort can be raised if unusual usage is detected, such as requiring the user to notify the issuer before additional use is allowed. [6]
Threats to Smart Cards
There are many different types of threats to smart cards, from the user to the issuer. A threat can be considered an attack on the smart card. An attack is defined as an attempt by one or more parties involved in a smart card transaction to cheat. [6] There are several motives for attacking a smart card. The number one motive is financial gain. Another motive may be the desire for notoriety.
There are all kinds of attacks that may take place with the smart card. An attack may be initiated by the terminal, for example you insert your card in the terminal to make a purchase of $5 but the terminal reports $6. An attack can also be done by the cardholder to the terminal, for example the cardholder uses a fake or modified card. The most common attacks are attacks by third parties using a stolen card. The main defense to these types of attacks is the thief does not have access to any secret information required to activate the card. Also the thief only has a limit amount of time before the card holder realizes the card has been stolen
.
Advantages of Using Smart Cards
There are many advantages of using a smart card over the more traditional magnetic strip card such as smart cards are more reliable than a magnetic stripe card and smart cards can store a hundred times more information than a magnetic strip card. Smart cards are also more difficult to tamper with and can be reusable or disposable. If you still need the magnetic strip for certain transactions it can be placed on your smart card. This reduces the number of cards carried by individuals.
Examples of Smart Cards
Listed are different uses of Smart cards. The information is provided by Bruce Schneier.
~ Digital Stored Value Card or Digital Check Card - these cards are very similar. They are used as payment cards intended to be substitutes for cash.
~ Prepaid Phone Card - These cards already have a specific amount allowed to be used on the card.
~ Account based Phone Card - The smart card does not store an account balance but simply an account number.
~ Access Token - In this application the smart card stores a key which is used in a login or authentication protocol.
~ Web Browsing Card - In this application a customer can use his card in his own PC to buy things on the WWW. This is another example of a cash card.
~ Digital Credential Card - In this application, the smart card stores digital certificates or other credentials for presentation to another party.
~ Key Storage Card - In this application, the user stores various public keys in a smart card to protect them from having to be stored on his less secure PC.
Works Cited
1. Chan, Siu-cheung. An Overview of Smart
Card Security. Retrieved:
2.
Cryptography. The Learning Network. Retrieved:
3. Di Giorgio, Rinaldo. Smart Cards: A Primer. Java World. Retrieved:
4. Naccache, David. Cryptographic Smart Card. Micro. Retrieved: April23, 2002, from http://www.computer.org/micro/mi1996/m3014abs.htm
5. Pipkin, Donald. Information Security.
6. Schneire, Bruce. Breaking Up Is Hard To Do: Modeling Security
Threats for Smart Cards.
7.
Smart Card Basics. Smart Cards and Security Overview. Retrieved:
8.
Smart Card Primer. Smart Card