Internet Explorer 6 Security Settings
[1] Introduction
[2] Changing security settings
[5] Malicious hyperlinks: URL spoofing vulnerability
Reference
1. Introduction
The approach to internet browser security involves first of all a high level of personal awareness of the risks. Then there are steps to adopt a few basic strategies and these include: installing an up to date anti-virus, firewall, Microsoft updates, having a high security settings, using browser security software and avoiding unscrupulous or malicious websites.
I cannot stress this strongly enough: you should change to an alternative browser that does not use the IE core, such as Netscape/Mozilla/Firefox or Opera. All the browser hijacking incidents I've seen in forums are from IE. These alternative browsers do not use ActiveX technology. However, Microsoft insists that you use IE for Windows Update and you cannot uninstall IE. So even if you mostly abandon IE, make it as safe as possible.
IE hijacking is covered elsewhere and this article is primarily concerned with IE and internet zone security settings. It is impractical to avoid IE altogether because Microsoft online updates require IE. You can download individual updates and save them using other browsers so that would be a workaround (I use this method anyway). So it is still important to configure IE security correctly.
You should install all the latest Windows and IE6 service packs and updates even if you don't use IE as your default browser because IE (iexplore.exe) is closely tied up with explorer.exe in Windows XP. New vulnerabilities are discovered frequently and you should check the security bulletins and availability of hotfixes regularly.
Set your IE security to at least Medium or preferably higher. The default setting is Medium (see the reference below). The High setting is quite restrictive as it disables most operations. It may cause more inconvenience to your browsing activity as you'll see more prompts and some useful and legitimate browser functions may be disabled. A possible workaround is to add those websites you trust to the trusted zone where the security level would be lower. The High setting is now officially recommended by Microsoft (link).
The suggested settings below would be between the Medium and High settings and in my opinion represent the minimum for safe surfing and avoiding browser hijacking. It would be better to reduce a setting from a higher to a lower level for a particular website that you find too restrictive when browsing than setting the security too low as default. Setting a Medium setting is no longer safe.
You can take this further to the extreme by separating websites into two zones: the trusted zone (with security settings similar to my recommendation below) and everything else in the untrusted internet zone (with High or maximum security settings; more details here).
It is also possible to configure other aspects of IE security in terms of restriction policies (such as home page locking) in Windows XP Professional with the Group Policy Editor (or regedit in Windows XP Home edition if you know which keys to modify) or the Microsoft IE Administration Kit or a third party programme (Internet Explorer Restrictions); aspects of these are covered elsewhere under IE hijacking.
Restriction policies are in general not very effective: they can prevent the console user from making changes in IE but are not effective to block scripts (esp. vbs and js) from executing. Therefore you need a good anti-virus programme with script blocking ability or a standalone script blocker to block these malicious scripts.
2. Changing security settings
Go to: IE, Tools, Internet Options, security, Internet, Custom Level:
Under ActiveX controls and plug-ins, choose (fig. 1):
• Prompt Download signed ActiveX controls;
• Disable Download unsigned ActiveX controls;
• Disable Initialize and script ActiveX controls not marked as safe;
• Enable Run ActiveX controls and plug-ins and
• Prompt Script ActiveX controls marked safe for scripting.
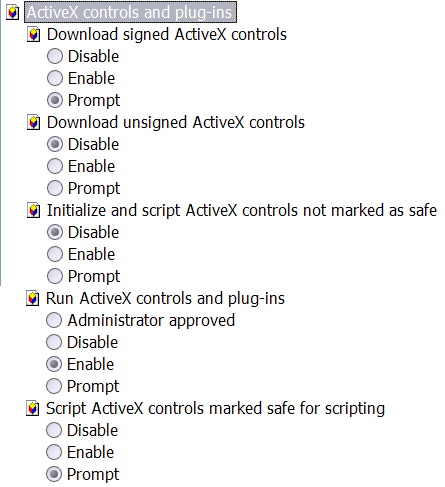
Fig. 1. ActiveX settings.
The last setting brings up frequently prompts in some websites including the Microsoft website (Fig. 2). With this setting you choose to be in control at the slight inconvenience of having to click Yes in the prompting window. Set it to Enable if you don't want the prompts.
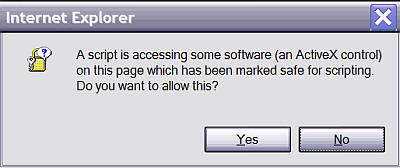
Fig. 2. ActiveX control warning dialogue box.
Under Microsoft VM, Java permissions, choose High safety (fig. 3). Disabling it would stop features in web pages using Java from working. There is another setting for Java VM in the Advanced tab. If you install Sun's Java you'll find it's entry there too.

Fig. 3. Microsoft VM setting.
Under Miscellaneous, choose:
• Disable Allow META REFRESH;
• Prompt Display mixed contents;
• Disable or Prompt Installation of desktop items;
• Prompt Navigate sub-frames across different domains
• High safety for Software channel permissions and
• Prompt Submit non-encrypted form data.
Under Scripting: choose (fig. 4):
• Enable Active scripting
• Prompt Allow paste operations via script and
• Prompt Scripting of Java applets.

Fig. 4. Scripting settings.
The first setting here is normally fine for websites in the internet zone. If it is set to Prompt, you will see frequent warnings when surfing some websites (fig. 5).

Fig. 5. Script warning.
3. Microsoft Java VM
If you use Microsoft Java VM (virtual machine), update to the latest Build 5.0.3810 which patches a ByteCode Verifier Vulnerability (Technet and KB article) or use Sun's version, which is the real thing and more secure and updated. Microsoft has ceased releasing its own Java VM due to legal reasons.
Note that MS Java VM is included in Windows XP Gold and Windows XP SP1 only. If you update SP1a instead there is no MS Java VM. If you update Windows XP Gold or SP1 to SP2, it will be removed. If you really want it, unofficial repackaged versions can be found on the internet (e.g. MSFN).
4. Other security software
To reduce the risk of installing browser hijack objects further, install:
Browser Hijack Blaster (or another real time registry monitoring programme like Spybot Search and Destroy's Tea Timer, or Startup Monitor),
run HijackThis,
Spybot Search and Destroy (including
Tea Timer),
Spyware Blaster,
Ad-aware SE (personal edition is sufficient)and a
Trojan
scanner periodically. Make sure you update these applications too.
Sometimes this is also useful:
HTASTOP 2003 (but note this would disable some Windows applications
like the Control Panel, User Accounts; read the setup information
carefully).
5. Malicious hyperlinks: URL spoofing vulnerability
An input validation error has recently been found to be a vulnerability in IE causing the Address Bar and the Status Bar to display a fake URL using some characters. Please read this and this KB article for more details and steps to be taken.
The recent Cumulative patch for IE (Q832894, 2 February 2004) appears to address this problem.
Please check for Windows and IE updates regularly for newer patches.
6. IE 6 SP2 Security Changes
Windows XP SP2 (released in August 2004) has brought tighter security measures in IE in two main areas that are customisable.
1. Disabling running scripts from your HD and CDROM. When opening an HTML file from your HD, you will see a yellow bar on top warning you about security. Click on it to read what it says. If you know what you're doing, these measures can be re-enabled in:
Tools, Internet Options, Advanced, Security:
□ Allow active content from CDs to run on My Computer
□ Allow active content to run in files from My Computer
2. New ActiveX control settings in:
Security Settings, ActiveX control and plug-ins:
О Automatic prompting for ActiveX controls
О Binary and script behaviors
Reference
![]() Go to TOP
Go to TOP
Copyright © 2003-2005 by Kilian. All my articles including graphics are provided "as is" without warranties of any kind. I hereby disclaim all warranties with regard to the information provided. In no event shall I be liable for any damage of any kind whatsoever resulting from the information. The articles are provided in good faith and after some degree of verification but they may contain technical or typographical errors. Links to other web resources may be changed at any time and are beyond the control of the author. Articles may be added, removed, edited or improved at any time. No support is provided by the author.
All the products mentioned are trademarks of their companies. Edit the settings at your own risk and back up first. Due to new vulnerabilities being discovered frequently even the highest security setting may not guarantee immunity from hijacking and other exploit.
Last updated 4 Apr 2005