| Home │ Wireless Network Security Part 2 │ | ||
Wireless Network Security in Windows XP (Part 1)Revised and updated 13 Feb 2005 Topics on this page: [1] Introduction [2] Hardware and Software requirements [3] The basic principles for wireless security In part 2: [4] router Security Settings (continued) [5] How to add SSID/WPA keys on a computer with Windows XP SP2 [6] Other network security considerations [7] Troubleshooting Glossary References
1. IntroductionWireless local area networking (WLAN) is increasingly popular even for home users and both Windows XP Home Edition and Professional support it and this is further enhanced in Windows XP SP2. This article shows you how to configure high security settings in your wireless router and Windows XP for the home or small office/home office (SOHO) user, taking Linksys WKPC54G kit (wireless G router WRT54G with notebook PC card) and Windows XP Professional SP2 using infrastructure mode as examples. It will focus only on these considerations: (Wi-Fi Protected Access) WPA, (Temporal Key Integrity Protocol) TKIP and (pre-shared key) PSK, (Service Set Identifier) SSID and MAC address filtering. The principles are the same whether you use 802.11b or 802.11g. It will not teach you how to set up a network or share file in Windows (which you should also attend to). By setting a few options you can make "war driving" much more difficult for the causal user wondering nearby. From the outset you are most strongly urged to use WPA (the newer interim standard) rather than older Wired Equivalent Privacy (WEP) if possible. Large corporate users should employ more advanced security setup with the required hardware support and network security is the responsibility of dedicated network security staff. I will not discuss the principles of wireless networking, Remote Authentication Dial-In User Service (RADIUS) set up or the underlying technical aspects of encryption and authentication; please consult the references in part 2 or elsewhere.
2. Hardware and Software requirementsWithout getting into semantics, for the purpose of this article, wireless routers for the home use normally would include a built-in wireless access point (AP), wired LAN ports and gateway for wide area network (WAN). Consumer wireless routers are available from Linksys, Netgear, Buffalo, D-link for example. This tutorial will concentrate on using Wi-Fi Protected Access (WPA) because it is much more secure than WEP but it requires updated versions of: (1) Windows XP WPA client (contained in KB 826942; overview in KB 815485 for Windows XP SP1; or already included in SP2 - hence the recommendation for updating to SP2); (2) router firmware and (3) wireless network adaptor (wireless NIC) drivers. Updated firmware and drivers can usually be found on the manufacturer's websites. New routers bought since the latter half of 2004 should support WPA. Check the website and labels on the product before purchase. For laptops, Intel Centrino processors are optimised for wireless networking but it's not a strict requirement for wireless networking. You would normally add an external (USB or PC card for laptops) or internal wireless G adaptor (PCI for desktops or mini-PCI for laptops) to use the 802.11g standard (54 Mbs). Your Intel Centrino laptop should be ready to go wireless out of the box. If the WPA option is seen in Windows XP wireless connection properties then it should be ready for setting up WPA without further updates unless there are problems.
3. The basic principles for wireless securityThe list is not exhaustive but would include the following when applied together. They are not all equally important and your own requirements may differ.
The most important feature to adopt is WPA rather than WEP because of the capability of rekeying, stronger encryption and authentication in WPA. If you must because of hardware limitation, use WEP with the highest possible bit (128 or above) encryption and manually change the key regularly. Note that disabling SSID broadcast can cause connection problems in some cases (it works fine in my setup). SSID can be discovered using a software so it only deters the casual user from finding out. MAC address filtering is troublesome to set up for many computers and is not foolproof (the MAC address can be sniffed from interceded packets). Many home users do not configure any security settings; it is not uncommon to be able to find several wireless APs from your home (as is the case in mine) with SSIDs and no encryption if you R click the Windows wireless connection icon to view all the connections.
4. Router Security SettingsOther routers are similar though not identical but the principles are the same. Not all routers have all the settings discussed below but should have the most important ones. Logon to the router to change its settings using wired LAN as it's easier to undo the changes and avoid any wireless connection problems while doing it). Remember the logon password and encryption key you set. After you've made changes, click the Save Settings button. First and before doing anything else, change the default Router Password. Leave Remote Router Access disabled unless you need to use this. Leave UPnP disabled unless you need to use this, say for Windows Messenger (fig. 1). Once you have changed the password you would normally be required to re-logon to the router.
Fig. 1. Change router password.
Limit Number of Address (the number of computers being able to connect to the router). If you are a home user with one or two wireless computers, there's no reason to allow 50 (the default in Linksys, fig. 2). Reduce this to a sensible number.
Fig. 2. Limit number of address.
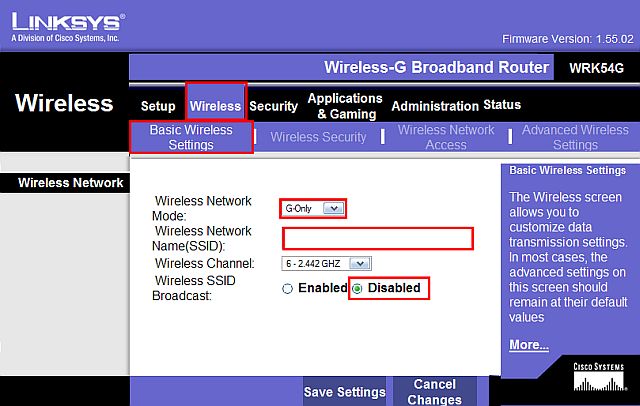
Change the default Wireless Network Name (SSID) to a name of your choice and set Disable Wireless SSID Broadcast (see my comments above). Optionally limit the Wireless Network Mode to G-only if you are only using 802.11g hardware (rather than mixed - B and G so that 802.11b equipped computers cannot connect; fig. 3).
Fig. 3. Change SSID and disable SSID Broadcast
Copyright © 2004-2005 by Kilian. All my articles including graphics are provided "as is" without warranties of any kind. I hereby disclaim all warranties with regard to the information provided. In no event shall I be liable for any damage of any kind whatsoever resulting from the information. The articles are provided in good faith and after some degree of verification but they may contain technical or typographical errors. Links to other web resources may be changed at any time and are beyond the control of the author. Articles may be added, removed, edited or improved at any time. No support is provided by the author. This is not an official support page for any products mentioned. All the products mentioned are trademarks of their companies. Created 5 Dec 2004; updated 27 Feb 2005 |
||