Rule Base
Security
Policy
-
Definition:
a set of rules that collectively determine what traffic is allowed and what is
not
-
Enforcement Directions:
there are three different directions
-
Default Inbound
-
Outbound
-
Eitherbound
-
Inbound
If an inbound rule is
applied, packets going into the FireWall are checked
-
Outbound
If an outbound rule is applied, packets leaving the FireWall are checked
-
Eitherbound
If an eitherbound rule is applied, packets going into and leaving the
Firewall are checked. Checking traffic both ways is CPU intensive.
The effective security settings
are a combination of settings found in the Security Policy Properties and the
Rule Base. Packets are matched in the following order:
-
Anti Spoofing
-
Any properties marked FIRST in the Security
Policy Properties
-
Rule base order (except for the last rule)
-
Any properties marked BEFORE LAST in the
Security Policy Properties
-
Rule Bases last rule
-
Any properties marked LAST in the Security
Policy Properties
-
Implicit Drop Rule (drop everything not
mentioned above)
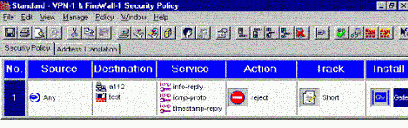
Sample Rule Base
-
Define a Rule in the Rule
base
- you must specify a minimum of Source,
Destination, Service, Action, and where to install the policy (e.g., the
enforcement point, generally the default Gateway).
-
Implicit Drop Rule
Drops everything without logging.
-
Explicit Clean-up Rule
As you will probably want to know what
other traffic is attempting to come through the Firewall you should create an
explicit clean-up rule and add logging. This should be the last rule in the
rule base and needs the following details ANY - ANY - ANY DROP LONG
-
Stealth Rule
- The first rule in the rule base that prevents direct access to the firewall.
Note:
Rule Base Order is very important. The Firewall will implement
rules in a Top Down order.
Verify the Rule Base to ensure
the rule base settings are usable.
Install the Rule Base so that
Firewall-1 will compile them, generate the corresponding script, and make it run
in the enforcement point.
The
Security Policy Tab (Rule 0)
Applying
Gateway Rules to Interface Direction
-
Inbound (Default)
Enforces the security policy only on packets entering the Gateway. Packets
will be allowed to leave ONLY if Accept Outgoing Packets is selected.
-
Outbound -
Enforces the security policy only on packets leaving the Gateway. A rule can
still be enforced in the incoming direction by selecting Destination under
Install On and specifying the Gateway in the Rule Base. At least one rule like
this must be present or no packets will be allowed to enter the gateway.
-
Eitherbound
-
Enforces the security policy only on packets entering and leaving the Gateway.
Firewall-1 inspects packets twice, once on entry and again when leaving.
TCP Session Timeout
Specify time in seconds after
which TCP session times out.
Accept UDP Replies
Check to accept reply data in
a two-way UDP communication.
UDP Virtual Session
Timeout
Specify time in seconds a UDP reply channel remains open without packets being
returned.
Enable Decryption
on Accept
Check to decrypt incoming,
accepted packets even when the rule does not include encryption.
Implied Rules:
Implied rules
are generated in the Rule Base for global properties. Check the properties
enforced in the Security Policy and then choose a position in the Rule base for
the implied rule.
First place first in the Rule
Base
Before last place before the
last rule in the Rule Base
Last place as the last rule
in the Rule Base
Accept VPN/Firewall-1
Control Connection
Used by Firewall-1 for
communication between Firewall daemons on different machines and for connecting
to external servers such as RADIUS and TACACS.
Accept RIP
Check to accept RIP used by routed daemon.
Accept Domain Name
Over UDP (Queries) Check to accept DNS queries used
by named.
Resolves names by associating
them with their IP address. If named does not know the IP address of a host
name, it issues a query to the name server on the Internet. UDP replies must
therefore be enabled to receive the replies.
Accept Domain Name
Over TCP (Zone Transfer) Check to allow upload of
Domain Name resolving tables.
Accept
ICMP Check to accept Internet Control Messages. This protocol is used to
ensure proper and efficient operation of IP.
Accept Outgoing
Packets Originating From Gateway Check to accept all
outgoing packets from Firewall-1 not from the internal network. Gateway rules
are usually enforced in the inbound direction. When packets passing through the
Gateway leave, it will be allowed to pass only if one of the following
conditions is true:
-
Accept Outgoing Packets property is checked
-
Rules are enforced in both directions
(Eitherbound), and there is a rule to allow packets to leave the Gateway.
Log Implied Rules
Implied rules are generated in the Rule Base from the
properties defined in this window. If this is checked Firewall-1 generates log
records for communications matching the implied rules.
Install Security
Policy only if it can be successfully installed on ALL selected targets
The Security Policy will either be installed on all or none
of the selected targets. Allows Administrator to ensure the same Security Policy
is being enforced at all enforcement points.
Rule Base
Possible
Rule Base actions include
-
Accept
-
Reject - reject the packet and inform the
sender
-
Drop - reject without informing the sender
-
User Auth - use User Authentication on this
packet
-
Session Auth - use Session Authentication
on this packet
-
Client Auth - use Client Authentication on
this packet
-
Encrypt - encrypt outgoing and decrypt
incoming traffic used with the extra VPN module not covered in this exam
-
Client Encrypt - encrypt outgoing and
decrypt incoming traffic with the help of a secure remote client
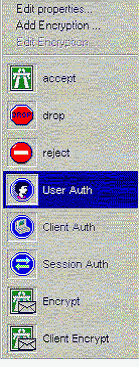
Rule Base Actions
System
Status Tool
-
Tells the number of packets
dropped/rejected/inspected/logged
-
Tells whether or not a security policy is
installed on the firewall, the name of the policy installed, and the date the
security policy was installed on the firewall
-
The most important display shows the status
of the Firewall-1 Daemon, whether it is INSTALLED (daemon is running, and
security policy is installed), NOT INSTALLED (daemon is running, but no
security policy is installed), and DISCONNECTED (no response from the daemon
at all)
Content
Security
-
Uses CVP (Content Vectoring Protocol), a
TCP based protocol developed by Checkpoint that uses port 18181 to
transparently re-route the data stream to an external content scanning server.
A CVP server object needs to be created for content security to work
-
Supports SMTP, HTTP and FTP; each has a
corresponding resource object type that can be defined in the rulebase
-
SMTP security functions: hides outgoing
emails FROM field, redirects email sent to given TO or CC addresses, drops
emails from particular senders or messages above a particular size, strips
MIME attachments, strips the RECEIVED field, and transparently relays email to
a third party anti-virus server
-
FTP security functions: controls the GET
and PUT operations, and transparently relays data stream to third party
anti-virus server
-
HTTP security functions: URL screening,
blocks Java code, strips all the script/applet/ActiveX tags in the HTML code
(known as HTML weeding), and anti-virus using third party server
-
URI (Uniform Resource Identifier) is the
resource object type for HTTP
Anti -
Spoofing
-
Configuration done in Firewall's Interface
properties - Valid Addresses section
-
Possible options:
-
Any - the default choice, no anti-spoof
config in place
-
No Security Policy - nothing at all
-
Others - all packets are allowed except
those with source IP addresses from networks listed under Valid Addresses for
this object's other interfaces
-
Others+ - same as Others, but packets from
addresses listed under the Others+ section are allowed
-
This Net - only packets from network
attached to this interface are allowed
-
Specific - only packets from a specifically
defined object we define are allowed
Back
Home


