PC Hardware & Network Course
T.I. McLaughlin
B-admin, MCSE, MCT, A+ Hardware Certification
tom@mclaughlin.net
http://tom.mclaughlin.net
©Copyright
2000 T.McLaughlin & Associates
![]()
TABLE OF CONTENTS
Overview
![]() Learn
the fundamentals of maintaining, troubleshooting and repairing your computer.
In a hands-on environment participants will get under the hood of a PC to explore
its components, architecture and design. In a thorough and systematic approach
we will assemble a PC from its basic components, configure and run diagnostics.
Participants will leave with a confident knowledge base and skill sets to
configure, upgrade and troubleshoot their own computers.
Learn
the fundamentals of maintaining, troubleshooting and repairing your computer.
In a hands-on environment participants will get under the hood of a PC to explore
its components, architecture and design. In a thorough and systematic approach
we will assemble a PC from its basic components, configure and run diagnostics.
Participants will leave with a confident knowledge base and skill sets to
configure, upgrade and troubleshoot their own computers.
|
PC Overview History of PCs PC Architecture ISA, EISA PC Components RAM, SIMM, DIMM Monitors VGA & SVGA
Monitors and Dot pitch Disassembling the
PC Disassembly
Preparation Installation
Procedures Installing a Hard
Drive Networking Network Types |
System Architecture Network Interface
Cards Memory Management Memory Overview Performance
Optimization Enhancing Win95/98
Performance Troubleshooting Basic
Troubleshooting Utilities Scandisk Tools & Test
Equipment Exploring
the toolbox |
Computers in plain English
Copyright
1996, 1998 by Morris Rosenthal
For more info get McGraw-Hill's published book, “The Hand-Me-Down PC“
Most people
who buy a car are not automotive engineers. Yet the vast majority of us make
comparisons between cars as a part of the buying process. If you have a lot of
kids, you want a lot of seats. If you have a lot of tools, a pickup or van may
be a good choice. Big motors usually pull more weight, turbo-chargers make it
go faster. Cruise control and air-conditioning are luxuries for some and
necessities for others. You don't need to be a musician to decide on a stereo
and you don't need to know how a transmission works to choose between a manual
and an automatic. When the car gets old, and the transmission shop wants $1000
to put in a rebuilt with a 90 day warrantee, the decision to invest the money
or buy a new car often has as much to do with the condition of your bank
account as with the overall condition of the car.
Like
automobiles, many models are built on the same chassis, with the most expensive
loaded models costing more than twice as much as the stripped down economy
version. There are many "after-market" enhancements you can make,
some are "add ons" and some replace the original components. The
expensive models have the potential to get you where you're going faster, and
in more comfort. However, there are few fundamental differences between PCs and
cars that make buying and owning a PC a whole lot easier. One difference is
that PCs are all built to standards such that their component parts, even
across brands, are largely interchangeable. Another difference is that is that
most of these parts are either commodities or available from a single source
only, i.e., you can buy memory or a floppy drive from any manufacturer, but
Intel chips come from Intel Corporation and MS DOS comes from Microsoft.
The System Box or Case
There are
two kinds of computer parts. There are things that go in the system box, and
things that attach to it. The system box itself is either a flat metal box,
with a couple buttons and lights on the front with at least one place to insert
a floppy disk, or the same flat metal box stood on end. The flat box lying down
is called a "desktop case" and the flat box standing up is called a
"mini-tower." Big mini-towers that sit on the floor are called
"towers." The system box has one power cord that gets plugged into
the wall, and all sorts of connection points called "ports" for
things outside the box to get plugged into. Two things that every computer will
have plugged into ports are a keyboard and a monitor (TV display). Other things
that are commonly plugged into ports on the system box include: a mouse, a
printer, a telephone wire, a joystick, and speakers. The parts that get plugged
into ports on the system box are often called "peripherals."
Before we
start to examine things that go in the system box, let's look at the box
itself. The front of the system box is covered by a plastic faceplate, with
several rectangular cutouts, a couple buttons and LEDs (lights), a keyhole, and
a power switch. The power switch is often on the side of the older desktop
cases. The rectangular cutouts cover the drive bays, where floppy drives, CD
ROM drives and hard drives are screwed in. The larger bays house 5 1/4 "
floppy drives, CD ROM drives, and older hard drives. The small bays house 3
1/2" floppy drives and newer hard drives. The two push buttons, side by
side, are labeled "reset" and "turbo." The reset button is
for re-starting the computer if it stops responding to keyboard and mouse
input. The turbo button switches the machine between its top speed, and a slow
speed on older computers. The power LED should be lit all the time when the
computer is on, and the HDD LED would blink when the hard drive is being
accessed. The buttons and the LEDs are for the benefit of the user. The
computer will work fine even if they are hooked up wrong or broken.
Inside the
box is normally where the confusion begins. Here we have RAM, ROM, Megabytes
and motherboards, drives and adapters. All of these things are necessary for
even the most stripped-down computer, but they need no assembly beyond plugging
connectors together and turning in the occasional screw. The cost of each part
can be as high as a couple hundred dollars, or as low as $10 or $20. The first
part we'll consider, the power supply, is usually purchased with the system box
itself, and in some brand name machines, will have a unique shape (form
factor). A unique and painful replacement cost goes hand- in-hand. Power
supplies and system boxes are normally sold together, for a price between $40
dollars for a cheap mini-tower to $70 for a desktop and over $100 for a tower.
The cheapest cases often have metal burrs inside that scratch unwary hands, and
lack fit and finish.
The Bare Bones System
A bare bones
system consists of a case, power supply, motherboard, CPU (brain) and memory.
New computers are often sold to computer stores and other resellers as
"bare bones" for a couple of reasons. One is the FCC (Federal
Communications Commission) approval sticker that should appear on the back of
every computer, certifying that it won't interfere with your neighbors TV or
radio. Manufacturers will sell "bare bones" systems as FCC approved,
although there is no guarantee they would pass the test with other parts added.
Another reason is that screwing in the motherboard and connecting all the
little lights and switches is a dreary job that most resellers are willing to
pay a few dollars to avoid. We will take advantage of the "bare
bones" approach and divide up the parts inside the system box into three
categories: "bare bones," "drives," and "adapter
cards."
The Power Supply
The power
supply, which is attached to the case with four to six screws, takes the
115volts of AC power from your wall plug, and turns it into the small DC
voltages that all computer components operate on. The only continuous sound
computers make when turned on is the power supply fan cooling the power supply.
If the fan fails, the power supply will quickly overheat and fail. The cost of
a standard power supply, for both mini-tower and desktop cases, is around $35.
Old fashioned "AT" type power supplies, with a large paddle switch on
the side, run over $50. The main figure of merit for power supply connoisseurs
to boast about is their power output, in watts. The standard, cheap, power
supply delivers 200 watts, which is more than you'll ever need. The power
supply performs two jobs insides the box. One is to supply power to the
motherboard in a wide variety of voltages, and the other is to provide power to
the drives.
The Motherboard
All of the
parts that go into building a computer have a direct connection to the
motherboard. The motherboard, besides serving as the traffic cop for routing
information to all the parts, also serves as the home of the brain (CPU) and
the memory (RAM), which fit into special sockets. A lot of terminology is used
to describe different flavors of motherboards and their capabilities, but most
variations have little real impact on the user. The main point to get is that
the motherboard is where the software you will run on your computer actually
executes, as the brain works with the information stored in the memory.
Motherboards are often sold with the brain (CPU), and a new generation of
motherboard must be designed for each new CPU (386, 486, Pentium) that's
released. A 386 motherboard, with CPU, has no value on the market, while a new
486 motherboard with CPU might sell for up to $75 dollars. Pentium
motherboards, with CPU, range from $100 to $1000 dollars, depending on the
exact model (Pentium, Pentium MMX, Pentium PRO, Pentium II).
CPU (The Brain)
The vast
majority of all CPUs mounted on PC motherboards from the beginning of time (the
early eighties in this case) are manufactured by Intel. Other companies that
have tried competing, including NEC, Texas Instruments, Cyrix, and Motorola,
which makes the CPUs for Apple Computers. However, the only CPUs besides Intel
that you're likely to find inside a hand-me-down PC are manufactured by AMD
(American Micro Devices). Fortunately, they follow the same nomenclature, so I
will usually omit the manufacturer and refer to CPUs generically as 386s or
486s. The primary figure of merit for a CPU is the clock speed, measured in MHz
(Megahertz). To understand speed with which CPUs operate, let's compare them to
alarm clocks.
CPUs are
digital. The CPU clock speed tells us how many step changes, or operations, the
CPU will make in one second. For example, a 386DX-25 CPU does 25 million
operations per second. A 486SX- 25 CPU also does 25 million operations per second,
while a 486DX/4-100 CPU does 100 million operations per second. CPUs all do
millions of operations per second, expressed as "MHz," so we only
need to comprehend the smaller number, 25, 66, 100. The speed of the CPU isn't
the only thing that determines how fast the computer runs your software
(imagine putting a race car engine in a truck), but the higher the number, the
faster the machine.
There are
three other parts to the nomenclature, which you may have noticed above. First
is whether we have a 386 or a 486. CPU manufacturers improve their chips with
each generation, and the 486 is required by many newer software packages. The
486 replaced the 386, just as the 386 replaced the 286, which was the CPU in
the IBM PC-AT. Don't pay for a 386. Another part to the nomenclature is the
"DX" or "SX" part, and the last bit is the "4"
that appears in the 486DX/4-100. With both 386 and 486 CPUs, the DX does
complicated math (engineering calculations) better than the SX. Some software
may require that you have a DX type CPU, or that you buy another CPU like chip
known as a math co-processor to compensate. Just remember DX is better than SX,
and don't buy a machine with an SX CPU unless it comes with a real nice monitor
you can use on your next machine. The "4" that appears in 486DX/4-100
or the "2" in 486DX/2-66 tells us that while the CPU runs at the
stated speed, 100 or 66, it talks with the motherboard it's plugged into at a
lower speed. That means it can work very quickly with information held in the CPU,
but if it has to go out and get something from memory, things slow down.
Current CPU speeds in new Pentium PCs range from 166MHz (a low end Pentium MMX)
to 500MHz for a high end Pentium II.
RAM (The Memory)
Memory is
what the CPU shuffles through in order for the software to accomplish anything.
The CPU never looks directly at the information on your floppy disk or your
hard drive. This information is copied into memory by one of the traffic cops
on the motherboard. The CPU then reads this information from the memory and
acts on it. Random Access Memory (RAM) is called by this name because the CPU
can get information from any location in the memory in much less than a
millionth of a second. Even picking spots at random, the retrieval speed
remains unchanged. This is very different from the case with a floppy drive.
Bits of information stored next to each other on the floppy can be read
quickly, while bits that are recorded a couple inches away on the disk take
much longer to retrieve, actual fractions of a second! Sometimes a
"D" is added to the front of "RAM," which makes the word
"DRAM." The "D" stands for dynamic; because the RAM
actually forgets what its holding if the motherboard doesn't continually
refresh (read and re-write) the information. Everything in DRAM disappears when
the computer is turned off.
Computers
work with very small bits of information, intelligently known as
"bits," which have to be combined together into larger clumps to make
any sense. The basic clump used by computers consists of 8 bits and is known as
a "byte." Memory size is measured in bytes, and more is always
better. Since computers need huge numbers of bytes to do anything useful, the
measure of a "megabyte," one million bytes, is used. Early 386
machines could limp by on 2 megabytes (MB) of RAM, but 4 MB is the minimum
required to run Windows 3.X in a reasonable fashion. 8 MB works fine with older
software, but many new programs are requiring 32 MB. Very few DOS/Windows
programs require 16 MB (the next possible increment due to the way memory is
installed in most machines), but overall performance does improve with
additional memory. Windows 95 can operate with 8MB, but many Windows 95
applications require 16MB, and 32MB is now standard on the run-of-the-mill new
PC.
Drives
Drives provide
the permanent storage for your computer. When the computer is turned off, all
of the parts except for the drives are effectively wiped clean. Drives all use
electric motors to spin disks or tapes, and require a power lead directly from
the power supply. Most drives, like floppies, CDs and tapes, use a removable
media that we slide into the drive on the front of the system box. Some special
purposes drives (you’ll rarely see one on a hand-me-down PC) sit entirely
outside the system box and is connected by a cable to a special port, and these
are called "external drives." Hard drives are sealed against the
atmosphere, and have no removable media. These drives can rarely be seen from
the outside of the system box, which is why manufacturers include a "HDD"
LED (light) on the front panel to show when they are being accessed.
The Floppy Drive.
Floppy
drives and floppy disks come in two sizes: the older, flexible, 5 1/4"
disks and the newer, rigid, 3 1/2" disks. Floppy disks, which are read by
a floppy drive, provide permanent, removable storage for your computer. The
storage is permanent, because it is recorded in the magnetic material of the
disk the same way that audio or videocassettes are recorded. As long as you
keep the disks away from big magnets and don't spill coffee on them, they'll
hold the information for a couple years. Several different formats for floppy
disks exist, which describe how much information can be recorded on them. New
drives, with High Density floppies, record 1.2 MB on a 5 1/4" disk and
1.44 MB on a 3 1/2" disk. The drives are cheap. A brand new 1.44MB drive
costs about $25, a 1.2MB drive about $35.
Hard Drives
Now we're
getting to the real storage. The hard drive is essentially several
non-removable rigid floppy disks stacked together with a drive built around
them. Because the disks are rigid, the read/write heads can be positioned much
more accurately, allowing more information to be written (higher density).
Another advantage is the disks can spin much faster, thousands of RPM
(Revolutions per Minute). As a result of higher recording density and faster
spinning, hard drives can write and retrieve information much faster than
floppy drives. The most important measure associated with a hard drive is the
capacity, how many megabytes it can store. Hard drives being sold today can
hold over 1000 floppy disks worth of information, but our older drives have a
more modest capacity.
About the
smallest drive you'll find in an old 386 is a 40MB drive, which could just
about hold DOS and Windows with a couple small programs. Drives up to about 500
MB are commonly found in older PCs, and some machines will have a second drive
installed. Pricing for old drives is irrelevant; since they quickly disappear
from the market when new drive prices fall. About the smallest hard drive
commonly available today is the 800MB drive for $100. A 1000 MB (or 1 gigabyte)
drive costs about $125, and a 3.0GB drive goes for less than $240. Hard drives
are very reliable (much more so then floppies) and most have an operating life
exceeding five years. However, if you have important information on your hard
drive, say your checkbook or your unfinished novel, it's always a good idea to
make a fallback copy onto a floppy disk. This procedure is known as "backing
up." Store the backup disk(s) away from the computer, so in case of fire
or theft, you still have your copy.
CD-ROM Drives
CD drives
are relative newcomers to PCs, coming into common use about five years ago. CD
drives made possible the delivery of huge software programs and games to the
user that would otherwise require hundreds of floppy disks. CD discs are very
cheap to mass manufacture at about 60 cents each, and have tremendous shelf
life, over 100 years. All CD drives are capable of playing regular music CDs,
and have a headphone jack on the front of the player. If the system box
contains a sound card, the music can be amplified and played out of speakers.
CD discs come in one size only, with a maximum capacity of about 680 MB. The
main comparison between CD drives is the transfer speed, how fast they can hand
information to the motherboard to be placed in memory. This is expressed as a
multiple, 2X, 3X, 4X, 6X and so on of the original CD drive transfer speed,
which was the same as that of a stereo CD player. The current state of the art
CD drive is the 52X, which costs over $100. DVD drives are just coming onto the
market with in their 4.0GB incarnation and can hold up to about seven Cd’s on
one DVD.
Tape Drives
Many older
PCs are equipped with tape drives for backing up the information on the hard
drive. The most common drives had a capacity of 120 or 250 megabytes, stored on
a removable tape about half the size and twice the thickness of an
audiocassette. The thick metal bottom of the cartridge easily recognizes these
one-sided tapes that helps conduct away heat. Some more expensive or obsolete
drives use tapes as small as a telephone answering machine cassette or as large
as a VHS cassette. Tape drives in individual computers have gone out of vogue for
two reasons. First, they proved less reliable than the hard drives they back
up. Second, as hard drive capacity skyrocketed, the cheap tape drives required
several tapes (and hours) to back up the data. Another reason is that most
companies have installed networks, which allow the administrator to backup
individual computers onto a single, fast tape drive at a central location.
Second-hand tape drives have no market value, and are often
"orphans," i.e., the tapes are no longer available.
Adapters
Adapter
cards that plug into the motherboard are what give PCs the tremendous
flexibility to do all of the jobs we can think up for them. As computer
technology has evolved, the sockets on the motherboard, called "bus
slots," into which the adapter cards are placed, have evolved as well. The
latest adapter cards used in Pentium computers can move four times as much
information in a single effort as the older cards used in 386 computers. Most
486 computer motherboards sport a few slots which fall in- between in this
evolution, allowing use of adapter cards which move twice as much information
at a time as in 386s and half as much as in Pentiums. The classification of
these adapters is important if you are buying replacements, and they go as
follows: 16 bit adapter (286 motherboards and higher), VESA adapter (486
systems), EISA adapter (some 386 systems and higher, very expensive) and PCI
adapter (Pentium systems). All motherboards, including the newest Pentiums,
leave a couple old-fashioned 16-bit slots (sometimes even 8 bit slots!) for
compatibility with old technology. The standard motherboard can support (has
space for) six or seven adapters to plug into the bus.
Video Adapters
The video
adapter performs the job of the cable box or the antennas on your TV. It takes
the information the motherboard tells it to display and generates the signals
that the monitor understands. In the case of old video adapters; Hercules, CGA
(Color Graphics Adapter), EGA (Extended Graphics Adapter), this was a digital
code. Do not pay for a computer with this type of adapter or monitor. The new
generation of adapters, VGA (Video Graphics Adapter), operates more like a
traditional television, providing the monitor with color (Red, Green, Blue -
RGB) information and some timing signals. There are several distinct levels of
performance associated with VGA adapters, namely how many colors they can
display at one time, how much information they can squeeze onto a screen, and
how often they update the information. How fast the different video adapters
can refresh the monitor is dependent on both the adapter and the monitor, and
is set aside for the monitor discussion. VGA adapters come equipped with their
own RAM for temporarily storing what will be drawn on the monitor, and the
amount of RAM usually corresponds with the overall performance of the adapter.
The brand of VGA adapter, and the amount of RAM it carries in kilobytes (KB),
is usually the first thing displayed on the monitor when the computer is turned
on.
SVGA Adapters with 512KB RAM
SVGA
adapters (you caught the "S" sneaking in front of the VGA) are
capable of displaying "Super" VGA resolutions, beyond the 640 by 400
resolution of plain VGA. As you can guess, more resolution means more pixels,
and more pixels at one byte of memory per pixel means more memory. SVGA
adapters can display 800 pixels horizontally by 600 pixels vertically on the
screen. Or, at two bytes of memory per pixel, they can still display regular
VGA resolution. The extra byte per pixel at regular VGA resolution lets the
adapter display 256 multiplied by 256 equals 64,356 colors at one time. Over
64,000 colors are enough to make most images appear as clear as photographs on
a good monitor. SVGA adapters are a minimum requirement for multimedia software
for this reason, the ability to display near to "true" color. Some
people will use the SVGA adapter to display the 800 by 600 pixel resolution
instead, which fits almost twice as much information on the screen in one shot.
Video Adapters with 1MB RAM and Beyond
The standard
video adapter sold today comes with 2MB (2048KB) of video memory, and many 486
PCs were equipped with these cards. With double the memory of the 512KB
adapters, they can send the monitor over 16 million colors to be displayed
simultaneously at VGA resolution. This creates a picture perfect image know as
"true color." Likewise, there is now enough memory per pixel at SVGA
resolution to display over 64,000 colors simultaneously. Most of these adapters
can operate at even higher resolutions, displaying 256 colors at 1024 by 768
resolution, or 16 colors at 1280 by 1024 resolution. These higher resolutions
are normally only used by artists or computer draftsmen who have large monitors
(over 17") and buy video adapters with 2MB of memory or more to allow them
to display more colors at these super high resolutions.
Input/Output (I/O) Adapter
Before we
even begin the discussion of the I/O adapter, we must note that in almost all
386 and 486 computers, the functions of this card have been combined with the disk
controller functions into a single adapter, the SIDE adapter, which will be
discussed in the next section. The I/O functions we discuss here operate
exactly the same way when combined into the SIDE adapter. The I/O adapter
provides several ports, through which the computer communicates with the
outside world. There are three types of ports provided; serial communications,
parallel communications and the game port. Two serial ports are provided,
normally called "Com1" and "Com2," one parallel port called
the "Printer Port," and the game port, normally used to connect a
joystick for arcade type games. Nearly all computers will have a mouse
(pointing device) connected to the Com1 port, and almost all printers sold will
work when hooked up to the printer port. The second serial port normally goes
unused, unless an external modem (connects your computer to the world through a
telephone lines) or some special equipment is purchased. An I/O adapter costs
less than $10.
Other Adapters
A video
adapter and a IDE adapter are the minimum number of adapters required for a PC
to operate. Millions of computers complete their life cycle with no additions
to these two basic adapters. If you don't have any additional adapters, you can
skip down to "Outside the System Box" at this point. There are
literally hundreds of other adapters available for PCs, most of them designed
to let the computer talk to a specific piece of equipment in a laboratory or on
a shop floor. While your hand-me-down PC might contain a left over adapter from
some obsolete system, guessing at what it might be is beyond the scope of this
book. In the next few paragraphs we will cover the more common adapters you
might find in a hand-me-down PC, or buy, but a final word about unknown
adapters. Leave them where they are, and don't start plugging things in unused
ports at random to see if they do anything. In other words, "If it's not
broke, don't fix it."
Internal Modem
About the
most common and most useful extra adapter you can have in your PC is an internal
modem. A modem is a device that gets plugged into a telephone jack that enables
communications between your computer and other computers. These other computers
could be at work, at your bank, or the gatekeepers (servers) on the Internet or
the World Wide Web. Like most computer parts, modems have evolved to
communicate faster and faster over the last ten years. Because of the premium
prices commanded by faster modems, older computers will come with slow modems.
Modems are categorized by their line data rate in bits per second (bps). The
slowest modem you'll find in an old 386 will run at 1200 bps, compared to the
newest modems in Pentiums that run at 33,600 bps (even faster using one way
digital links - up to 56,000 bps). Modems in 386s and 486s can be at either
extreme or fall anywhere in-between. The important cut off number, 14,400 bps,
is known as a "fourteen four," and this is the minimum speed for a
modem to achieve acceptable performance on the World Wide Web. Most modems are
also capable of sending and receiving faxes, but people with a serious amount
of faxing to do will find a regular paper fax far more convenient.
Sound Cards
Sound cards
are adapters that perform at least three functions. Two of those functions are
complimentary; converting analog sound from a microphone or stereo jack into
digital computer codes (A/D) and converting the computers digital codes for
sound back into voice or music, that is played back through speakers (D/A).
They provide enough amplification so that a CD drive played through the sound
card will provide enough power to drive the speakers. Most sound cards also
have a ribbon connector for connecting CD drives that can't be connected to a
different adapter. Musical Instrument Digital Interface (MIDI) sound allowed the
card to create instrumental sound based on "cues," which take less
than 1% the storage space than actual recorded music. Newer cards also support
the Wave Tables, which use pre- sampled selections of actual instruments to
produce a much richer sound than MIDI.
Sound cards,
like everything else, have evolved since their introduction in the early
Nineties. The original successful card was the Sound Blaster from Creative
Labs, and most sound cards manufactured since guarantee "Sound
Blaster" compatibility. The oldest generations, called “eight bit” cards,
are better than nothing, but should not be purchased. "Sixteen bit"
cards are capable of recording and reproducing sound as accurately as your
stereo CD player. However, high fidelity recording also depends on having a
system fast enough to take the recorded sound from the sound card and move it
to the hard drive without any interruptions. A "sixteen bit Sound Blaster
Compatible" goes for around $30, while a real Sound Blaster from Creative
Labs cost about $50. More expensive sound cards with recording studio type
software can cost hundreds of dollars.
Network Adapters
Few of us
have LANs (Local Area Networks) in our homes, but cost is no longer the reason.
Early network adapters costs hundreds of dollars apiece, but while some brand
names still hover around the $100 mark, reliable network adapters for all types
of networks can be purchased in the $30 to $40 range. Special network software,
which once had to be purchased separately, now comes as part of the Window for
Workgroups or Windows 95 software. LANs allow information to be passed from
computer to computer about 1000 times faster than by a modem connection. There
are at least half dozen types of LANs in use, with names like Token Ring,
Ethernet and ArcNet. The most common LANs, outside of big corporations,
variations on the Ethernet standard; 10Base 'T', which uses twisted pair
telephone type wire, and Thin Ethernet, which uses coaxial cable. The $30 to
$40 adapters mentioned earlier support both types of LANs.
Small Computer System Interface (SCSI) Adapters
SCSI
adapters, pronounced "scuzzy," are high performance, general-purpose
adapters for connecting the motherboard to a variety of drives and devices.
Most high performance hard drives are SCSI drives, along with CD Recorders
(CDRs), some CD players, and quality tape drives. SCSI adapters also support
connection to external devices, including portable versions of all of the
above-mentioned drives, and other devices like scanners that digitize (change
into digital computer codes) documents and photographs. A single SCSI adapter
can support up to seven different drives and devices simultaneously. Low
performance SCSI adapters start around $50, while the best adapters with
controlling software cost up to $500. SCSI adapters also support floppy drives,
so some systems will have a SCSI adapter and a I/O adapter instead of a SIDE
adapter.
Video Capture Cards
These
special adapters are used to capture single frames or real motion video from a
VCR, Video Camera, or other video source. Prices for "Frame
Grabbers," which capture a single picture, start under $100 while decent
motion video capture cards start at a few hundred dollars. Capturing quality
motion video is extremely dependent on the system, a fast 486 with a special
A/V (Audio/Visual) hard drive is the minimum requirement, and probably won't
produce anything good enough to be used in a saleable product. Video capture
and edit workstations used by professionals may be based on PCs, but typically
cost well over ten thousand dollars.
Things Outside the System Box
There are
two things that attach to every system box to make it a working PC: a keyboard
and a monitor. Modern software is easier to work with if we add a third item
for pointing at things on the monitor screen, a mouse. The next most common
thing to attach to the system box is a printer, followed by external modems,
external drives, scanners, digitizers, and other special purpose accessories.
In the chapter on what you can and can't do with your hand-me-down PC, we'll
look at some combinations of equipment for different professional tasks. Things
that get plugged into communications ports on the system box are called
"peripherals," and are almost never manufactured by the same company
whose name goes on the system box. Sometimes, the same company name appears on
the peripherals because they pay the real manufacturer to put it there. As with
clothing, mattresses, and other purchases, you can often buy the exact same
part without the brand name for a fraction of the cost.
Keyboards
The keyboard
is are an area where preference for "feel" varies greatly from person
to person. Most people will be comfortable with the first keyboard they work
on, and feel there is something wrong with any new keyboard, until they get
used to it. Most keyboards sell in the $15 to $20 dollar range, including my
personal favorite for reliability and feel from Mitsumi Electronics, over 1000
sold without a single failure. In my experience, extremely expensive keyboards (almost
$200 retail) manufactured by one of the world's largest computer companies,
have a failure rate of about five percent per year. Keyboards receive power
from the motherboard, so there is only one connection to make. The newest
keyboards on the market feature "V" shapes for ergonomic positioning
of the hands, and wrist rests and other devices to combat repetitive use
injuries are available for people who work for extended periods of time typing
every day.
Monitors
Monitors
come in a dizzying array of sizes, capability, and prices. To simplify the
discussion, we will stick to VGA monitors and better. Information about old
"TTL" type monitors is contained in the troubleshooting chapter. The
least expensive SVGA monitors start at around $160. Unfortunately, the
manufacturer's labels on the back of the monitor rarely identify the
capabilities of monitor, beyond giving a model number. Try to obtain the
instruction booklet with any second hand monitor purchase; otherwise you'll
have to trust the seller. Monitors that display VGA resolution only, and
"paper white" VGA monitors are no longer sold and are rarely worth
repairing. If you already own a monitor and are happy with it, you might want
to skip the next section that unavoidably gets a little technical.
Screen Size.
Monitors,
like television sets, are measured diagonally, from two opposing corners of the
picture tube. The standard monitor size is 14," and prices rise rapidly
with increasing screen size. Very large monitors can measure 21" diagonal
or greater, weigh over 80 pounds and cost more than $2000. Manufacturers of
monitors, like manufacturers of some clothing items, are not entirely
consistent with their measuring schemes. Some measure parts of the picture tube
that are hidden behind the plastic bezel of the monitors casing, and others
simply don't allow the screen size to be adjusted to anywhere near the edges of
the bezel. This has led to an unofficial measurement known as "viewable
area," measured diagonally, which describes how large a picture you can
actually see. For example, one 17" monitor may have a viewable area of 16
1/2," while another may have a viewable area of 15 1/2." One recent
innovation is the "flat screen" monitor, which doesn't have the
curved face of the standard picture tubes in most monitors and televisions.
Flat screens look a little better than standard monitors, and cost a little
more.
Interlace and Horizontal Frequency
The two
factors that control how "solid" or "flicker free" your
monitor is are the whether or not the display is "interlaced" or
"non-interlaced," and the horizontal frequency, which controls how
many times per second the screen is redrawn. Monitors, like televisions and
movie projectors, flash a series of pictures at us, which our eyes and brain
merge into a solid image. How many images per second are required to create a
really "solid" looking picture varies from individual to individual,
but the minimum number of times per second (frequency) an image is displayed by
any modern monitor is 60 per second (60Hz). The cost of the electronic
components that control the picture tube go up in price as they go up in speed.
One trick that allowed monitors with slower electronics to draw SVGA resolution
images without excessive flicker is "interlacing." When an image is
interlaced, the monitor draws the entire image more than 60 times per second,
but skipping every other line. On the next redraw, it does only the lines it
skipped. The result is that the entire image appears less bright and a little
flicker to some people, while others don't notice.
Even with an
NI monitor, some people who stare at monitors all day long, especially under
artificial lighting, see flickering or get dizzy by the end of the day. The way
to make the picture appear even more "solid" is to run up the
horizontal frequency to 72Hz or 75Hz. The increase in price to the video
adapter is trivial; in fact most 512K and 1MB SVGA adapters can already handle
72Hz, known as the VESA frequency (VESA for the Video Electronics Standards
Association). The real challenge for both adapters and monitors is maintaining
the higher horizontal frequency at screen resolutions beyond SVGA
Resolution and Dot Pitch (DP)
How
"sharp" an image looks is determined by how many pixels (dots) the
image is made comprises, and how large the dots are. The best combination to
create a really sharp image is a high resolution with a low dot pitch (DP).
Resolution depends on the video adapter, software and monitors all working
together; the dot pitch depends on the monitor alone. Manufacturers use a
couple of different approaches to defining dot pitch, but it basically defines
how large each pixel or dot on the screen ends up being. Fourteen-inch monitors
should have a .28 DP, while larger monitors range from DPs of .25 to .31. A 14"
monitor with a high dot pitch, say .39, is cheaper, but image definition is
poor. The trade off on resolution is a given image displayed at two different
resolutions will appear sharper at the higher resolution, but larger at the
lower resolution. Most people run their 14" SVGA monitors at VGA
resolution for this reason, although it's nice being able to switch to a higher
resolution when you need to. If you want easily readable screen fonts
(characters) at SVGA resolution, consider a 17" monitor.
Mice and Other Pointing Devices.
Mice can be
purchased for anywhere between $5 to $100. The mouse you receive with any
system bought as a whole is going to be the $5 model. Unless you do a lot of
desktop publishing or other graphics work and want a special "feel"
or extra control software with the mouse, the cheap version works fine. A mouse
is normally connected to the system box via a Com port, normally Com1, but
there are two other methods. The first method, used in brand name machines
only, is via a special mouse port. This is normally located next to the
keyboard connector. The second approach, popular in the early nineties, is
called a "bus mouse." In this approach, the mouse requires its own
adapter card, and is plugged into a special port on this card. Other pointing
devices include pen pointers, trackballs and joysticks, like those used in
video games. Artists and draftsmen, who need to position lines down to the
thousandth of an inch or lower, use digitizer pads, which start around $200.
The user either draws on this pad with a special instrument like a pen, or uses
a mouse like device that sports a cross hair for precise positioning.
Printers
People have
been experimenting with ways to reproduce words since Guttenberg printed the
Bible over 500 years ago. That's the long way of saying there are at least a
dozen technologies that have been widely used at one time or another for
computer printers. We'll limit our consideration to the big three; Dot Matrix,
Laser and Inkjet. All three types of printers are available as color or black
and white, with color inkjets representing the happy medium between price and
quality for color printing. Prices range from $100 for a cheap dot matrix to
over $10,000 for a production color laser.
Dot Matrix Printers
Dot matrix
printers have been around for over 25 years, so most of the bugs have been
worked out. The two characteristics that describe dot matrix printers are the
number of pins in the print head , 9 pin or 24 pin, and the width of the
carriage; "narrow" or "wide." The cheapest printer is the
narrow carriage 9 pin, and the most expensive is the wide carriage 24 pin. The
width of the carriage simply refers to how wide the paper path is, where the
narrow carriage handles the standard 8 1/2" by 11" paper. The number
of pins determines how close to "letter quality" the printing will
look. The dots in the individual letters printed by a 9 pin dot matrix will be
obvious, while a 24 pin printer on its slow "near letter quality"
setting will produce much nicer print.
The print
quality of any dot matrix printer can't compete with that of inkjets or lasers,
but they maintain a market niche where carbon copies or labels are used. Dot
matrix printers normally come with both tractor and friction feed, chosen by a
lever on the side. Tractor feed uses paper with holes along the edges for
sprockets to pull the printer, while friction feed works like an old fashioned
typewriter. Dot matrix printers are also rated by their speed in Characters per
Second (CPS). The CPS in draft mode (not very pretty) is always much higher
than the CPS in "near letter quality" mode. The consumable (computer
lingo for a part requiring regular replacement) for dot matrix printers is the
ribbon cartridge, which can cost between $3 to $20 or more. Expensive dot
matrix printers called "line printers" are used for jobs like
addressing bills or making out checks and can cost thousands of dollars.
Inkjet Printers
Inkjet
printers are the newest addition to the printer family, and operate by shooting
a stream of ink drops at the paper where they rapidly dry. Older model black
and white inkjets can be had for around $125 while color models start around
$200. All inkjets suffer from being slow, often turning out less than one page
per minute. The advantages that inkjets hold over dot matrix printers is their
ability to turn out good looking output, including graphics. The more expensive
color inkjets can do a pretty good job with photographic images when printing
on specially treated paper. The consumable for inkjet printers in the ink
cartridge, which averages about $20. The inkjet market, both the printers and
the consumables, is dominated by Hewellet Packard, which also has the lions
share of the laser printer market.
Laser Printers
Laser
printers operate along the same lines as copying machines, except they have a
lot fewer moving parts and are much more reliable. The two measures of
performance for a laser printer are the number of dots per inch (dpi) and the
number of pages per minute printed (ppm). Older lasers printed 300 dpi, which
produces much better print than any dot matrix or inkjet. New lasers can print
at 600 and 800 dpi, which is noticeably sharper when viewed through a
magnifying glass. A slow laser printer will average about 4 ppm, middle of the
road lasers manage 8 ppm, and expensive shared lasers used in office settings
often print over 20 ppm. Cheap lasers without paper trays start under $400, a
decent office quality laser costs about twice that amount.
Options that
add to the functionality and expense of a laser are PostScript compatibility, a
software enhancement developed by Adobe that is required by some desktop
publishing and artists software, and additional RAM for temporarily storing the
images to be printed. The main consumable for laser printers is the toner
cartridge, costing any between $10 to $200 dollars, depending on the life span
and print engine. Image drums, which start around $100 for rebuilts to a couple
hundred dollars for various new models, have longer lifetimes than toner cartridges,
but also require occasional replacement. Recycled replacements are available at
savings. Pricing and lifetime of laser consumables should be considered when
comparison-shopping laser printers.
Scanners
Scanners are
used to digitize (change into computer codes) photographs, artwork and
documents. The resulting digitized image can be used to display the original on
a monitor, reproduce it on a printer, or in the case of documents containing
typed quality words and numbers, to read them. Changing the image of a document
into actual words and numbers that can be used in a word processor or
spreadsheet is called Optical Character Recognition (OCR). Scanners see images
as either color or "gray scales," which convert the image into shades
of gray varying from white to black. Color scanner prices vary from a couple
hundred dollars for hand held roller scanners to tens of thousands of dollars
for commercial models in the publishing industry. The most popular models are
"flat bed" scanners, where a sheet of paper or photograph is laid
flat to be scanned. A decent flat bed color scanner costs between $150 to $600,
and comes with software and an adapter card. Inexpensive gray scale scanners
lost out to color scanners when the prices came down, and don't really have any
value in the second hand market. High-end gray scale scanners, costing from
several thousand to almost one hundred thousand dollars are used for processing
large numbers of documents for archiving or OCR. The most expensive of these
can scan over 100 pages per minute, compared to the one or two pages per minute
achieved by inexpensive flat beds.
Scanners use
the same "dots per inch" dpi figure used by laser printers. Most
scanners are capable of scanning at resolutions from 75 to 300 dpi, according
to software settings. New scanners, even inexpensive models, can scan up to 600
dpi, and produce images that appear to be 1200 dpi using software tricks. High
resolution scanning is important for photographs or artwork that will be
reproduced later, but most OCR works fine at 200 dpi. Color scanners also have
graded ability to reproduce colors expressed in bits of depth. Any newer
scanner will manage 24 bits deep, while 30 bits deep or higher offers more
accuracy and control. Most people who aren't professional artists or publishers
will be happy with a $400 flatbed scanner that offers 24 bit color and 300 dpi.
Speakers and Microphones
Speakers,
which require the presence of a sound card in the system box to be of any use,
can be a little different from the speakers on your stereo. In order to play
music at a reasonable volume from your sound card, you will need to run the
output through an amplifier, or purchase amplified speakers. Some amplified
speakers come require batteries; others come with a transformer that can be
plugged into a wall outlet. Good amplified speakers, costing between $20 to
$100, can make the CD player in your computer sound like a stereo, and add
tremendously to the multimedia experience. Cheap speakers often come free with
the sound card, but their volume is limited to a level around spoken
conversation, and the fidelity is terrible. The microphone supplied with most
sound cards works well enough, but is usually the clip on type.
Electrostatic Discharges
Electrostatic discharges (ESD) are the most severe form of electromagnetic interference (EMI). The human body can build up static charges that range up to 25,000 volts. These build-ups can discharge very rapidly into an electrically grounded body or device.
Human Voltage
Most computer components use 3 to 5 volts. A discharge as low as 30 volts can
be damaging to a computer component. A human placing a 25,000-volt surge through
any electronic device could be devastating to the device. When people move, the clothes they are
wearing rub together and can produce large amounts of electrostatic charge on
their bodies. Walking across carpeting can create charges in excess of 1,000
volts.
Causes of ESD
Here are the most common causes of ESD are moving people, low humidity,
improper grounding, unshielded cables, and poor connections.
ESD and Humidity
ESD is most likely to occur during periods of low humidity. If the relative humidity is below 50%,
static charges can accumulate easily. ESD generally does not occur when the
humidity is above 50%. Anytime the
charge reaches around 10,000 volts, it's likely to discharge to grounded metal
parts.
ESD and IC Devices
Although ESD won't hurt humans; it will destroy certain electronic devices. The
high-voltage pulse can burn out the inputs of many IC devices. This damage may
not appear instantly. It can build up over time and cause the device to fail.
Minimizing Risk of ESD
To minimize the chances of damaging MOS devices during handling, special
procedures have been developed to protect these devices from static shock.
Integrated circuits (ICs) are generally shipped and stored in special
conductive plastic tubes or trays. You
may want to store MOS devices in these tubes. You may ensure a MOS device's
safety by inserting the IC's leads into aluminum foil or black conductive foam
(not Styrofoam).
Transporting PC Boards
PC boards containing static-sensitive devices are normally shipped in special,
antistatic bags. These bags are good for storing ICs and other computer
components that may be damaged by ESD. Antistatic bags are also the best
container that you can use to transport PC boards that have static-sensitive
components.
Grounding Straps
Professional service technicians employ a number of precautionary steps when
they are working on systems that may contain MOS devices. One of the main
precautionary steps is the use of a grounding strap.
When Not to Wear Them
You should never wear antistatic straps while working on higher-voltage
components such as monitors and power supply units. Doing so could result in a
potentially lethal amount of voltage passing through your body.
|
|
Some technicians wrap a copper wire around their wrist or ankle and connect it to the groundside of an outlet. Do not attempt this. |
Antistatic Mats
Most technicians' work areas also include antistatic mats made out of rubber or
other antistatic materials that they stand on while working on the equipment.
Touching the Chassis
Computers and peripheral systems may contain a number of static-sensitive
devices. Before touching any components
inside the system, touch an exposed part of the chassis or the power-supply
housing with your finger. Grounding yourself in this manner ensures that any
static charge present on your body is removed. You should be aware that this
technique will only work safely if the power cord is attached to a grounded
power outlet. The ground plug on a standard power cable is the best tool for
overcoming ESD problems.
What
Is a Ground?
The term ground actually encompasses a collection of terms. Generically, ground is just any point from
which electrical measurements are referenced.
Grounding
ICs
The signal ground point isn't too difficult to find in a circuit board full of
ICs. Most DIP-style chips use the highest-numbered pin for the positive supply
voltage, and the last pin on the pin-1 side of the chip as the ground pin. Some caution should be used with this assumption,
however, because not all ICs use this logic for ground.
Limiting EMI
Grounding is an important aspect of limiting EMI in computer systems. Left
unchecked, EMI can distort images on the video display, interfere with
commercial communication equipment such as radios and televisions, and corrupt
data on floppy disks.
Effects of EMI
In addition, EMI can cause signal deterioration and loss when cable is
improperly routed. If a signal cable is
bundled with a power cable, radiation from the power cable may be induced into
the signal cable, affecting the signals that pass through it. Unlike ESD, which is destructive, the
effects of EMI can be corrected without damage to computer components.
Electrical Storms
Because the computer system is connected to an actual earth ground, it should
always be turned off and disconnected from the wall outlet during electrical
storms. This includes the computer and
all of its peripherals.
Radio Interference
A tight fit and electrical conductivity between the case and top are necessary
to prevent unwanted radio interference from escaping the interior of the case.
PC MOTHERBOARDS
The motherboard is the board that contains the logic circuits that tie all parts of your PC together. It provides the connectors for the CPU, the memory, BIOS, CMOS, Video devices, sound devices, storage devices, chipsets, etc. in order to form an integrated set of components.
Here is a list of WEB sites of motherboard
manufacturers you can check out:
www.micronics.com
www.asus.com
www.abit.com
www.Aopen.com
www.Soyo.com
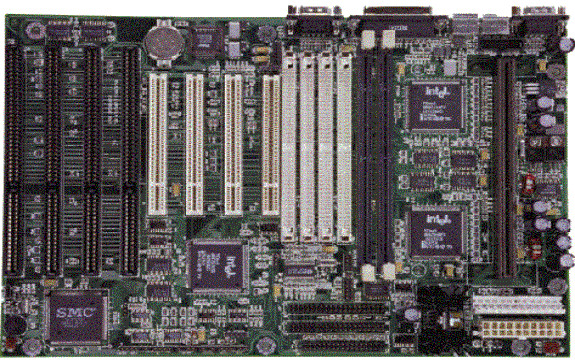
This illustration is just to show what a
motherboard looks like. It has each of the following components, and a lot
more. The problem is to tell you where each of them are:
ISA Expansion Slots (4 - long black slots at upper left)
PCI Expansion Slots (4 - mid length white slots in middle)
Pentium II CPU Slot (long slot near right edge)
Memory (SIMM) bank (4 white slots to right of PCI slots).
Memory (DIMM) bank (2 gray/black slots to right of SIMM slots).
CPU (Microprocessor)Slot - (lower right, 2nd from bottom)
External Cache (L2) (integrated into Pentium II CPU)
ROM Chip (BIOS Chip)
Clock Oscillator
The above illustration is a real motherboard, a Micronics "Stingray" System Mother board. On older PCs, you may not be able to view all details. It has a socket for PentiumII 200/233/266/300/350/400/450 MHZ processors (long slot upper right corner); 4 16-bit ISA slots (left side), 4 32-bit PCI slots(white slots in center) and 1 shared PCI/ISA slot (right); 5 32 bit EISA slots (upper right - brown slots); 4 64-bit, 168-pin DIMM sockets (for a possible 1 GB maximum memory); and much, much, more.
The board shown provides 8 expansion slots! It
also has a "Universal Serial Bus" port! It has a high speed CPU slot
(233, 266, and 300/350/400/450 MHz), and serious memory and L2 cache available.
These are selling points for the future.
The motherboard also contains other components
such as BIOS chips, the CPU clock, cache chips, bus, etc. To see every detail,
you will need to get a "User's Manual" for the specific motherboard
you have, and to locate all components on the board. The bus is actually a set
of circuits that run throughout the board and connect all the expansion slots,
memory, and CPU, etc. together. This photo does not contain enough detail to
specifically show you the bus.
Motherboards sizes are as follows:
Standard AT = 12" w x 13.8" long
Baby AT = 8.57" w x 13.04" long
LPX = 9.0" w x 13.0 long
ATX = 9.6" w x 12.00 long
Sizes are important if you are replacing an
existing motherboard!
The ATX is the Intel specification released in
July 1995. It has become the defacto industry standard for motherboards. The following drawing will help you to
visualize the bus:
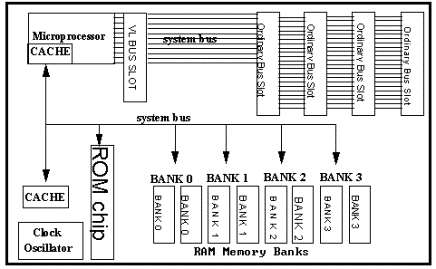
The motherboard components serve specific
functions:
BUS - connects all the components of the computer and provides a path from device/controller to the next component.
Expansion Slots - for connecting other devices/controller cards to the motherboard.
Memory Slots - provides receptacles for adding additional memory chips (SIMMs, DIMMs, or other types of memory).
ZIF Socket - provides a location to insert the heart of the computer - the CPU.
BIOS Chip - provides a definition of the system for booting.
USB Port - some newer machines will have a port for the Universal Serial Bus (USB) connection.
Chip Set - controls most of the capabilities such as type of memory, I/O, etc.
PC MEMORY
MEMORY is only one of
the required hardware components of a PC. It is not more important, nor less
important than the other components of your PC. But much of our modern day
software will not operate efficiently, if at all, without lots of memory.
MEMORY is a
term that is used to represent storage that has "almost"
instantaneous access by the CPU or other processor. Every computer will have
some type of memory. However, the memory we speak of the most often is Random
Access Memory (RAM). RAM is the primary memory used when we "boot"
(start up) a microprocessor and the PC's operating system and device drivers
are loaded into RAM.
RAM has many
functions, but its primary function is to store programs and drivers for the
various system devices. It is probably the most important type of memory in
your PC.
We will
discuss three types of memory:
RAM, ROM, CACHE
When you
enter a command from your keyboard, the CPU (microprocessor) processes the
command and calls for data (a program or data file) to be copied from a storage
device (hard disk, floppy, CD-ROM, etc.) into memory, where it is stored
temporarily until the CPU needs it. The memory then provides the data to the
CPU more quickly than from the storage device. This data may be a program and
actual data. This bulk memory is called "RAM", and is what you are
referring to when you say "my system has 32 Megs of memory".
The RAM is divided into multiple parts (locations, not types):
Conventional Memory (location 0 thru 640 KB)
High (Upper) Memory (641 thru 1 MB)
Extended Memory (addresses above 1 MB)
Expanded Memory (sometimes).
RAM, itself,
usually consists of Dynamic Random Access Memory (DRAM). DRAM has
several variations (such as FPM RAM, EDO RAM, and SDRAM) of chips mounted on
Single In-Line Memory Modules (SIMM) boards or chips, or on Dual In-Lin memory
modules. A single 30-pin SIMM can hold up to 4MB and a 72-pin SIMM can hold up
to 32 MB of memory. I think I am right in saying that a 168-pin DIMM chip can
contain up to 256MB of SDRAM.
Numerous
"types" of memory exist and your specific PC may contain several
types of memory for different purposes. Some of the terms you will hear are: RAM,
DRAM, SRAM, EDORAM, SDRAM, ROM, PROM, EPROM, EEPROM, FLASH, internal and
external cache, etc.
|
Memory Type |
Use |
|
ROM |
BIOS, CMOS, Special function Chips. |
|
Main Memory - FPM RAM, EDO & BEDO RAM, Synchronous DRAM (SDRAM) |
|
|
Chips on SIMM boards or Motherboard (Main Memory)-DRAM is actually FPM, EDO RAM, or SDRAM on a chip. |
|
|
Static RAM, used as External (L2)CACHE. L2 SRAM is on chips. L2 On-board cache is in the CPU chip. It comes in 3 basic types - Async SRAM, Sync SRAM, and PB SRAM (Pipelined Burst RAM - the fastest). |
|
|
FPM |
Fast Page Mode RAM used in 486 or before style motherboards. I think it is normally 30 pin SIMMs, but may also be on 72 pin SIMMs in some Intel Pentium based systems. The 70ns access time will work with the older, slower 486 CPUs, but for a system with bus speeds of 66MHz, you will need the 60ns speed SIMMs. |
|
EDO RAM |
Extended Data Out RAM Memory used on Pentium or later type motherboards. EDO RAM is not designed for 486 or earlier motherboards. EDO RAM is on 72-pin SIMMs. EDO RAM comes in plain EDO and Burst EDO (BEDO RAM) versions. EDO and BEDO RAM are ok in systems with bus speeds up to 66MHz. |
|
SDRAM |
Synchronous DRAM (Pentium w/MMX has SDRAM as main memory). SDRAM memory is on 168-pin DIMM chips. SDRAM comes in several types with speeds from 10, 15, 20, and 25 nanoseconds. |
|
FLASH |
Normally, it is memory on a card. The size of a PCMCIA card. |
Keep in mind that DOS was originally designed to run with an 8086 processor; a processor limited to addressing 1 MB of total memory. Of that 1 MB of memory, some of it had to be set aside for system information such as addresses used for video, expansion cards, and other system components. By design, MS-DOS is limited to 640 KB of memory.
There are four specific areas of memory: conventional, upper memory area, expanded and extended.
Conventional Memory
We know that the 8086 processor could address 1 MB (1024KB) of memory and part of that memory had to be set aside for system addresses. Therefore, DOS was designed to work with only 640 KB of memory.
This first 640 KB of system memory is commonly called conventional memory. It is also referred to as base memory. It is used to load the DOS command processor, memory resident programs (TSRs), and device drivers. Traditionally, this was the only memory available to DOS applications. So when a DOS application is launched, it too occupies this area of memory.
Upper Memory Area
(UMA)
So we have seen what the first 640 KB of memory is used for, but as we said, the earlier processors could address 1 MB (1024 KB) of memory. What is the other 384 KB used for? This area is reserved for system components. That's why the Upper Memory Area is also know as "Reserved Memory."
Located between 640 KB and 1 MB, the Upper Memory Area (UMA) contains the ROM BIOS, device controller ROM, and video controller ROM and RAM. Shadow RAM uses this memory area to shadow the ROM BIOS instructions and hardware devices can store their program code here. When supporting expanded memory, it will also contain the expanded memory page frames.
Upper Memory Blocks
(UMB)
Upper Memory Blocks (UMB) are free areas within the UMA. UMBs can be used to contain device drivers and memory resident programs (TSRs). Access to UMBs requires an extended memory manager such as HIMEM.SYS and a UMB manager such as EMM386.EXE loaded.
Expanded Memory (EMS)
Expanded Memory (EMS) uses an expanded memory card placed in an expansion slot. It is basically just a card with memory chips on it. Using an application written to work within the LIM Expanded Memory Specification (EMS), data can be stored in the expanded memory area for later access. When needed, the data stored in expanded memory is moved to the system memory area by "paging" the data through a window, or page frame, created in the
Upper Memory Area.
The page frame is 64 KB in total size and is made up of four 16 KB pages. Since DOS assumes all applications are running in the Conventional memory area, you must use an expanded memory manager in order for this technique to be successful. It is the expanded memory manager's job to keep track of what data is placed where in the expanded memory area. The DOS expanded memory manager is EMM386.EXE.
Extended Memory (XMS)
With the debut of the 80286 processor came the ability to address 16 MB of memory. Memory above 1 MB (1024 KB) is called extended memory (XMS.) This is physically limited to 16 MB for 80286 microprocessors and 4 GB for 80386 and above microprocessors.
Unfortunately, systems running DOS are not able to directly access this memory. Remember DOS only recognizes 640 KB. To make full use of this memory, a user must have an operating system written to access this range, such as Windows 95, Windows NT or OS/2, or they must use an extended memory manager.
You must load HIMEM.SYS, or its equivalent, as part of CONFIG.SYS to make extended memory available. HIMEM.SYS must be loaded before any other memory drivers or programs that use extended memory.
High Memory Area
(HMA)
The first 64 KB of Extended Memory (address range 1024 KB - 1088 KB) has a special name, the High Memory Area. An XMS driver, such as HIMEM.SYS, is required for DOS to use the HMA. It is commonly used for loading of DOS components, but may be used for a different memory resident program. However, only one program at a time may reside in the HMA.
Virtual Memory
Virtual memory is physically a file on the hard disk that emulates physical RAM. A swap file is created on the hard disk. This may be either a Temporary or Permanent swap file. A portion of program and data will be kept in RAM at all times, with the rest being swapped out to the hard disk. When an attempt is made to access code or data residing on the hard disk, it is swapped back into RAM. If necessary, other code or data will be swapped out to make additional room available. This process is controlled by the VMM (Virtual Memory Manager). Except for a loss of performance when swapping occurs, virtual memory use is transparent to both the user and the application.
HOW MUCH RAM MEMORY DO YOU NEED?
No one can
say exactly - you need to know things about your system operating system, the
type of applications you will run on your PC (graphics, multi-media, word
processing, etc). Let me give you a few hints:
|
Quantity |
GENERAL USES |
|
4 MB |
DOS applications, maybe Windows 3.1, a few old word processing packages, etc. |
|
8-12 MB |
Windows for Workgroups, small word-processing, E-Mail, only a few (1 to 3) applications open. Maybe an Internet package such as Internet Explorer or Netscape, AOL, etc. Will be somewhat inefficient. |
|
12-16 MB |
Windows for Workgroups, supposedly Windows 95 (not really!), Word processing, E-Mail, WEB interfaces, FAX, spreadsheets, and low level graphics applications. Few applications open simultaneously. |
|
16-24 MB |
You can now load Windows NT Server, Windows NT Workstation, and Windows 95. NT Server works inefficiently at this level. Some number crunching, spreadsheets, E-Mail, WEB browsers, some graphics and audio-visual (but weak). |
|
24-32 MB |
Now you can do heavy applications. Spread sheets, statistical analysis programs, large databases, and multiple applications open. Even a little graphics and games - a an acceptable speed. |
|
32-64 MB |
Starting into decent graphics, with word processing, page layouts, even some good "audio visual" type applications. |
|
64-128 |
You are now read for medium to high level graphics and animation - if you have the other necessary hardware. Photo editing, multimedia, word processing, illustration graphics, the whole nine yards! |
|
128+ MB |
Now you are talking! This is the level for efficient Windows NT Servers with many users. Multimedia and about everything else! |
Just
remember this: You can have all the RAM memory you can install; but, if you do
not have adequate internal and external cache, good video cards, a 32-bit or
64-bit bus, etc., you will still operate somewhat slower.
Video Types
There are several major types of video,
v Monochrome,
v EGA/CGA (Enhanced Graphics Adapter,
v Color Graphics Adapter),
v VGA (Video Graphics Adapter),
v SuperVGA(Super VGA), and
v XGA (Extended Graphics Array).
Monitors
Monitors have two main characteristics, the dot pitch and the
refresh rate. The dot pitch is described in millimeters (mm) and describes
shortest distance between two dots of the same color. For example, a lot of
present day monitors will have a 0.28 mm dot pitch, anything lower than that
(such as 0.25 mm) is superior, anything larger (such as 0.31 mm) is less
quality.
The second way to describe a monitor is in its refresh rate. The
refresh rate (also know as vertical scan frequency) measures how many times per
second the monitor is scanned. VGA has a standard refresh rate of 60 Hertz, or
in other words, refreshes itself 60 times per second. The higher the number,
the more times per second the monitor is being refreshed, which means less
flicker is being perceived.
There are two types of monitors, CRT and LCD. CRT is Cathode Ray
Tube and LCD is Liquid Crystal Display. LCD screens are mainly used in Laptops,
though are appearing in desktop models every day.
Each of these different types of video support differing numbers of
colors and resolutions.
|
Video Type |
Colours Depth |
Resolution |
|
Monochrome |
Mono |
720X350 |
|
CGA |
4 |
320X200 |
|
EGA |
16 |
640X350 |
|
VGA |
16 |
640X480 |
|
SVGA |
16 |
1024X768 |
Printers
Printers is a large
part of the A+ Certification Core Exam and there are several sections that I
guarantee will be on the exam. The most important part of the laser printer
section is the order in which a laser printer operates, it will be at least one
question on the exam.
Laser Printers
Laser printers, also
referred to as page printers, receive their information one page at a time and
print using electrostatic charges, toner, and laser light.
The laser printer has
several Field Replaceable Modules, including the Toner Cartridge, the Laser Scanning
Assembly, High Voltage Power Supply, DC Power Supply, Paper Transport Assembly,
Transfer Corona Assembly, Fusing Assembly, and the Formatter Board.
The EP Toner
Cartridge holds the toner which is eventually what is printed onto the page.
Toner is sensitive to the electrostatic charges. The Toner Cartridge also
contains the print drum, charge corona wire, and the cleaning blade. The print
drum is has a photosensitive material on it which holds static charge when it
is not exposed to light. The charge corona wire charges the drum, while the
cleaning blade does exactly what its name suggests, it cleans the used toner
off the drum.
The Laser Scanning
Assembly holds the laser which shines its light on certain parts of the printer
drum. The electrical charge is reduced and the toner attaches itself to the
drum where the laser has shined.
The High Voltage
Power Supply takes 120 V AC and converts it to higher voltages for the charge
corona wire and transfer corona wire. The DC Power Supply produces +5 Volt DC,
-5 Volt DC, and +24 Volt DC from household current.
The paper transport
assembly moves the paper through the printer. It is a series of motors and
rollers to move the paper.
The Transfer Corona
Assembly charges the paper with a positive charge as it moves through the
printer. Once charged, it picks up the toner from the photosensitive drum.
The Fusing Assembly
(also known as the fuser) applies pressure and heat to the paper to seal the
toner particles to the paper. In the process of fusing, there is a halogen lamp
which heats up to about 350 degrees F.
The Formatter Board
is the circuit board that controls everything that is going on in the printer.
It formats the information then tells the different modules to function
together to get the printed page across.
Order of Processes
The following is the
order of processes that occur in a laser printer:
1. Cleaning - the EP
Drum is cleaned with a rubber blade.
2. Conditioning - the
EP drum is given a negative charge of about -600 Volts by the primary corona wire
3. Writing - A laser
beam writes to the EP Drum, this laser causes portions of the drum to become
almost positively charged
4. Developing - Toner
is applied to the drum by the particles being transferred to the areas of
positive charge
5. Transferring - The
Transfer Corona wire charges the paper with a positive charge, the EP drum
turns as the paper runs beneath it
6. Fusing - the paper
runs through the Fusing Assembly which is heated to 350 degrees F, the toner is
fused onto the paper
Other Notes
The ozone filter
should be replaced during maintenance.
Dark spots on paper
could indicate loose toner particles, run a few pages through to clear it up.
The primary corona
has the highest negative charge in a printer.
Always check the
leading edge of paper when there is a paper jam, it can indicate what part of
the printer is causing the jam.
The drum is
photoconductive and loses its charge when light hits it. It is normally
negatively charged during the print process.
The transfer corona can cause the print to be too
light.
Dot Matrix Printers
Dot matrix printers
are a form of impact printer. The printhead in a dot matrix printer is a series
of pins which form numbers, letters, and graphics as it passes over the paper.
In early dot matrix printers, 9-pin was a common size of printhead. This was
called a draft quality printer. Later versions, such as the 24-pin printhead,
print in near letter quality (NLQ) print mode.
During preventative
maintenance, never lubricate the printhead of the printer. A tight ribbon could
be the cause for flecks and smudges on the paper. Also, a missing or broken
printhead pin could cause incomplete printing. If the print density is erratic,
there can be a problem in the advancement of the printer ribbon.
Bubble jet (Inkjet)
Printers
Inkjet printers spray
ink onto the page to form the letters and graphics. The inkjet printer has an
ink cartridge which contains several chambers of ink. When the ink runs out,
you must replace the ink cartridge. It is not recommended to refill ink cartridges.
Networks
Types
- Ethernet
- Token Ring
- ArcNet
- AppleTalk
Bus Types
|
ISA 8-16 bit PCI – 32 bit self configuring irq above 15 PCMCIA (PC card laptop) |
MCA – not many around Nubus is apple bus type |
Media Types
COAX, UTP, STP, Fiber Optic, Infrared, Radio
Coax – BNC connectors
UTP – RJ45 connector
Token ring – 9 pin D connector or RJ45 connector
Media Concerns
v Cost
v Ease of Installation
v Bandwidth capacity – larger documents etc
Node capacity – how we want to connect, how many we can have
Digital Signals
- Baseband all of the signal, normally used for network connections
Analog
- Broadband shares media bandwidth with other channels, uses part of entire signal
- Everything in computer is digital so slows down because of conversion
Hints for setting up your cards - C049.avi
- Set IRQ same on every card
- Make I/O port unique, but same on every card.
- I/O port address – address of information like a Post office box (in header)
- Ram address is where the BIOS address resides.
As system gets info off the card, it has to know where to find it. It uses the I/O port address to find the card where to get the BIOS address, but then it needs the actual bios info. Some BIOS are preset, but some you have to setup.
Settings on the card - C048.avi
3 settings - IRQ, I/O, Ram
- Some manual some Plug and Play.
- Each has to have a unique setting
IRQ – it basically request to system to speak
Choices of Network Card type for your system - C040
- Network Type
- Bus Type
Networking Essentials 70-58 Notes
The Networking Essentials exam requires you to answer 58 questions over a 75-minute period. The pass mark for the exam is 793 / 1000. Networking Essentials counts as one of the four 'core' exams required for MCSE, it covers quite a wide range of topics and there's a lot to learn so let's get started...
Networks, LAN's and WAN's
A network can be defined as "a group of interconnected computers that share information and resources". In it's simplest form, a network can consist of two computers communicating over a single cable.
The term LAN stands for Local Area Network. A LAN is a group of computers networked within an office, building or campus.
A WAN or Wide Area Network usually consists of computers in separate geographical areas interconnected by means of leased lines, telephone lines or microwave, radio and satellite links. A good example of a WAN could be a company with offices in two different cities whose LAN's share information over an ISDN line.
Network Topology
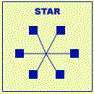
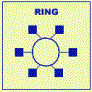
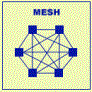
Bus Topology: Single cable connecting all computers on the network in a line
Star Topology: All computers on the network are connected directly to a central hub
Ring Topology: Each computer is connected to the next in a ring with no end to the network
Mesh Topology: Each computer is connected to every other computer on the network forming a mesh
Client/Server network vs. Peer-to-Peer network
Peer-to-Peer Network
In a peer-to-peer network all the computers on the network operate as equals (peers) that both share and use resources. Essentially, each computer is both a client and a server. Every computer is responsible for managing it's own shared resources. Peer-to-peer networks are usually quite small and generally consist of 10 or fewer computers. Peer-to-peer networks usually implement share-level security.
Windows 3.11 for Workgroups, Windows 95/98 and Windows NT Workstation can operate in a peer-to-peer network.
Advantages include: low cost, easy to set up & no need for centralized administration
Disadvantages include: poor security, limited growth & requires more knowledgeable users
Client/Server Network
In a server based network large numbers of client computers request and use resources from a smaller number of higher performance server computers. The server-based network is usually managed centrally by a network administrator. Server based networks implement user-level security.
Windows NT Server is used to build a server-based network. Windows 95/98 and NT Workstation can act as clients in a server based network. NOTE: NT Server supports an unlimited number of connections but NT Workstation can only support a maximum of 10 concurrent connections.
Advantages include: Strong security, centralized management of large number of users & potential for growth
Disadvantages include: Expensive to set up, more difficult to set up & usually requires a dedicated network administrator
User-Level security vs. Share-Level
The two basic security models covered by the Networking Essentials exam are share-level security otherwise known as password-protected shares and user-level security often referred to as access permissions. Before we continue, you need to be aware of the term resource. A resource can be any device (e.g. a printer) or information (e.g. data files) on the network. When a resource is available for use on the network we can call it a shared resource.
Share-Level Security
In the share-level security model each shared resource on the network is assigned a password. In order to gain access to the resource a user must enter the correct password for that resource. A 10 user Windows 95 peer-to-peer network is a good example of a network that implements share-level security.
User-Level Security
Some network operating systems such as Windows NT Server use a more advanced and flexible security model called user-level security. Rights and permissions to shared resources on the network are assigned on a user-by-user basis. To gain access to shared resources a user must first log on to the network by supplying a valid username and password. When a user attempts to access a shared resource the server will validate the user and grant access to the resource based on the permissions associated with the user for that resource. A 50 user NT Server based network with Windows 95 and NT Workstation clients with users managed centrally on the server is a good example of a network using user-level security.
Networking Essentials 2
1. IRQ (Interrupt Requests)
IRQ 1 Keyboard IRQ 2(9) Video Card IRQ 3 Com2, Com4 IRQ 4 Com1, Com3 IRQ 5 Available IRQ 6 Floppy Disk Controller IRQ 7 Parallel Port (LPT1) IRQ 8 Real-time clock |
IRQ 9 Redirected IRQ2 IRQ 10 Available IRQ 11 Available IRQ 12 PS/2 Mouse IRQ 13 Math Coprocessor IRQ 14 Hard Disk Controller IRQ 15 Available |
2. Standard Topologies
Bus - A single cable (trunk) that connects all computers in a single line.
Star - Computers connect to a centralized hub via cable segments.
Ring - Connects all computers on a single cable. Ends are not terminated, but form a full loop connecting the last computer to the first computer.
Mesh - Commonly used in WAN configurations. Routers are connected to multiple links for redundancy and to give the ability to determine the quickest route to a destination.
3. Access Methods
CSMA/CD - Collision Detection; listens to cable prior to sending data. (Ethernet)
CSMA/CA - Collision Avoidance; Announces intention to send data. (AppleTalk)Token-Passing - Token revolves around ring, computer which has token is permitted to send data. (Token Ring)
4. IBM Cabling System
Thinnet Coaxial - .25 inches thick, carries signal 185 meters. Known as RG-58 family, and has a 50 ohm impedance. RG-58 /U - Solid Copper Core RG-58 A/U - Stranded Wire Core RG-58 C/U - Military Specification of RG-58 A/U RG-59 - Broadband transmission (Television Cable) RG-62 - ArcNet Network Cable - When troubleshooting thinnet coaxial cable, the cable terminator must read 50 ohms, and the cable and connector must measure infinite.Thicknet Coaxial - .5 inches thick, carries signal 500 meters. A transceiver (Vampire Tap) is used to make a physical connection with the Thicknet core.
Unshielded Twisted Pair - Twisted pair wiring, carries signal 100 meters. Is susceptible to crosstalk.
Shielded Twisted Pair - Twisted pair wiring, carries signal 100 meters. Has foil or braided jacket around wiring to help reduce crosstalk and to prevent electromagnetic interference.
Crosstalk - Signal overflow from one wire to another adjacent wire.
Attenuation - The degrading of a signal as it travels farther from its origination.
Jitter - Instability in a signal wave. Caused by signal interference or an unbalanced FDDI ring or Token Ring.
5. UTP/STP Category Speeds
Cat 2 - 4 mbps Cat 3 - 10 mbps Cat 4 - 16 mbps Cat 5 - 100 mbps Fiber-Optic - Carries light pulse signals through glass core at speeds of between 100 Mbps - 200,000 Mbps.
6. Ethernet Specifications
Type Cable types Connection Max Length 10Base2 - RG-58 thinnet coaxial cable BNC T 185 meters (607 ft) 10Base5 - Thicknet coaxial cable DIX/AUI 500 meters (1640 ft) 10BaseT - Category 3, 4, or 5 UTP cable RJ-45 100 meters (328 ft) 100BaseT - Category 5 UTP cable RJ-45 100 meters (328 ft)
7. Signal Transmissions
Baseband - Uses digital signaling over a single frequency. Transmits bi-directionally.
Broadband - Uses analog signaling over a range of frequencies. Transmits unidirectional and uses amplifiers for signal regeneration.
8. OSI Model – All People Seem To Need Data Processing
|
Application Layer |
Allows applications to use the network. Handles network access, flow control and error recovery. |
|
Presentation Layer |
Translates data into a form usable by the application layer. The redirector operates here. Responsible for protocol conversion, translating and encrypting data, and managing data compression. |
|
Session Layer |
Allows applications on connecting systems to establish a session. Provides synchronization between communicating computers. |
|
Transport Layer |
free delivery. Repackages messages into smaller packets, and handles error handling. |
|
Network Layer |
Translates system names into addresses. Responsible for addressing, determining routes for sending, managing network traffic problems, packet switching, routing, data congestion, & reassembling data. |
|
Data Link Layer |
Sends data from network layer to physical layer. Manages physical layer communications between connecting systems. |
|
LLC |
(802.2) Manages link control and defines SAP's (Service Access Points). |
|
MAC |
(802.3, 802.4, 802.5, 802.12) Communicates with adapter card. |
|
Physical Layer |
Transmits data over a physical medium. Defines cables, cards, and physical aspects. |
OSI layer Protocols residing here
Application SMB, NCP
Presentation NCP
Session None
Transport TCP, SPX, NWLink, NetBEUI
Network IP, IPX, NetBEUI, DLC, DecNET
Data Link None
Physical None
9. IEEE 802
Specifications
802.1 Internetworking
802.2 LLC (Logical Link Control)
802.3 CSMA/CD - Ethernet
802.4 Token Bus LAN
802.5 Token Ring LAN
802.6 MAN (Metropolitan Area Network)
802.7 Broadband Technical Advisory Group
802.8 Fiber-Optic Technical Advisory Group
802.9 Integrated Voice/Data Networks
802.10 Network Security
802.11 Wireless Networks
802.12 Demand Priority Access LAN, 100 Base VG - AnyLAN
10. LAN Enhancement
Components
Repeater - regenerates signals for retransmission. Moves packets from one physical media to another. Will pass broadcast storms. Cannot connect different network topologies or access methods.
Bridges - are used to segment networks. They forward packets based on address of destination node. Uses RAM to build a routing table based on hardware addresses. Will connect dissimilar network topologies. Will forward all protocols. Regenerates the signal at the packet level.
Remote Bridge - Same as bridge, but used for telephone communications. Uses STA (Spanning Tree Algorithm).
Routes - packets across multiple networks. Uses RAM to build a routing table based on network addresses (i.e. TCP address). Shares status and routing information to other routers to provide better traffic management and bypass slow connections. Will not pass broadcast traffic. Are slower than bridges due to complex functions. Strips off Data Link Layer source and destination addresses and then recreates them for packets. Routers can accommodate multiple active paths between LAN segments. Will not pass unroutable protocols.
Brouter - Will act as a router for specified protocols and as a bridge for other specified protocols.
Gateway - Used for communications between different NOS's (i.e. Windows NT and IBM SNA). Takes the packet, strips off the old protocol and repackages it for the receiving network.
Multiplexer Device - that can divide transmissions into two or more channels.
Switches - Hub with bridging capabilities. Switch filters traffic through MAC addresses. Creates sessions on ports within the hub. Used when upgrading to 100mb Fast Ethernet.
Repeater Physical
Bridge Data Link (MAC Sublayer)
Remote Bridge Data Link (MAC Sublayer)
Router Network
Brouter Data Link and Network
Gateway Transport, Session, Presentation and Application
Multiplexer Physical
Switch Data Link
Spanning Tree Algorithm - was developed for bridges to determine the most efficient network in path when there are multiple paths to choose from.
Multiplexing - Several signals from different sources are collected into the component and are fed into one cable for transmission.
11. Protocols
Routable - TCP/IP, IPX/SPX, OSI, AppleTalk, DecNET, XNS. Non-routable - NetBEUI, DLC, LAT.
NetBEUI - Microsoft protocol designed for small LANs; non-routable. Not compatible with UNIX networks.
IPX/SPX - Fast protocol for small and large Novell networks; is routable. Also known in NT as NWLink.
TCP/IP - Internet protocol; is routable. Used by UNIX networks.
DecNET - Defines communications over FDDI MANs; is routable.
AppleTalk - Apple protocol designed for small LAN file and print sharing; is routable.
RIP (Routing Information Protocol) - Routers use this to communicate with each other to determine the least busy and shortest network routes.
NDIS (Microsoft) and ODI (Novell) are used to bind multiple protocols to a network adapter.
SLIP (Serial Line IP) - Provides dial-up communications, but is unable to simultaneously transfer multiple protocols.
PPP (Point-to-Point Protocol) - Performs dynamic IP addressing, multi-protocol support, password login and error control.
Common TCP/IP problems are caused by incorrect subnet masks and default gateways.Incorrect frame types will cause problems between two systems using IPX/SPX.
12. Computer Name Resolution
DNS (Domain Name Services) - Used to resolve DNS host name to an IP address.
WINS (Windows Internet Naming Service) - Used to resolve NetBIOS computer name to an IP address.
HOSTS - File which contains mappings between DNS host names and their IP addresses.
LMHOSTS - File which contains mappings between NetBIOS computer names and their IP addresses.
Packet Switching - Packets are relayed across network along the best route available.
Beaconing - Computers are used to detect network faults, then transmit the fault signal to the server.
Packet Switching Networks Type FunctionX.25 Designed to connect remote terminals to mainframe host systems. Is very slow due to constant error-checking.
Frame Relay Point-to-point system which uses digital leased lines. Will provide bandwidth as needed. Requires frame relay capable bridge or router for transmission.
ATM Advanced implementation of packet switching. Transmits at speeds of 155Mbps to 622Mbps with capabilities of higher speeds. Transmits data in 53 byte (48 application, 5 header) cells. Uses switches as multiplexers to permit several computers to simultaneously transmit data on a network. Great for voice and video communications.
ISDN Transmits at 128k/sec. Has three data channels - 2 B channels @ 64k/sec & 1 D channel @ 16k/sec. The B channels carry data while the D channel performs link management and signaling.
FDDI 100 Mbps token-passing ring network which uses fiber-optic media. Uses a dual-ring topology for redundancy and in case of ring failure. Each ring is capable of connecting 500 computers over 100 kilometers (62 miles). Can be used as a network backbone. Uses beaconing for ring troubleshooting.
Security levels Share-level security - Used in Windows 95 to share resources. A password is needed to access the resource. User-level security - Used in Windows NT to share resources. When you attempt to access a shared resource, the server will make sure your user account has been authorized to access the resource.
13. Network Diagnostic Tools
Tool FunctionDigital Volt Meters (DVM) Measures voltage passing through a resistance. Primarily used for network cable troubleshooting.
Time-Domain Reflectors (TDRs) Sends sonar-like pulses to look for breaks, shorts or crimps in cables. Can locate a break within a few feet of actual fault.
Oscilloscope Measures amount of signal voltage per unit of time. Displays crimps, shorts, opens, etc.
Network Monitor Examines packet types, errors and traffic to and from each computer on a network.
Protocol Analyzer Look inside the packet to determine cause of problem. Contains built in Time-Domain
Reflector. Gives insights to many problems including connection errors, bottlenecks, traffic problems, protocol problems, etc.
14. Multiple Disk Sets
Fault Tolerant Systems protect data by duplicating data or by placing data in different physical sources. RAID FunctionLevel 0 Disk Striping -Divides data into 64k blocks and spreads it equally among all disks in the array. Is not fault tolerant.
Level 1 a Disk Mirroring -Duplicates a partition on another physical disk.
Level 1 b Disk Duplexing -Duplicates a partition on another physical disk that is connected to another Hard Drive Controller.
Level 2 Disk Striping w/ECC -Data blocks are broken up and distributed across all drives in array with error checking.
Level 3 Disk Striping w/ ECC stored as parity -Data blocks are broken up and distributed across all drives in array with one drive dedicated to storing parity data.
Level 4 Disk Striping with large blocks -Complete blocks of data are distributed across all drives in the array.
Level 5 Disk Striping with parity -Distributes data and parity information across all disks in the array. The data and the and parity information are arranged so they are always on separate disks. A parity stripe block exists for each row across the disk. The parity stripe is used for disk reconstruction in case of a failed disk. Supports a minimum of three disks and a maximum of thirty-two disks.
Windows NT supports RAID Levels 0, 1, and 5.Sector Sparing - Automatically adds sector-recovery capabilities to the files system while the computer is running. Available when using RAID methods. Only available with SCSI drives.
Upgrading the network To upgrade a network to 100 mbps Ethernet, you must perform the following:- Upgrade all hubs to switches or 100 mbps hubs. - Upgrade the wiring to CAT 5 UTP/STP. - Upgrade all network cards to 100 mbps.
How to install NT on a Large Hard-Drive
The motherboard BIOS must support and recognize drives
larger than 8 GB before NT can access the entire drive. Windows 95/98 and Windows NT can only share
FAT16 partitions.
If you are installing Windows 98 first, make sure that the first partition is
FAT16 [less than 2 GB]. NT will later be installed on the FAT16 partition. NT
3.5x and NT4 cannot access FAT32 partitions, which is the default for Windows
98.
The CD is Service Pack 1.
Download Atapi.sys from Microsoft.
FTP.MICROSOFT.COM/BUSSYS/WINNT/WINNT-UNSUP-ED/FIXES/NT40/ATAPI/ATAPI.EXE
Execute ATAPI.EXE and copy the ATAPI.SYS file to a diskette.
During the installation, when asked for additional devices, add the large drive by specifying the new device from the ATAPI.SYS diskette.
During the NT install, install NT on the existing FAT16 partition and LEAVE THE FORMAT INTACT.
Finish the NT installation.
When NT is fully installed:
START > PROGRAMS > ADMINISTRATIVE TOOLS > DISK ADMINISTRATOR
Select the cross-hatched end of the hard drive > CREATE PARTITION and ASSIGN DRIVE LETTER.
In Windows Explorer, format the new drive.
The CD is Service Pack 4.
Install NT on the existing FAT16 partition and LEAVE THE FORMAT INTACT.
Finish the NT installation.
When NT is fully installed:
START > PROGRAMS > ADMINISTRATIVE TOOLS > DISK ADMINISTRATOR
Select the cross-hatched end of the hard drive > CREATE PARTITION and ASSIGN DRIVE LETTER.
In Windows Explorer, format the new drive.
The Internet Gateways
Connecting all the users and individual networks together are Internet
Service Providers (ISPs). ISPs are
companies that provide the technical gateway to the Internet.
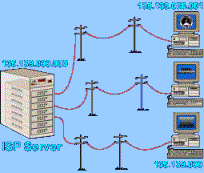
What's the Address?
These companies own blocks of registered access addresses that they assign to
their customers, to give them an identity on the network. These addresses are
called the Internet protocol addresses, or IP addresses.
Having a registered IP address makes each site a valid member of the Internet.
This is how individual users are identified to receive file transfers, e-mail,
and file requests.
IP Addresses
IP addresses exist in the numeric format of XXX.YYY.ZZZ.AAA. Each address
consists of four 8-bit fields separated by dots. This format of specifying
addresses is referred to as dotted decimal notation. The decimal numbers are
derived from the binary address that the hardware understands. For example, the
following network address:
10000111.10001011.01001001.00110110 (binary) corresponds to 135.139.073.054 (decimal).
ISDN Links
Other users, who require quicker data transfers, contract with the telephone
company to use special, high-speed Integrated Service Digital Network (ISDN)
lines. These types of links require a
digital modem to conduct data transfers. Because the modem is digital, no
analog conversion is required.
T1 and T3 Dedicated Connections
Users who require very high volumes will lease dedicated T1 and T3 lines from
the telephone company. These applications generally serve businesses who put
several of their computers or networks online
Metropolitan Area Networks
In some areas, high-speed intermediate-sized networks, referred to as
Metropolitan Area Networks (MANs), are popping up. These networks typically
cover areas up to 50 kilometers in diameter and are operated to provide access
to regional resources. They are similar to LANs in speed and operation but use
special high-speed connections and protocols to increase the geographical span
of the network — more similar to WANs
TCP/IP
The language of the Internet is Transmission Control Protocol/Internet
Protocol, or TCP/IP for short. No matter what type of computer platform or
software is being used, the information must move across the Internet in this
format. TCP/IP is now supported on virtually every brand of computing
equipment.
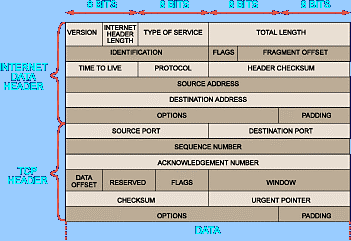 The
TCP/IP Packet
The
TCP/IP Packet
TCP/IP calls for data to be grouped together in bundles called network packets.
The TCP/IP packet is designed primarily to allow for message fragmentation and
reassembly. Packet information is conveyed through two header fields: the IP
header, and the TCP header, followed by the data field, as shown.
Domain Name System
The IP addresses of all the computers connected to the Internet are tracked
using a listing system called the domain name system (DNS). This system evolved
as a method of organizing the members of the Internet into a hierarchical
management structure. The DNS structure
consists of various levels of computer groups called domains. Each computer on
the Internet is assigned a domain name, such as tom.mclaughlin.net. Each domain name corresponds to an
additional domain level.
Names and Addresses
In addition to its domain name tracking function, the DNS system links the
individual domain names to their current IP address listings
Site Identifiers
In the example tom.mclaughlin.net the
.com notation at the end of the address is a major domain code that identifies
the user as a commercial site. The following list identifies the Internet's
major domain codes:
|
.com = Commercial businesses
|
.mil = Military establishments
|
![]()
Subdomain Names
The .net identifies the organization that is a domain listed under the major
domain heading. Likewise, the “.mclaughlin” entry is a subdomain of the “.net”
domain. It is very likely one of multiple networks supported by “.net”. The “tom” is the end user location. If the end user location is an e-mail
address, it is usually denoted by an ampersand (@) between its name and the
name of its host domain (that is, tom@mclaughlin.net
).
Windows NT 4.0 Profiles and Policies
Defining the user environment via Profiles and Policies
The document below has excellent information and links. This originally was on the http://www.usyd.edu.au/ web site but has since been removed. This has been reproduced by permission of Luke Brennan, co-author of the document.
This is a guide for experienced NT administrators having difficulties with Microsoft’s new implementation of System Policies in NT 4.0. Windows NT defines the user environment in two ways; Profiles and Policies, and as we all now know, completely different animals.
The profile defines the user environment within the parameters set by the system policy.
All users have a profile whether they like it or not. They may use the default profile, but they all have a profile. The system resources available to any user can be less than the system policy allows for that user but cannot be greater.
It also seems that the system will only update a profile if a change has been made to the profile defined in the login script. (not understood yet, so don't take this as hard fact - I think profile caching might be a key to this behaviour)
Many facets of Policy and Profile have been fixed in NT4.0 with the release of SP3. If you are not using this Service Pack, we strongly recommend that you do so.
Policies
A policy file can be thought of as a Registry Hive. If you keep that in mind, it might all click for you a bit faster!
The standard (default) Policy on your Server will contain at least two policy items. You can add others.
The first standard entry is Default Computer that equates to the Registry entries
under the HKEY_LOCAL_MACHINE
hierarchy.
Note: it would appear that this section of the target machine
registry gets recreated at each REBOOT.
The second standard entry is Default User that equates to the HKEY_CURRENT_USER hierarchy.
The implementation of domain wide policies depends on the
workstation registry. The workstation will only receive a
system wide policy if the check box Default Computer/Network/System
policies update has been ticked and set to automatic. This then picks up
the system policy from the \\PDC\NETLOGON
share. If you are feeling masochistic, you can choose manual mode and
enter/guess the path to the PDC/BDC NETLOGON
share.
Furthermore one or more user and group
entries can be added and these too are applied to HKEY_CURRENT_USER for the user or the member of the
group(s).
The order of execution for the user policy is first the defined
user policy (if it exists) - if none has been defined then the Default User policy on the PDC
is used then any group policies are implemented.
Note that if you have multiple groups, the group allocated highest
priority will be applied first, then the others in descending order.
If you missed the key issue there, I'll point it out. If you have a defined user policy for an individual, it gets applied all by itself and Default User and Group Policies do not get applied.
The system policy for domains by default lives in the \\PDC\NETLOGON share
and is called NTconfig.pol.
The local path on the PDC to NETLOGON
is %SystemRoot%\system32\Repl\Import\Scripts
(Win95 expects a file called config.pol
and it must initially be stored into NETLOGON on the PDC)
In order to configure a policy for groups of users you use
the poledit utility to open the current system policy, usually \\PDC\NETLOGON\NTconfig.pol.
Add the group or individual by selecting the appropriate icon on the menu strip.
Double click on the group or user icon and then define whatever you wish for the policy.
Note here that in the Poledit registry editor, a grey box means not to change whatever value exists in the registry on the remote machine that the user is logging on to. If the value on the local workstation is different to that in the system policy it will only be changed if the corresponding value in the system policy is set, that is, not greyed out. White (blank) means clear the registry value, while a check means enforce a registry value.
If you have a network with Backup Domain Controllers, you
need to copy the file \\PDC\NETLOGON\NTconfig.pol
to the %SystemRoot%\System32\Repl\Export
subdirectory, for replication to the BDC's. Most people who implement this type
of network recommend that you directly copy the files to the %SystemRoot%\System32\Repl\Import\Scripts
subdirectory of each BDC to ensure the message gets through. Do
remember to turn on the directory replication service or your
export will sit there forever!
Microsoft's README
(Q142640) file says:
System Policy
System policy can be defined for both users and groups. The
order of precedence of system policies can be set for instances where a user is
a member of multiple groups. Three settings are available for each policy item
(enabled, disabled, or not specified). These policy settings are saved to the NETLOGON share of the PDC,
where they are replicated to the BDCs in the domain. When a user logs on, the NTConfig.pol file (depending on
the client) is parsed for policy settings to apply.
When a user logs on, the user policy (as defined in System Policy Editor) for the user is applied. If a user-specific policy is not applied, the default user policy is applied, followed by the group policies in priority order:
The lowest priority (as defined in System Policy
Editor) group policy for the user is applied.
(set this using Options|Group
Priority)
The next highest priority group policy is applied, and this step repeats until the policies for all of the user's groups have been applied.
If you have multiple groups defined in the System Policy then the first group in the order will be implemented. If you leave a box greyed out then the next group's selection will be implemented and so on. If they are all grey then it will be set to the workstation default value.
IMPORTANT (Listen carefully!!)
Policy being applied requires write
access?
NT 4.0 without Service Packs: On the workstation you MUST grant
read/write permission to all users for the %SystemRoot%\Profiles\Policy subdirectory. This was the
biggest gotcha in the implementation of System Policies in NT
4.0. This should be a function of the OS. The user should not have to access
such an important file. It was our feeling that this was a bug
in Windows NT 4.0. See the
KnowledgeBase article Q157673 that confirmed this! A fix was supplied
in NT4.0 SP2. You must still grant add/read to your %SystemRoot% so that the policy
can be downloaded. This is still a bug as far as we're concerned.
Can Microsoft ever get it right? Yes! SP3 fixes this!
It is essential that for workstations to
get a copy of the policy, the Default Computer\network\system policy
updates\remote updates box is checked, and set to Automatic, unless you are
feeling brave enough to define a path manually. I mean it should
be simple, but in a multiple domain controller environment...
Save the system policy file in the NETLOGON share (better
known as %SystemRoot%\System32\Repl\Import\Scripts
subdirectory) of the PDC. The file should be named NTconfig.pol.
Policy Troubleshooting Tips
Windows NT FAQ is a key resource to aid in understanding what you can do to restrict/limit using the Policy Editor and/or Registry Editor.
Is your SERVER name longer than 13 characters? We've had feedback that says that a long server name will cause Policy updates to fail! Install SP3 to solve this.
It might seem that changes to the policy will only be picked
up upon login by a user for the first time after the workstation is
restarted, however we have found that this is NOT the case! We kept
getting bitten because we would login as Administrator to see what happened -
which then promptly did behave correctly, so ensure that %SystemRoot%\Profiles\Policy on
the workstation(s) has the correct (write) permissions on the
directory and files within it. If you're running SP2,
then the permissions problem shifts to your %SystemRoot% directory. Install SP3
to solve this.
Check what remote policy the workstation is actually using. Login, then go back to your server and connect to the workstation with System Policy Editor. Check the stuff in Local Computer and make sure that it matches what should be there. To do this, use the file/connect option in the Poledit utility.
Check that your users have read access to
the NETLOGON share.
The security should be Everyone:
READ and Administrator:
FULL for both the share and normal security settings. You
wouldn't have forgotten that now, would you?
Having problems with groups? Make sure your users are being entered into a global group, not a local group!
Check that you actually made the user a member of the group that you're trying to apply to them!
Wrestling with Win95?
Create your Win95 policy on Win95 and copy it to the NT NETLOGON share as config.pol
Don't forget that you have to put grouppol.dll
into the windows\system
directory on your Win95 machine.
Profiles
Profiles are much simpler.
They exist as a group of directories that define the user environment.
The location for a domain users user profile can be set in the user manager for domains profile tab. The location must be specified as a UNC name.
If not set, they default to the profile in the %SystemRoot%\profiles\Default User
directory, not the %SystemRoot%\profiles\all
users directory that you might have thought.
Tip: if you put the profile for Default User in your NETLOGON share, any
workstations with an older copy will see this and update automatically.
The best way to set this profile is to have a dummy account especially for user profiles. Login, make any changes, then save the profile. The profile is then copied to the desired location by the system utility in the control panel.
This utility has a user profile tab. Select the user profile, then select copy. You then need to specify the location of the copy.
Browse for the location, then set the permissions to allow users access. Press OK and the profile is now active.
User Manager
Profiles are no longer limited to having .pds or .pdm extensions. Windows NT version 4.0 profiles have .man or .usr extensions, but they can have any extensions.
If you have a mixed work environment of computers running Windows NT version 3.51 and Windows NT version 4.0, you should use the .man or .usr extensions for compatibility. When Windows NT version 4.0 encounters a profile with a .usr or .man extension, it will create a matching directory with the .pds or .pdm extension.
Profile Troubleshooting Tips
Windows NT FAQ is a key resource to aid in understanding what you can do to restrict/limit using the Policy Editor and/or Registry Editor.
You did put the profile path into the User-Manager->User->Properties, didn't you?
The location must be specified as a UNC name. If you are using C:\blah\blah then this is wrong!
Your users aren't in the GUEST group, are they? If so, profiles won't get saved!
Roaming Profiles require that the location that you are storing the profiles under must be a share, otherwise you won't pick them up - and no, ADMIN$ will not work!
Roaming Profiles get copied back to the server on logout. Make sure you update the profile with the user logged out!
Changed from a WORKGROUP to Domains have you? Roaming Profiles will not get picked up if the workstation user still has a cached profile from when it was part of a WORKGROUP. You'll need to remove that, via Control Panel->System->User Profiles.
Moving from machine to machine and finding things are
different on each, even though your Roaming Profile is working? You need to
clear the local profile that is being picked up from %SystemRoot%\Profiles\All Users on
the workstation.
You can also hack the workstation(s) Registry so that All Users
resides on the server.
If you want the profiles to stay in one spot, you have to disable the local caching of the profiles. This will slow things down, but if your network is fairly fast, it shouldn't matter much. You can do this by using Regedt32 on each machine to edit:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\
CurrentVersion\Winlogon\DeleteRoamingCache
REG_DWORD
Default: 0
If the value of this entry is 1, locally cached profiles are deleted when users with domain profiles log off. Thus the only copy of the profile is on the server.
Mandatory Profiles?
Say you have a domain controller with a policy file on it that does not allow cached profiles.
Using one default mandatory profile for all users Add the .MAN extension to the ntuser file.
If you use the .man extension on the folder
in which the profile is stored, such as default.man then in the event of the workstation being
off the net or unable to contact the server, this will cause the system to
display a message telling the user that since it can not contact the domain
controller, he/she can't be logged in. This is the NT 3.5x behaviour and can be
useful! If you want the normal NT4 profile to behave in the same way, just give
the profile a .man and make sure that you disable local profile caching on the
target workstations. I haven't tested if an NT4 folder with .PDM works the same
way.
You can't share the folder with the .man extension. So, put it in
the NETLOGON share
and then point the users profile to \\PDC\NETLOGON\default.man.
W95 and Profile
locations.
Yes, profiles work with Win95 clients too. The Win95 clients store
their profile info in the users home directory, while the NT
clients will store them in the Profiles
directory.
i.e. a user with both Win95 and NT access will have two different
profiles.
Windows NT Protocols
Transport Control
Protocol/Internet Protocol (TCP/IP)
Transport Control Protocol/Internet Protocol (TCP/IP) provides communication across interconnected networks made up of computers with diverse hardware architectures. TCP/IP is the transport protocol used on the Internet. Microsoft® Windows NT® TCP/IP supports Dynamic Host Configuration Protocol (DHCP), which provides centralized management of address allocation and protocol configuration.
During troubleshooting, make sure the DHCP servers are running the DHCP Server service (automatically configured to start on a DHCP server), and that the DHCP clients are running the DHCP Client service (automatically starts on a DHCP client). If there are multiple DHCP servers to provide redundancy, make sure the DHCP servers do not overlap in their address pools. If this occurs, it is possible that two DHCP clients are assigned the same IP address. To verify that only authorized DHCP servers exist on the network, use the DHCP Server Locator utility. If a DHCP server database becomes corrupt, restore it from the automatic backup files.
NWLink (IPX/SPX)
Client Service for NetWare (CSNW) allows computers running Microsoft Windows NT Workstation to access file and print resources on Novell NetWare servers. If the site has multiple frame types, such as Ether 802.2 and 802.3, make sure you choose the correct frame type. NetWare 3.12 and later defaults to 802.2, while NetWare 3.11 and earlier defaults to 802.3.
NWLink is an Internetwork Packet Exchange/Sequence Packet Exchange (IPX/SPX) compatible transport protocol. IPX/SPX is the primary protocol for Novell® networks. Used in conjunction with GSNW (Gateway Service for NetWare), Computers running Windows NT Server can access file and print resources on Novell NetWare servers.
NWLink via NetBIOS over IPX (NBIPX)also supports communication between Windows NT and Microsoft MS-DOS®, OS/2®, Microsoft Windows®, or other computers running Windows NT . It is often used in mixed NetWare and Microsoft environments.
When troubleshooting in an environment with NetWare servers,
make sure that NWLink is configured with the same frame type as the frame type
of the NetWare server. Also run the ipxroute
configuration utility to see the network number, binding info and frame type.
As always, check that the appropriate services are running on the servers and
clients, such as Client Service for
NetWare or Gateway Service for NetWare.
NetBIOS Frame (NBF) protocol provides compatibility with earlier LANs, such as LAN Manager and LAN Server, using an implementation of the IBM NetBEUI protocol stack standards. NBF is designed to be a local area network transport that does not need to interoperate with a variety of other hosts.
NBF is the Windows NT version of NetBEUI. At the OSI Transport and Session layers NBF uses the IBM NBFP (NetBIOS Extended Frame Protocol) for session and connection establishment and termination.
In the registry, NBF is labeled Nbf.
AppleTalk
AppleTalk is used with Services for Macintosh on a computer running Windows NT Server to host connections from Apple Macintosh clients.
Tom's
A+ Hardware HELP Section
PC Ports
Parallel ports: - 25 Pin female, "D" connector
- Sends and receives 8 bits of data at a time
Serial ports: - 25 Pin male, "D" connector or
9 Pin male, "D" connector
- Sends and receives 1 bit of data at a time
- External ports send data in an asynchronous fashion.
Keyboard: - 5 Pin DIN or PS/2
Mouse: - 9 Pin serial or PS/2
Video: - HDA= 15 pin female, 3 rows of pins. (current VGA and
SVGA only)
Cables and Connectors
Tape, removable, hard, and
optical drives along with scanners can all use SCSI connections.
- Up to seven devices can be
chained off of a SCSI port.
- 18 feet is the maximum length
that a SCSI cable can support.
- Most external SCSI devices
have two 50 pin female ports.
- Most PC's are set to SCSI ID
7.
Null modem cables (serial
cables) are used to transmit data between 2 DTE devices.
- Because of interference, you
have to reduce transfer rates the longer a cable is.
- 15 feet is the maximum length
that a serial cable should be.
Phone lines (few network)
cables use RJ11 or RJ12 connectors. Connector resembles a small phone jack.
- Twisted pair cables use RJ45
connectors. Connector resembles a fat phone jack.
Com Ports
COM1 and COM3 use IRQ4.
COM2 and COM4 use IRQ3.
The majority of PC's have only
2 COM port connectors.
BIOS
(Basic Input Output System)
- Chip that contains low level
software for configuring the system's capabilities with hardware.
System
Assembly Basics
Phillips and Flat-Head
screwdrivers are the most common tools needed for disassembly.
Paper should be at hand for
diagramming connections.
Egg cartons are helpful in
keeping screws organized.
Expansion boards should be
removed by gently rocking back and forth at each end.
Red and blue stripes on ribbon
cables indicate pin 1.
Field
replaceable units (or FRU's)
are any computer parts that can be replaced without special equipment such as
soldering irons.
|
Busses ISA 8-bit EISA 16-bit PCMCIA 32-bit PCI 64-bit |
I/O Ports COM1 3F8H COM2 2F8H COM3 3E8H COM4 2E8H LPT1 378H LPT2 278H |
Monitors
Dot pitch is the space between
pixels in millimeters.
The refresh rate is the number
times display is redrawn every second.
Processors
The math coprocessor deals with
floating-point numeric operations.
The 80386SX uses the 80387SX as
its fastest coprocessor, and has a 32-bit word size and 16-bit data path.
The 80386DX uses the 80387DX as
its fastest coprocessor, and has a 32-bit word size and data path.
The 80486SX has a disabled
coprocessor, and 32-bit word size and data path.
A 486DX2's external clock speed
is half of the internal clock speed.
A 486DX4's external clock speed
is 1/3 of the internal clock speed.
MMX:
1) 57 instructions for
manipulating video, audio and graphic data
2) SIMD: Single Instruction
Multiple Data
3) More build-in cache on chip
Pentium II System Bus allows
multiple simultaneous transactions.
SEC - (Pentium II) Single Edge
Cartridge design.
Core and L2 Cache in cartridge,
designed for single and dual processor computers.
Cache:
- L1 - Internal Cache
- L2 - External Cache
CPU
Connectivity:
- Socket 7 - Pentium CPUs
- Socket 8 - Pentium Pro
387-pin ZIF contact connector
- Slot 1 - Pentium II 242 SEC
contact connector
CMOS:
- Contains the computer BIOS.
- Maintains its data with the
use of a battery for periods when the machine is powered down.
Memory
ROM (Read-Only Memory):
- ROM is a form of non-volatile
memory.
- Contains both POST and SETUP.
NVRAM (Non-Volatile Memory):
- Can maintain data without the
use of power.
RAM
(Random Access Memory):
- RAM is volatile memory and
does not retain data without power.
- RAM contains any active
application, including the operating system.
- HMA (or high memory area) is
the first 64K of extended memory.
- Conventional memory is the
first 640K of memory.
- Upper memory is the memory
between 640K and 1024K. Used to load DOS drivers to allow applications more
conventional memory.
- Extended memory is the memory
above 1024K.
- Expanded memory is addressed
in pages of 16K.
Drives
When transferring data, copying
data from one drive to another is the best method of data protection. A cluster is a group of sectors. Sectors are aligned in tracks.
- The seek time is the time
that is takes the head to reach the needed track.
- The latency period is the
time that it takes the sector to move under the head.
- The overall time it takes a
hard drive to find data is the access time.
- The data transfer rate is how
fast the hard drive sends data to the PC.
- The BIOS in older systems may
not support large hard drives, and must be upgraded before installation. The
physical or low-level format is rarely needed.
To prepare a hard disk for use,
setup a partition on the disk, format the partition, then load the OS.
FDISK and PART (found on older
versions of DOS) are the programs used for setting up partitions.
- Always back up hard drives
before formatting.
FORMAT.EXE - Program used for
DOS formatting.
FORMAT /S is the fastest way to
make a bootable disk. The /S switch tells FORMAT to copy system boot files to
the disk.
Physical drives are actual
separate drives while logical drives concern partitions on the physical drives.
To write protect a 3.5 floppy,
uncover the hole in the upper-right hand corner of the diskette.
To write protect a 5.25 floppy,
cover the notch on the side of the diskette.
FDD controllers use DMA channel
2 in most cases.
HDI = Head to Disk Interference
Controllers
Controllers match speeds
between sending and receiving devices, convert data between formats, and
isolate the software from the hardware.
A DTE device in general, is a
device such as a computer or printer.
A DCE device is a device such
as a modem.
RS232 is the standard for
serial connections.
DMAs (Direct Memory Access)
work with the CPU, letting devices put data into memory rather than the CPU,
therefore helping to speed transfer rates.
Modem Commands
Command Function
ATA Answer
ATD Dial
ATDL Redial
ATF1 Half-Duplex Off (echo copy of receiving information)
ATHN Hang up
ATMN Speaker On/Off
ATSR Display register
ATH Hangs up modem
PCMCIA
Type 1 3.3mm Memory
Type 2 5mm Modems,
Network cards
Type 3 10.5mm Hard Disks
Power
Supplies
Yellow: + 12
Blue: -
12
Red: +
5
White: -
5
Voltage for motor: +/- 12 volts
Voltage for circuitry: +/- 5 volts
TROUBLE-SHOOTING and REPAIRING
 Hardware problems
usually surface at the time you are booting your PC, but sometimes occur when
you are trying to access some device on your PC.
Hardware problems
usually surface at the time you are booting your PC, but sometimes occur when
you are trying to access some device on your PC.
I will address some of the most common problems
first, then go into a few more less common problems.
RULE OF THUMB: Always turn-off the power to your
PC before connecting or disconnecting any device or cable! Also, we recommend
that you use a "static" wristband before touching any expansion card
or chips in your PC to reduce problems with "static electricity".
NOTE: Some PCs will burn a chip on the motherboard if you plug in a device or
remove a device while the power is on!
Error Messages:
Message:"Keyboard Error" - this error usually appears when booting and often is unnoticed by the user because "who really watches the boot process?". It is usually noticed when the keys you press don't reflect on the screen.
CAUSE: Keyboard is not plugged into its port, or the
keyboard has died or shorted somewhere.
SOLUTION: Turn-off the power, plug the keyboard into its port, and reboot.
If it is plugged in, try another keyboard in its place.
Message:"Mouse Not Found" - usually appears when you are booting.
CAUSE: Mouse may not be plugged into its port. Might be
because the mouse has been dropped and destroyed inside the mouse case.
SOLUTION: Check if your mouse is plugged in. If it is
plugged in, try another mouse. If a new mouse doesn't work, you may have to
re-install your mouse software.
In some machines with "Micronics"
motherboards which have two 9-pin COM ports, you will find that some
Microsoft/PS-2 (the ones with a dull gray finish and a small plug) mice will
not work in the port labeled "Mouse", and you have to plug it into
the other 9-Pin connector. Make sure the power is off when you do this.
Message: "Invalid System Disk" This may occur when you are trying to load an operating system, or when you try to boot your PC.
CAUSES:
No operating system currently installed on the
"C:" drive.
No bootable partition on the "C:" drive.
No "bootable" partition on "C:" drive set to "active" status.
SOLUTIONS:
Use the DOS SETUP DISKETTE #1 to boot your machine. At the first MS-DOS screen
where you can exit (you will see "Exit=F3" along the bottom), exit by
pressing F3 twice. You should see the "A:\> prompt appear. Run the
"FDISK" program from the "A:" drive. Then select option 4
to see the status of your partitions. If the C: drive is not
"active", set it to "active" using the "FDISK"
option 2. Then try to reboot.
If your system still doesn't reboot, you will
probably need to load your operating system - DOS or whatever.
Message:”No Operating
System" or "Operating System not found".
CAUSES:
No operating system currently installed on the
"C:" drive.
No bootable partition on the "C:" drive.
No "bootable" partition on "C:" drive set to "active" status.
Hard Drive (hard drive 0) may not be properly defined in the Setup (CMOS). Remember this: You should always have a listing of your setup taped inside your PC's cover. Many times, your hard drive will have the specifications for that hard drive listed on the label on the hard drive. Many systems will want you to set your CMOS to "Auto" for auto-detect, and some even want "not installed" (but this not common).
SOLUTIONS:
Use the DOS SETUP DISKETTE #1 to boot your machine. At the first MS-DOS screen
where you can exit (you will see "Exit=F3" along the bottom), exit by
pressing F3 twice. You should see the "A:\> prompt appear. Run the
"FDISK" program from the "A:" drive. Then select option 4
to see the status of your partitions. If the C: drive is not
"active", set it to "active" using the "FDISK"
option 2. Then try to reboot.
Check your setup (cmos) to see if your hard disk
is properly defined in your CMOS. If not, set it properly, and try to reboot.
If your system still doesn't reboot, you will
probably need to load your operating system - DOS or whatever.
Message: "Not Ready Reading Drive A:" or some other drive.
CAUSES:
No floppy in drive A. or no CDROM is CDROM drive.
Floppy drive cable installed incorrectly. Pin 1 on wrong side.
Cable installed backwards.
Invalid Drive Size
A: drive has died or shorted out.
SOLUTIONS:
Place a floppy diskette in Drive A and press ENTER key.
Check the cable on the A: drive. Make sure the red edge goes to pin 1 on the drive (usually toward the power cable), and that the cable connector is on all 34 pins. Some floppy drives have an arrow and a 1 to show which side is pin 1. Then try again to read the drive.
NOTES: An IDE floppy cable has 34-pin connectors. The
red edge of the cable at the motherboard normally is toward the rear of the PC
or motherboard. The end of the cable with the two connectors close together
goes toward the drives, the long end connects to the motherboard.
Make sure the end of the cable with the two connectors close together is plugged into the A: drive. The end connector goes to the A: drive.
SYMPTOM: Indicator Light on a Drive remains on and will not read.
CAUSES: Usually caused by incorrect cable installation.
Check the cable on the A: drive. Make sure the red edge goes to pin 1 on the drive (usually toward the power cable), and that the cable connector is on all 34 pins. Some floppy drives have an arrow and a 1 to show which side is pin 1. Then try again to read the drive.
NOTES: An IDE floppy cable has 34-pin connectors. The
red edge of the cable at the motherboard normally is toward the rear of the PC
or motherboard. The end of the cable with the two connectors close together
goes toward the drives, the long end connects to the motherboard.
SOLUTION: Install cable correctly by making sure the end of the cable with the two connectors close together is plugged into the A: drive. The end connector goes to the A: drive.
SYMPTOM: CDROM will not read.
CAUSES: Could be many problems.
Cables not properly attached.
Device not properly configured.
Driver software not loaded at boot time.
SOLUTIONS:
Make sure the cables have the end with two connectors at the drive, and the long end to the motherboard. Make sure the red edges of the cable are on the Pin-1 side of the drive and motherboard connectors. If you have to change the cable, turn off the power before unplugging the cables.
Check your "config.sys" file. It should have a statement like this: "DEVICE=C:\CDROM\SGIDECD.SYS /D:MSCD000". On your PC the directory and the "SGIDECD.SYS" may be different, but the statement should be there.
Check your "autoexec.bat" file. It should have a statement somewhat like this: "C:\DOS\MSCDEX.EXE /D:MSCD000". Again the directory may be different.
Trouble Shooting Memory Problems
"Trouble-Shooting" memory is often
related to knowing a few simple facts, and they are usually only learned at the
time you try to install additional memory in a PC. First, lets state some of
these facts.
30-pin SIMMs do not fit in 72-pin slots. And neither fit in a 168-pin DIMM slot.
Many people see a bargain in memory and purchase it without knowing if it will work in their PCs. Often, it must be returned to the store.
FPM memory was designed for PCs of the 386 and 486 motherboard styles.
EDO memory does not work on a 486 style motherboard.
SDRAM memory does not work on a 486 style motherboard.
Memory for 486 machines should be FPM SIMMs.
Memory for Pentium PCs will most often be EDO RAM, but in a few cases it may be SDRAM which is on 168-pin DIMM chips.
Parity memory and non-parity memory is not the same!
Non-parity memory will not run if you have parity enabled on your motherboard.
Some parity memory will run as non-parity on motherboards which are configured for non-parity memory.
To actually test memory, you may want to purchase
a SIMM tester, or a DIMM tester if available.
Ok, with that in mind, lets look a little further
into troubleshooting memory. The following types of problems may occur with
memory:
Troubleshooting
General
When replacing a power supply
pay special attention to the physical characteristics, the voltage and
connectors are standardized.
Rom addresses, I/O addresses,
Iris, and DMA channels can all cause conflicts.
IRQ conflicts are the most
common conflict, because there are so few IRQs compared to the many peripherals
that can be installed into a system.
If a battery test fine after a
boot configuration error, the most likely cause is the system board.
Always carefully examine any
shipped in merchandise before installation and powering the system on.
Preventative
Maintenance and Safety
- Almost all computer equipment
should be cleaned with only a soft, damp cloth with a mild detergent.
ESD (Electro-Static Discharge) awareness - Prevention of
having electric currents damage system components. Wear a wrist strap.
- ESD will degrade components
integrity. Although not immediately seen, the effects show up months later.
- Any amount of friction is
enough to cause enough static to cause ESD.
- To avoid ESD use a wrist
strap, and always ship items in ESD safe bags.
- Nylon, plastic, wood, and
vinyl are not ESD safe materials.
- Compressed air it most
effective for removing dust because of the pressure, directability, and less
chance of ESD damage.
- Line analyzers are used for
detecting line surges, sags, and spikes.
- Hard drives should be
defragmented and backed up often.
- Hard drives should be
protected from both magnetic fields and temperature extremes.
- Never lubricate the printhead
pins of a dot matrix printer during preventative maintenance.
- Never wear a wrist strap
while working on a monitor CRT because the stored voltage is capable of killing
a person.
Trouble Shooting Video (Monitor) Problems
"Trouble-Shooting" of video display
devices includes both the monitor itself, and the video card in an expansion
slot; however, most of the problems we see today occurs because of the setup
problems with different Microsoft Windows software such as Windows 95, Windows
NT Server, and Windows NT Workstation.
The problem that we see most often is that the
software (Novell, Windows NT) do not come with the drivers for some of the
newer video graphics cards produced after the network software was shipped. So,
in many instances we have to use the software from the vendor to provide the
necessary drivers and then set up the graphics with Windows based software.
If your problems cannot be traced to an
"adjustment" of brightness, contrast, image location on the screen,
or problems such as not loading a driver, or not properly setup, then we
recommend you call a vendor or professional repairman.
DO NOT ATTEMPT TO REPAIR THE ELECTRONICS OF A
MONITOR UNLESS YOU HAVE HAD EXTENSIVE TRAINING! A COLOR DISPLAY MONITOR HOLDS WELL
OVER 30,000 VOLTS - ENOUGH TO ELECTROCUTE YOU. THIS IS THE TIME TO CALL THE
MANUFACTURER OR CONTRACTED MAINTENANCE COMPANY!
SYMPTOM: The monitor is blank, but the system is turned on (the power indicator light is green).
CAUSES/SOLUTIONS: With most users,
this is often caused by: monitor power is off, the brightness or contrast
buttons have been turned down to the point nothing shows, or the cable has
fallen off. These are the first things to check.
SYMPTOM: The monitor is blank, but the system is turned on (the power indicator light is Orange or not green).
Usually, if the power light does not turn green
after the POST tests you have a serious problem with the video card, or you
have a problem with your video card, or your BIOS has been damaged.
SYMPTOM: The monitor is blank, but the system is turned on (the power indicator light is not green) and you do not hear your "C:" drive operate, or your printer kick in.
CAUSES/SOLUTIONS: Most likely, if you
do not start the POST tests, your BIOS has been damaged, or some chip on the
motherboard has shorted.
NOTE: Occasionally, users like to "play" and
they go into the monitor setup and change the frequency, the font, the number
of colors, and even the screen size.
When installing Windows NT, for instance, with
Diamond Stealth 64DRAM video cards we often have problems with the
"Refresh Rate" being changed from 60 hertz to something else.
SYMPTOM: The picture you see on the screen is actually two screens (both the same) showing in miniature versions on the screen.
CAUSES/SOLUTIONS: Incorrect
"Refresh Rate" is the normal problem. We usually just reinstall the
drivers and reboot. Sometimes we need to get into the above windows screen and
set the refresh rate. The refresh rate for MOST monitors will be 60 hertz. You
can always refer to your Users Manual for your particular monitor.
REMEMBER: Any time you change the settings using the
screen above, you have to click on the "Apply" button, then the
"OK" button to get the changes to take place.
SYMPTOM: When installing Windows 95, with some video cards, the picture you see is about 1/2 size, in the middle of the screen; and, it is often poorly focused.
CAUSE/SOLUTION: On our Micronics P75s with SVGA screens this is caused by Windows 95 defaulting to 16 colors and 640x480 pixels. We get into the Windows 95 Display setup from the "Control Panel" and change the settings. First, we change it to 256 colors, then 800x600 pixels in the "Desktop Area" (just put the mouse on the down arrow and drag it horizontally until 800x600 shows), then we make sure the "Font Size" box has "small fonts" in it, and finally we set the "Refresh Frequency" box is set to "60 Hz". Then, we reboot and it works.
Another Solution: Occasionally, with
early shipments of Windows 95, the drivers for a new video card is missing. Use
the diskette provided by the vendor to install the drivers in this case. We
create a directory on the hard drive, drag the files from the A: drive to the
C: drive directory, and run the setup program provided by the monitor's
manufacturer. Then rebooting Windows 95 usually corrects the problem.
If
the above adjustments and loading of drivers do not solve the problems, we
usually call contracted maintenance.
Troubleshooting
Printers
Laser Printers:
The ozone filter needs to be
replaced on laser printers when performing preventative maintenance. For dark spots on a page with a laser
printer, it indicates loose toner particles. Running extra paper through will
usually resolve it.
The order of processes in a
laser printer is:
1) Cleaning 2) Charging
3) Writing 4) Developing 5) Transferring 6) Fusing
The primary corona has the
highest negative charge in a printer.
Always check where the leading
edge of paper is when troubleshooting paper jams, because it can indicate which
printer part is causing the jam. The photoconductive drum in a laser printer is
charged negatively, and loses its charge when light hits it. The transfer
corona can cause the print to be too light.
Dot Matrix:
A tight ribbon can cause flecks and smudges on the
paper. Missing or broken print head pins causes incomplete characters. Never
lubricate the print head on a printer. If the print density is erratic, then
there is probably an error with the ribbon advance.
Common DOS 6.0+ commands
- For more information on commands, type the
command with a "/?" following it.
- Reserved symbols: ? / * & ; \ : % @ . (
) < ># ! = |
- Remember DOS works like this: "command_from_to"
("_" is a space)
Example:
copy
tom.doc
c:\winnt\system32\drivers\etc
ren -
renames a file to something else
*.* -
wild card...means include all files
..?.. -
wild card for one letter
attrib + or -
shows and sets the attributes of a file (read, write, system, etc)
cd\ - change (go) to the
root directory (C:\)
cd.. - change (go) up one
level of directory
copy -
copy files from-to
xcopy -
same as copy but has more options, such as sub-directory copying.
date or time -
sets the date or time on the computer
del -
delete a file
deltree -
delete the directory and everything inside it
dir -
shows files and directories where you are at
edit -
edit a file command
fdisk /mbr - fix master boot
record
format a: or c: -
format a floppy or hard drive (dangerous!)
help "..." -
help command "..."- name of file same as "/?"
mem - shows the amount of
memory on a computer
move -
move a file command
md -
make a directory
rd -
remove a directory (only if empty) else use deltree
ren -
rename a file
tree - shows directory in
a tree format
"\" - back slash
"/" - forward slash
ipconfig -
checking a computers configuration (winipcfg for Win95)
arp -
shows physical address translation
nbtstat -
NETbios over TCP/IP protocol statistics
Viewing Directory examples:
dir /o = view directory in alphabetical order
dir /p = view directory by one page at a time
dir /w = view directory in wide format
To stop the screen from flying by, use the "|more"
command after your command.
(The "|" is actually two lines
straight up and down, usually with the "\" key)
Example: "dir |more"
TCP Command Line Utilities
arp- Arp.exe is used to resolve
an IP address to its hardware (MAC address).
Local Arp cache is checked first before initiating an ARP request
broadcast
Switches
-a - View the contents of the local ARP cache table
-s - Add a static Arp entry for frequent accessed hosts
-d - Delete a entry
ipconfig - The ipconfig is a command
line tool for NT that shows how the computer's IP stack is
configured.C:\ipconfig
Windows NT IP
Configuration:
Ethernet adapter E100B1:
IP Address: 198.133.234.23
Subnet Mask: 255.255.255.0
Default Gateway: 198.133.234.2
Switches
/all - Extra information is revealed; IP host name, DNS, WINS server
/release - If DHCP is enabled, you release the lease with this switch.
/renew - The renew switch will update and renew DHCP lease information from the
DHCP Server.
Winipcfg
- The winipcfg is a GUI
version for Windows 95/98 of ipconfig
Ping- verifies configurations
and tests connectivity If you can ping a hostname but cannot connect to a share
point in Explorer, then the LMHOST file does not have an entry for that
hostname or WINS is not working.
Conversely,
if you CAN connect to a share in Explorer yet cannot ping the hostname, then
either the HOST file entry is wrong or DNS is not working.
netstat The netstat tool displays
protocol statistics and the state of current TCP/IP connections
C:\WINDOWS>netstat /?
- Displays protocol statistics and current TCP/IP network connections.
NETSTAT [-a] [-e] [-n]
[-s] [-p proto] [-r] [interval]
-a Displays all connections and
listening ports.
-e
Displays Ethernet statistics. This may be combined with the -s option.
-n
Displays addresses and port numbers in numerical form.
*-p proto Shows connections for the protocol specified
by proto; proto may be TCP or UDP. If
used with the -s option to display per-protocol statistics, proto may be TCP,
UDP, or IP.
-r
Displays the routing table.
-s Displays per-protocol
statistics. By default, statistics are
shown for TCP, UDP and IP; the -p option may be used to specify a subset of the
default.
*interval Redisplays selected statistics, pausing
interval seconds between each display.
Press CTRL+C to stop redisplaying statistics. If omitted, netstat will print the current configuration
information once.
nbtstat The nbtstat checks the
state of NetBIOS over TCP/IP connections and returns NetBIOS session and name
resolution statistics. This tool can also be used to update the local NetBIOS
name cache.
Displays protocol
statistics and current TCP/IP connections using NBT(NetBIOS over TCP/IP).
NBTSTAT [-a RemoteName]
[-A IP address] [-c] [-n]
[-r] [-R] [-s] [S] [interval] ]
-a
(adapter status) Lists the
remote machine's name table given its name
-A
(Adapter status) Lists the
remote machine's name table given its IP address.
-c
(cache) Lists the remote name cache
including the IP addresses
-n
(names) Lists local NetBIOS names.
-r
(resolved) Lists names resolved by broadcast
and via WINS
-R
(Reload) Purges and reloads the remote cache
name table
-S
(Sessions) Lists sessions table with the
destination IP addresses
-s
(sessions) Lists sessions table converting
destination IP to host names via the hosts file.
*RemoteName Remote host machine name.
IP
address Dotted decimal representation of the IP address.
interval Redisplays selected
statistics, pausing interval seconds between each display.
Press Ctrl+C to stop redisplaying statistics.
Note: Netstat works
for TCP/IP connections, and Nbtstat works for NetBIOS connections.
Tracert - the
tracert tool shows the route a packet will take over a network from one
computer to another.
DVD Technology
DVD is an audio/video/data storage standard based on high-density
optical discs. DVD includes four major formats:
-
DVD-Video for video data
-
DVD-ROM (Read Only Memory) for computer data
-
DVD-R (recordable) for write-once computer data
-
DVD-RAM for erasable computer data
DVD Discs
DVD disks are offered in many
different capacities ranging from a single-sided, single-layer disk with 4.7 GB
of data to a double-sided, double-layer disk with 17 GB of data stored on the
disk.
DVD discs can hold nearly 26 times the amount of data that can be stored on a
conventional CD-ROM disc. This capacity virtually eliminates the need to swap
discs in the middle of a game or application, and at the same time reduces the
cost and the number of discs necessary to hold the data. The chart below
illustrates the difference between CD and DVD storage possibilities.
Disc Type |
Diameter |
Sides & |
Capacity |
Playback Time |
|
CD-ROM |
120 mm |
SS |
650 Megabytes |
Max 74 min audio |
|
DVD-5 |
120 mm |
SS/SL |
4.7 Gigabytes |
Over 2 hours of video |
|
DVD-9 |
120 mm |
SS/DL |
8.5 Gigabytes |
Approx. 4 hours |
|
DVD-10 |
120 mm |
DS/SL |
9.4 Gigabytes |
Approx.4.5 hours |
|
DVD-18 |
120 mm |
DS/DL |
17 Gigabytes |
Over 8 hours |
|
Table Notes: |
||||
|
|
To squeeze all
this information onto the CD-sized disc, the designers of the DVD disc made
several changes from the compact disc. First they made pits and lands used to
record data and the track spacing nearly half the size of the original CD
design. Then, they made the discs double sided and added another data layer
to each side creating a potential for four layers of data per disc. See
Figure 1. |
|
|
Compared to CD, DVD uses smaller pits and a more closely spaced track. The result is a significant increase in data density. See Figure 2. Like CD, DVD is 120 mm in diameter. Like CD, DVD is 1.2 mm
thick composed of two 0.6 mm substrates bonded together. The new DVD-ROM
drives are able to play existing audio CDs, however this is not part of the
DVD specification. |
The DVD standard defines a disc that maintains the overall dimensions,
look and feel of the current CD. Some of these similarities provide
similarities for customers who have not used DVD disks.
|
|
CD |
DVD |
|
Disc
Diameter |
120 mm |
120 mm |
|
Disc
Thickness |
1.2 mm |
1.2 mm |
|
Disc
Structure |
Single substrate |
Two bonded 0.6 mm
substrates |
|
Data
Layers |
1 |
1 or 2 |
|
Data
Capacity |
Approx. 680 MB |
Single Layer: 4.7 GB x 2 |
|
Data
Transfer Rate |
Mode 1: 153.6 KB/second |
1,108 KB/second, nominal |
DVD-ROM and DVD-Video Discs
DVD disks use the UDF format. The difference between a DVD-ROM title and
DVD-Video title is only the data that is stored on the disc. This is one reason
why the UDF format was adopted. Discs can be used for different purposes
without requiring a change in format.
An Apple DVD-ROM drive can read a DVD-Video disc. However, the computer must be
able to decode the video in order for it to be played. The decoders commonly
used to compress DVD-Video data are:
- MPEG-1 or MPEG-2 for video data
- AC-3 for audio data
Decoding can be performed through hardware or software solutions.
Hardware decoding usually includes either a PCI Card that has the MPEG-2 and AC-3 decoders on the card or for the PowerBook G3 Series DVD, a PC Card with the same equivalent hardware. MPEG-1 can be decoded by QuickTime does not require hardware decoding.
Software
decoding does not require any additional hardware because it uses a
software-based MPEG-2 and AC-3 decoder.
DVD vs CD-Rom
In the world of CD-ROM drives, Toshiba has long
stood for quality and speed. In many higher priced computers, the CD-ROM drive
is invariably made by Toshiba. We now
will take a look and compare head to head Toshiba’s latest entries into the
CD-ROM/DVD-ROM drive market.
The latest generation of Toshiba drives encompass
two models, one is a CD-ROM only drive, and the other is a DVD-ROM drive.
The XM-6502B is a 40X CD-ROM drive that features
UDMA-2 bus transfers. This really is a rocket and is about the fastest drive
out there without the Kenwood Zen technology (multiple lasers reading different
sectors). What it gains in speed
though, it loses in a couple of areas.
The SD-M1212 is Toshiba’s latest DVD-ROM drive. It
has a 6X DVD and 32X CD-ROM speed; it is one of the latest in the current crop
of DVD-ROM drives. This drive also features UDMA-2 bus transfers. It is no
slouch, but it does not have the speed of the 40X drive (obviously). What this
drive gives up in speed, it does make up for in features.
|
The Results: |
SD-M1212 (DVD-ROM) |
XM-6502B (CD-ROM) |
|
WinMark 99© |
1550 |
1040 |
|
CD Transfer Rate |
|
|
|
Inside |
2230 KB/Sec |
2630 KB/Sec |
|
Outside |
4580 KB/Sec |
1910 KB/Sec |
|
CD Access |
87.6 ms |
101 ms |
|
CPU Utilization |
3.63 % |
3.46 % |
Interpretation
While the
DVD-ROM drive was never able to go above 4.6 MB/sec in transfers, the 40X
CD-ROM was able to go up to 6 MB/sec in transfers. Why such a low number in the
outside CD Transfer Rate? Well, the program averages those numbers out, and
while the 40X CD-ROM drive peaked at 6 MB/sec, it also dropped very low when it
started to hit the middle and outside tracks of the CD-ROM.