Objectives| Introduction| The Berkeley r Commands| Network File System| NFS Daemons| Exporting NFS File systems| Importing NFS File Systems| Other Useful Commands| Adding a Host| Conclusions| Review Questions
This section and the last section combine to provide an introduction to the topic of networking under the UNIX operating system. The entire area is much more complex and deserves a subject in its own right.
Command Purpose rsh remote shell, used to execute commands on a remote machine without logging in rlogin remote login, logs into a remote machine, if set up properly no password will be asked for rcp remote copy, copy a file from a remote machine to the local machine Table 13.1. Some of the Berkeley r Commands.
For example:
perform an ls on the remote machine aldur bash$ rsh aldur ls Password: Mail core masters.tar.z rcos.uu telnet.doc Masters dead.letter mbox researchHowever if the two level equivalence system that these commands use is satisfied then no password will be requested. The two levels of equivalence used are
Host and account equivalence are one way. In the above jasper is an equivalent host to aldur but not the other way around.
hosts.equiv file is a text file containing lines of the following format
host_name [user_name]For example:
A machine pol might have the following /etc/hosts.equiv file aldur jasper david It specifies that all users on the machine aldur, and the user david from jasper are allowed to use the r commands to connect to pol without specifying passwords.
hostname [username_list]If a username and host is listed in the .rhosts file it means that the specified account is equivalent to this one and may use the r commands without a password.
If host and account level equivalence are allowed the following guidelines should be followed
Exercise 13-1. Set a local machine up so that you have host and account equivalence between accounts on two machines.
Exercise 13-2. Having set up equivalence use the rsh command to perform the following tasks.
d) is a method that is sometimes used to implement backups across a network.
The Network File System (NFS) was developed by Sun Microsystems, a manufacturer of UNIX machines. The specification for NFS was placed in the public domain and is now implemented on every version of UNIX currently available and implementations also exist on other platforms including MS-DOS and OS/2.
NFS runs on top of TCP/IP and is basically a new file system much like the ext2 and msdos file systems discussed in Section 7. It provides the ability to connect directories from remote machines into the local machine's normal file system. This means that users may manipulate the remote files and directories using the same commands they use on local files and directories.
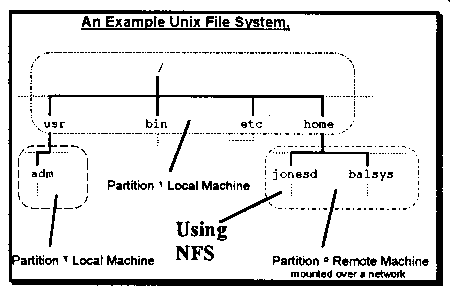
In Diagram 13.1 NFS provides the jonesd and balsys directories that are located on another machine somewhere on the network. NFS allows the user to perform commands like ls /home/jonesd to obtain a directory listing of the jonesd directory.

Diagram 13.1. UNIX File system Using NFS.
Before using NFS the
The daemons and their purpose are summarised in Table 13.2 for servers and in Table 13.3 for clients.
The NFS daemons are started in the system startup scripts. The exact format of the startup scripts (as discussed in Section 9) will differ from system to system. Included below is an example from a server machine's startup scripts.
Daemon Purpose nfsd handles NFS requests and executes them on the server, a server will typically run multiple nfsd daemons mountd handles the mount requests portmap performs the translation from RPCs to ports biod the block I/O daemon, typically multiple copies are running rpc.statd the network status daemon, notifies lockd if network goes down rpc.lockd handles file locking and lock recovery Table 13.2. NFS Server Daemons. Daemon Purpose portmap performs the translation from remote procedure calls to ports biod the block I/O daemon, typically multiple copies are running rpc.statd the network status daemon, notifies lockd if network goes down rpc.lockd handles file locking and lock recovery Table 13.3. NFS Client Daemons.For example:
if [ -f /etc/exports ] # does /etc/exports exist? then exportfs -a nfsd 8 echo -n ' nfsd' rpc.mountd -n fi
The /etc/exports file is a text file containing lines of the following format
directory export_optionsdirectory is the full path name of the directory that is to be exported. The choice of directory must follow these rules
NFS Option Purpose rw=host:host specify which hosts can read/write to the exported directory ro specify that the directory can only be mounted read only access=host:host only allow specified hosts to have access anon=uid map anonymous or unknown users to the specified uid secure clients must use secure RPC to access the file system root=host grant superuser access to the specified hosts Table 13.4. Export Options for NFS.For example:
An example /etc/exports file might be /home -rw=bertha:pol /usr/local -ro,access=bertha:pol:jasper:aldur This file specifies that the /home directory is exported for the hosts bertha and pol and they can read and write to that directory. /usr/local is exported read only to the hosts specified.Exercise 13.3. The machine aldur has the following directory hierarchy

and the following /etc/fstab file
/dev/hda1 / ext2 defaults /dev/hda2 /usr ext2 defaults /dev/hdb1 /usr/local ext2 defaultsIndicate whether the following /etc/exports files contain valid or invalid entries. If they are invalid, why?
a) /usr /usr/users b) /usr /usr/local
For example:
An example /etc/fstab file might be /dev/hda1 / ext2 /dev/hda2 /usr/local ext2 /dev/hdb1 /dosc msdos pol:/home/slackware /usr/local/slackware nfsFor example:
The command to mount the directory /home/slackware from the host pol is mount -t nfs pol:/home/slackware /mnt
Exercise 13-5. Determine where these daemons are started (if they are).
Exercise 13-6. Determine whether your machine is set up as an NFS client or server (or not at all).
Exercise 13-7. On your local site set up two machines as NFS server and client and using NFS share a particular directory between the two. Experiment with the options listed in Table 13.4.
Command Purpose traceroute to discover the route used by information flowing over the network between two hosts nslookup used to query nameservers to obtain IP addresses and other information about hosts Table 13.5. Useful Network Commands.
Remember it is not only the machines at the two ends you have to check. If the two machines are on different networks the information will flow through a number of gateways and routers. It might be one of the gateway machines that is causing the problem.
The traceroute command provides a way of discovering the path taken by information as it goes from one machine to another and the problems that may occur. On the Internet that path may not always be the same.
For example:
The following are the results of a number of executions of traceroute from the machine aldur (138.77.36.29). Refer back to Diagram 12.3 knuth is on the same network so no gateway was used bash$ traceroute knuth traceroute to knuth.cqu.edu.au (138.77.36.20), 30 hops max, 40 byte packets 1 knuth.cqu.EDU.AU (138.77.36.20) 2 ms 2 ms 2 ms a host one network away bash$ traceroute jasper traceroute to jasper.cqu.edu.au (138.77.1.1), 30 hops max, 40 byte packets 1 centaurus.cqu.EDU.AU (138.77.36.1) 1 ms 1 ms 1 ms 2 jasper.cqu.EDU.AU (138.77.1.1) 2 ms 1 ms 1 ms a machine still on the CQU site but a little further away bash$ traceroute jade traceroute to jade.cqu.edu.au (138.77.7.2), 30 hops max, 40 byte packets 1 centaurus.cqu.EDU.AU (138.77.36.1) 1 ms 1 ms 1 ms 2 hercules.cqu.EDU.AU (138.77.5.3) 4 ms 2 ms 12 ms 3 jade.cqu.EDU.AU (138.77.7.2) 3 ms 13 ms 3 ms A host still in Australia (but a long way from CQU) bash$ traceroute archie.au traceroute to archie.au (139.130.23.2), 30 hops max, 40 byte packets 1 centaurus.cqu.EDU.AU (138.77.36.1) 1 ms 1 ms 1 ms 2 tucana.cqu.EDU.AU (138.77.5.27) 2 ms 2 ms 2 ms 3 138.77.32.10 (138.77.32.10) 5 ms 5 ms 5 ms 4 qld.gw.au (139.130.60.1) 21 ms 13 ms 51 ms 5 national.gw.au (139.130.48.1) 35 ms 36 ms 40 ms 6 plaza.aarnet.edu.au (139.130.23.2) 38 ms 35 ms 68 ms A host in the Eastern United States bash$ traceroute sunsite.unc.edu traceroute to knuth.cqu.edu.au (139.130.23.2), 30 hops max, 40 byte packets 1 centaurus.cqu.EDU.AU (138.77.36.1) 1 ms 1 ms 1 ms 2 tucana.cqu.EDU.AU (138.77.5.27) 2 ms 2 ms 3 ms 3 138.77.32.10 (138.77.32.10) 5 ms 5 ms 5 ms 4 qld.gw.au (139.130.60.1) 13 ms 20 ms 13 ms 5 national.gw.au (139.130.48.1) 51 ms 36 ms 36 ms 6 usa.gw.au (139.130.29.5) 37 ms 36 ms 38 ms NOTICE THE TIME TO CROSS 7 usa-au.gw.au (203.62.255.1) 233 ms 252 ms 264 ms THE PACIFIC 8 * * t3-0.enss144.t3.nsf.net (192.203.230.253) 224 ms 9 140.222.8.4 (140.222.8.4) 226 ms 236 ms 258 ms 10 t3-3.cnss25.Chicago.t3.ans.net (140.222.25.4) 272 ms 293 ms 266 ms 11 t3-0.cnss40.Cleveland.t3.ans.net (140.222.40.1) 328 ms 270 ms 300 ms 12 t3-1.cnss48.Hartford.t3.ans.net (140.222.48.2) 325 ms 355 ms 289 ms 13 t3-2.cnss32.New-York.t3.ans.net (140.222.32.3) 284 ms 319 ms 347 ms 14 t3-1.cnss56.Washington-DC.t3.ans.net (140.222.56.2) 352 ms 299 ms 305 ms 15 t3-1.cnss72.Greensboro.t3.ans.net (140.222.72.2) 319 ms 344 ms 310 ms 16 mf-0.cnss75.Greensboro.t3.ans.net (140.222.72.195) 343 ms 320 ms * 17 cnss76.Greensboro.t3.ans.net (192.103.68.6) 338 ms 319 ms 355 ms 18 192.103.68.50 (192.103.68.50) 338 ms 330 ms 330 ms 19 rtp5-gw.ncren.net (128.109.135.254) 357 ms 361 ms * 20 * rtp2-gw.ncren.net (128.109.70.253) 359 ms 334 ms 21 128.109.13.2 (128.109.13.2) 374 ms 411 ms 451 ms 22 * calypso-2.oit.unc.edu (198.86.40.81) 418 ms 415 msExercise 13-8. For those of you connected to the Internet use the traceroute command to obtain the route between your machine and a machine in another country. Perform the same command twice. Each time send the output to a file. Compare the results.
Command Purpose ls [-ah] [domain] list information available for the current domain, -a lists host aliases, -t lists CPU and operating system information (output can be redirected to a file using >) set keyword [ = value ] change a variety of state information that affects how lookups are done host display information about host server host change the server to query to host root change the default server to the root server for the entire Internet, the machine, ns.nic.ddn.mil Table 13.6. Commands recognised by nslookup.For example:
bash$ nslookup Default Server: jasper.cqu.EDU.AU Address: 138.77.1.1 > ls cqu.edu.au all the machines this server knows about appearExercise 13-9. Using nslookup answer the following
The nameserver for the domain cc.uq.oz.au is the host cuscus (or at least it was at the time of writing).
The process can be divided into the following steps
There are a number of commands that may also make use of the above information and should be included in the startup scripts. Table 13.8 summarises these commands.
ifconfig is used to set up the software side of network interfaces so that they properly represent the systems values.
For example:
An example ifconfig command is /sbin/ifconfig eth0 138.77.37.28 broadcast 138.77.37.255 \ netmask 255.255.255.0 Information Configuration File IP address and hostname /etc/hosts hostname used by the hostname command in the startup files Domain name /etc/resolv.conf IP address and hostname of gateway /etc/gateways IP address and hostname of nameserver /etc/resolv.conf network address used in startup files and in/etc/networks broadcast address used in startup files Table 13.7. Configuration Files for Networking. Command Purpose ifconfig performs configuration so software will recognise each network card hostname initialises the hostname of your machine Table 13.8. Startup Commands for Network Configuration.
Installing a new device driver will differ between versions of the UNIX operating system and is covered in a later section.
Now you should notify those in charge of the local nameserver (possibly yourself) that your machine is up and talking to the network. They will then add your machine's host and IP address to the local nameserver that will allow other machines to connect to your machine.
Host Purpose gandalf system administrator's machine bilbo used by software development team frodo used by administration Table 13. e1.Table 13.e2 lists the more important users on each system, their accounts and requirements.
User Position Host Username for equivalent account yourself System Administrator gandalf, bilbo, frodo your username gandalf root bilbo root frodo root Arnold Pane Managing Director frodo arnold bilbo panea Andrew Hacker software engineer bilbo andrew Jim Tidey operator gandalf tideyj bilbo backup frodo backup Table 13. e2.(a) List the full paths, host and contents of all the files that need to be created to allow each user to use the remote commands (rlogin, rsh, rcp etc) between all of their accounts.
(b) Why might this not be a good idea?
David Jones (author)