Chapter 2 of PC Networks
HOME INTRODUCTION CHAPTER-2 CHAPTER-3 CHAPTER-4
CHAPTER-5 CHAPTER-6 CHAPTER-7 CHAPTER-8
Basics of Networks
The OSI Model
The OSI model was set by International Standards el is not a protocol, just a model for understanding and designing a network architecture that is flexible, robust and interoperable.
The Open Systems Interconnection model is a layered framework for design of network systems that allows for communication across all types of computer systems. It consists of seven separate but related layers, each one defining a segment of the process of moving information across a network.
The architecture of the OSI model goes like this: physical layer (layer 1), data link (layer 2), network (layer 3), transport (layer 4), session (layer 5), presentation (layer 6) and application (layer 7)
Functions of the Layers
Physical Layer
The physical layer coordinates the functions required to transmit a bit stream over a physical medium. It deals with the mechanical and electrical specifications of the interface and transmission medium. It also defines the procedures and functions that physical devices and interfaces have to perform for transmission to occur. In order for the bits to be send they must be encoded into signals – electrical or optical.Data Link Layer
Data link layer transforms the physical layer to a reliable link and is responsible for node to node delivery. It makes the physical layer appear error free to the network layer. The data link layer is responsible to divide the stream of bits received into manageable frames. Data link layer also checks the access on the link by the nodes, has error control and flow control system.Network Layer
The network layer is responsible for the source-to-destination delivery of a packet possibly across multiple networks. Network layer ensures that the packet gets from its point of origin to its final destination. Network layer is responsible for logical addressing and routing.Transport Layer
The transport layer is responsible for the source-to-destination of the entire message. Whereas network layer oversees end-to-end delivery of individual packets it does not recognize any relationship between the packets. Transport layer ensures that the whole message arrives to destination intact overseeing both error control and flow control. For more security the transport layer creates a connection between the two end ports. A connection is a single logical path between the source and destination that is associated with all packets in a message. The connection involves three steps: establishing a connection, data transfer and connection release. With this way the transport layer has more control over sequencing, flow and error detection and correction. Between the responsibilities of this layer is connection, flow and error control and also segmentation and reassembly at which process the message is divided into transmittable segments containing a sequence number and reassembles them by reaching the destination.Session Layer
The services provided by the first three layers (physical, data link and network) are not sufficient for some processes. The session layer is the network dialog controller. It establishes, maintains and synchronizes the interaction between communicating systems. The responsibilities of the session layer are: dialog control between two systems and synchronization which is used for large files.Presentation Layer
The presentation layer is concerned with the syntax and semantics of the information exchanged between two systems. The responsibilities of this layer include: Translation - the information should be changed from characters, numbers etc. to bit streams before they are transmitted. Encryption - there are private information transmitted over a network, so to ensure privacy we encrypt (change) the message into another code and the receiver decrypts it and read it. Compression - data compression reduces the number of bits to be transmitted.Application Layer
The application layer enables the user (human or software) to access the network. It provides user interfaces and support for services such as electronic mail, remote file access and transfer, shared database management and other types of distributed information services. The services provided by the application layer are as follows: Network virtual terminal- this is a software version of a physical terminal and allows a user to log on to a remote host. File transfer, access and management (FTAM) - this application allows user to access, retrieve or manage files in a remote computer. Mail services – this application provides the basis for e-mail forwarding and storage. Directory services – provides distributed database sources and access for global information about various objects and services.
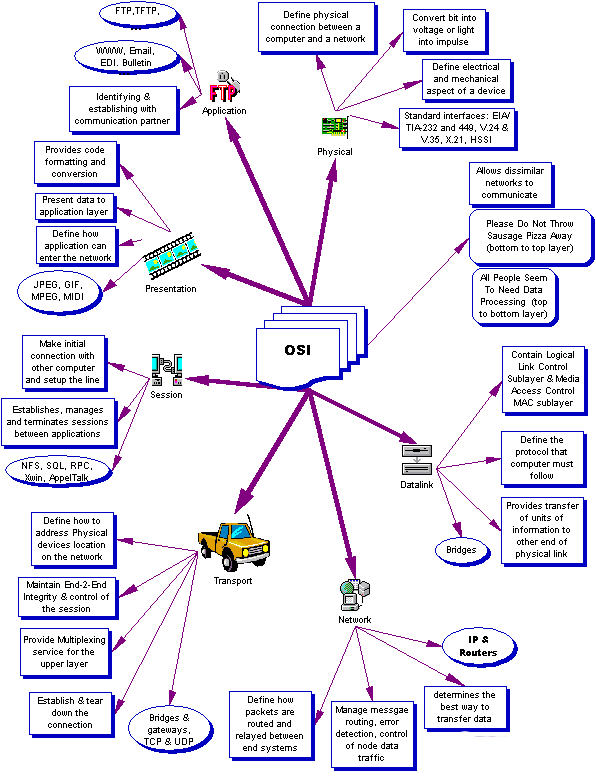
Network Topologies
The term topology derives from mathematics field that deals with points and surfaces in space which is the physical layout of objects in space. Topologies correspond to the OSI physical layer. There are three basic topologies: Ring, Bus and Star.
Ring Topology
In a ring topology the medium forms a closed loop and all stations are connected to the ring. The data are transferred from node to node in one direction. Let’s say we have four computers connected together in ring. In order for the information to pass from the first computer to the third it has to pass firstly through the second computer. If a computer is inactive (switched off) the information will not pass through and thus it will never reach its destination.

Token-ring is the most common microcomputer ring network. Token passing is one way in which a node gains access to the medium and passes messages. A token is a unique type of message that is passed from node to node and gives a node that receives the token the right to transfer data.
When a node receives the token it has either to send a message to another node or to pass the token to the next node. Thus one node can’t monopolize the medium by keeping the token indefinitely.
IBM choose token ring as its principal LAN topology. IBM’s approach has been adopted and conforms to the IEEE 802.5 standard. Token ring topology is not widely used today.
Bus Topology
In a bus topology the medium consists of a single wire to which nodes are attached. Unlike in a ring the ends of the bus are not connected, instead they are terminated by a hardware device called terminator. The purpose of the terminator is to eliminate signal feedback or loss at the endpoints. The cable used for this kind of connections is coaxial cable which usually is RG58 terminated at a matched impedance of 50O.
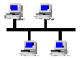
Star Topology
Star topology consists of a wiring hub at which all nodes are directly connected. This the commonest topology used in microcomputer networks. Star LAN technology was developed by AT&T Corporation. The topology was adopted and marketed as a low-cost low-speed option in the IEEE 802.3 standard. The primary medium used for star is the twisted pair wires currently at category 5 (category 6 is at an evolutionary station) and running at a maximum speed of 1Gbps.
There are also another two kinds of topologies which are taken out from the three basic topologies. The one is called mesh topology at which each node is directly connected to every other node in the network. This offer better security and speed. The other is called tree topology and is actually a secondary star topology coming from a bigger star connection.

Transmission Mode
The term transmission mode is used to define the direction of signal flow between two linked devices. There are three types of transmission modes: simplex, half-duplex and full-duplex.
In simplex mode the communication is unidirectional, as on a one way street. Only one of the two stations can transmit; the other can only receive. Classic simplex devices are the keyboards (input device) and monitors (output device).
In half-duplex mode each station can both receive and transmit but not at the same time. When one device is sending the other is only working as a receiver. In a half-duplex transmission the entire capacity of a channel is taken over by whichever of the devices is transmitting at the time. Walkie-talkies are a classic half-duplex device.
In full-duplex mode both stations can transmit and receive simultaneously. Signals going in either direction share the capacity of the link. This sharing may occur in two ways: either the link must contain two physically separate transmission paths one for sending and the other is receiving or the capacity of the channel is divided between signals traveling in opposite directions. An example of full-duplex transmission is the telephone network.Categories of Networks
When speaking for networks we actually talking about three primary categories of networks: local area networks, metropolitan area networks and wide area networks. The name of the network depends by its size, its ownership, the distance it covers and its physical architecture.
Local Area Networks
A local area network (LAN) is usually privately owned and links the devices in a single office, building or campus. The LAN may be as simple as two computers and a printer in someone’s home or may extend throughout a company and include voice, sound and video peripherals. LAN size is limited to few kilometers. LAN are designed to allow people exchange resources using their computers. The shared resources can be hardware, software or data. LAN should only use one type of transmission medium. The most common LAN topologies are bus, ring and star. LAN speeds can reach up to 1Gbps.
Metropolitan Area Network (MAN)
A metropolitan area network is designed to extend over an entire city. It may be a single network such as a cable television network or it may be a means of connecting a number of LANs into a larger network so that resources may be shared LAN-to-LAN as well as device-to-device. A MAN may be wholly owned by a private company or by a public company.
Wide Area Network (WAN)
A wide area network provides long distance transmission of data, voice, image and video information over large geographical areas that may comprise a country, a continent or even the whole world. WANs may utilize public, leased or private communication devices usually in combinations and can therefore span an unlimited number of miles.Protocols and Standards
Two computers cannot just send bit streams to each other and expect to be understood. They must agree on a protocol. A protocol is a set of rules that govern data communication. It defines how, when and what it is communicated. The key elements of a protocol are syntax, semantics and timing. Syntax refers to the structure of data, meaning the order in which they are presented. Semantics refers to the meaning of each section of bits. How is a particular pattern to be interpreted and what action is to be taken based on the interpretation. Timing refers to two characteristics: when data should be sent and how fast they can be sent.
The most common protocols we have now on our computers are: TCP/IP, IPX/SPX and NETBEUI.
NETBEUI (NETBios Extended User Interface)
The NETBEUI protocol is based on the NetBIOS protocol which was developed by IBM in 1984. NetBIOS was developed entirely for use with IBM PC Adapter Card. NETBEUI was introduced by IBM in 1985 and extends NetBIOS to a full networking protocol with additional features and services. When NETBEUI was designed it was assumed that LANs would use it locally not to get outside. In its latest release NETBEUI 3.0 it is a NetBIOS Frame (NBF) and has been adopted from Microsoft for their Windows NT and Windows for Workgroups. In the latest Windows XP Professional NETBEUI is not part of the protocols installed.
NETBEUI is the best performance choice for communication within a single LAN. It is optimized for high performance when used in departmental LANs or LAN segments. This was the primary reason why Microsoft used it to be their default protocol for Windows for Workgroups. It is a good protocol for a simple non mixed environment. It does not support routing of messages to other networks.
IPX/SPX (Internet Packet Exchange / Sequence Packet Exchange)
NetWare when first introduced in 1970 was a small operating system primarily offering file and print services. It was designed to be used by companies downsizing from mainframe to a network of personal computers. Advanced NetWare 86 had an adaptation of Xerox’s networking layer software known as Internet Packet Exchange (IPX). Advanced NetWare 286 ver. 2.11 had an adaptation of Xerox’s transport layer software known as Sequence Packet Exchange (SPX) which guaranteed reliable package delivery.
The IPX/SPX protocol can be combined with a variety of data link protocols. The SPX component is a reliable connection-oriented protocol. SPX provides services for flow control and the suppression of duplicate packages. It ensures that the data have been transferred to the destined computer. The IPX component provides the important service of routing and delivering data packets across an internetwork of workstations and servers. IPX makes its best to deliver the data to its destination but does not request any acknowledgment that the packet has reached its destination from the receiving machine. For a workstation to participate on an internetwork the IPX software must be loaded. Every server has a full IPX router built into it.
TCP/IP (Transmission Control Protocol / Internet Protocol)
TCP/IP is not a single protocol but a suite of over 100 protocols, each addressing a specific application within an internet. This is the factor which makes it so flexible. TCP/IP’s success is primarily due to the growth of the Internet. The fact that TCP/IP was developed in the 1960’s does not make it obsolete. Development on TCP/IP protocols continues as new demands are placed on internet. IP addressing has been strained to the point that new addresses are distributed on a limited basis. Old protocols have been updated and in some cases replaced by newer more robust protocols. There is no doubt that TCP/IP has a long future but let’s not forget the long past.
During 1950’s the U.S defense network consisted of several main-frame computers linked by point to point transmission links. The main concern at the time was the survivability of such a network during wartime. What was needed was a network which could heal itself. If any node or any section of the network were to suddenly become unreachable the rest of the network must be able to continue its operation. Such technology did not exist at the time so the Defense Communication Agency began development in the 1960’s on behalf of the Department of Defense.
The result was TCP/IP. The first efforts concentrated on the network layer (IP) and the transport layer (TCP) . Later, other protocols were added to provide additional functionality to the government internet. The Advanced Research Projects Agency (ARPA) network was the first commissioned in 1968 but without TCP/IP. The group was disbanded in1971 and work was resumed by the Defense Advanced Research Projects Agency (DARPA). DARPA began deploying TCP/IP in all ARPANET computers in 1983. This network remained in use until the last node was taken out in 1990.
Today the ARPANET is known as the Internet and it links millions of nodes that are connected via sub-networks located around the world. Today Internet is not under military use.
TCP/IP is successfully known for delivering basic services such as file transfer, e-mail, remote logon etc. TCP/IP provides a number of solutions that meet many corporate networking needs. It allows reasonably efficient and error-free transmission between different systems. A network design using the TCP/IP protocol allows the construction of a very large communication networks with less central management. The TCP/IP will be studied in more detail at a later stage.Standards
With so many factors to synchronize a great deal of coordination across the nodes of a network is necessary if communication is to occur at all, let alone accurately or efficiently. A single manufacturer may build all of its products to work well together but what if some of the best components you need are not made by the same company? Where there are no standards there are many difficulties. A steering wheel of one car make company definitely will not do on another car of another company without modifications. That is why we use standards. A standard provides a model for development that makes it possible for a product to work regardless of the individual manufacturer. Standards are essential in creating and maintaining an open and competitive market for equipment manufacturers and in guaranteeing national and international interoperability of data and telecommunications technology and processes. They give guidelines to the manufacturers, vendors, government agencies and other providers to ensure the kind of interconnectivity necessary in today’s marketplace and in international communications.
Data communication standards fall into two categories: De facto (mean “by fact”) and de jure (mean “by law”).
De jure standards are those that have been legislated by an officially recognized body.
De facto standards are often established originally by manufacturers seeking to define the functionality of a new product or technology. This category may be further sub-divided into proprietary and nonproprietary standards. Proprietary standards are those originally invented by a commercial organization as a basis for the operation of its products. They are called proprietary because they are wholly owned by the company that invented them. They are also called closed standards because they close communications with systems produced by different companies. Nonproprietary standards are those originally developed by groups or committees that have passed them into the public domain; they are also called open standards because they open communications between different systems.
Standards Organizations
Standards are created by cooperation among standards creation committees, forums and regulatory agencies. Some of these organizations are the follow:
® The International Standard Organization (ISO) – The ISO is an organization dedicated to worldwide agreement on international standards in a variety of fields.
® The International Telecommunications Union / Telecommunications Standards Sector (ITU-T) – It is an international standards organization related to the United Nations that develops standards for telecommunications.
® The American National Standards Institute (ANSI) – It is a nonprofit organization which is connected to ISO and ITU-T.
® The Institute of Electrical and Electronics Engineers (IEEE) – It is the largest national professional group involved in developing standards for computing, communication, electrical engineering and electronics. It was the sponsor of the Project 802 for LAN.
® The Electronic Industries Association (EIA) – It is an association of electronics manufacturers in the United States.
® Telcordia – Formerly called Bellcore is an outgrowth of the Bell Labs. Telcordia provides research and development resources for the advancement of telecommunications technology.
