On Encryption
I guess now is a good time as any to talk about encryption or the "E" word as a professor of mine used to say. Put very loosely, encryption is about transforming information into a form that cannot be interpreted by another without special knowledge such as the key. The counterpart to encryption is decryption and it essentially undoes the actions carried out on the original data also commonly known as the "plain text".
I use the word data to emphasize that current encryption techniques allow any form of information to be encrypted. The term "plain text" does not entail any restriction on the data form and can therefore be applied to pictures, songs, movies, etc. The counterpart of "plain text" is in turn the "cipher text". A well designed cipher should yield a "cipher text" characteristic to static (or random data.)
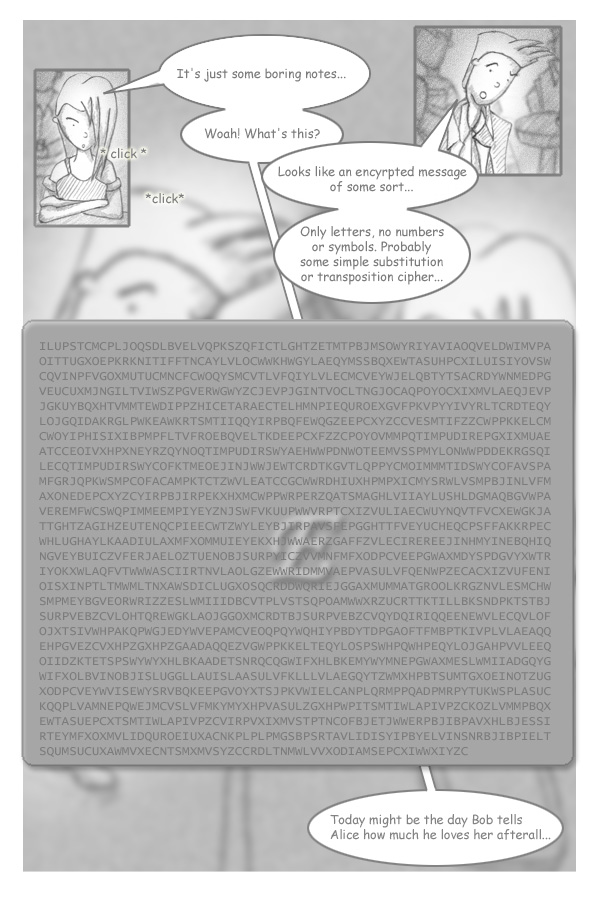
In this chapter, the cipher text consists only of the twenty-six alphabets and none of the numbers and symbols we commonly see (and certainly none of the unprintable ASCII codes.) This is an artifact of the choice of the cipher and is not at all exemplary of the form of encryption that is used in computer security. Incidentally, the cipher used here is a sixteenth century cipher.
Encryption is an age old technique, borne out of necessity in war and espionage. And back in the really old days, only messages were encrypted and hence the text-only plain text and cipher text. In addition, encryption techniques fell into two main branches - transposition and substitution. Although current encryption techniques are now more complex, transposition and substitution remain important steps in any cipher.
Transposition refers to the rearrangement of the characters according to a known pattern. For instance, BROWN could be transposed as BONRW by skipping every alternate letter. However, as the letter composition of the plain text and cipher text is essentially the same, short messages can be broken rather easily with the aid of an anagram generator. (Well, to be fair, anagram generators did not exist in those days.)
Substitution refers to the replacement of each letter in the alphabet set by another. As a simple example, if we were to replace each letter by the letter preceding it as accorded to the order in the alphabet, then BROWN would become AQNVM.
Today, rather than encrypt individual letters, data is divided into block sizes (usually 32bit or 64bit.) Beyond transposition and substitution, modern ciphers also employ techniques like block size expansion, mathematical transformations and logical operations. Nevertheless, the objective of encryption remains unchanged to this very day - to obfuscate data so as to render it unreadable other than to its intended recipient.
I might make the program available in the future or I might code up some packaged program. Who knows?
Next