| Home │ Part: 2 │ 3 │ 4 │ 5 │ 6 │ 7 │ 8 │ 9 │ | ||||||||||
Administrator Password in Windows XP: how to reset it if you forget (in 9 parts)Part 1. Introduction and Windows Password Reset Disk (PRD) This articles applies to Windows XP Home or Professional standalone or workgroup computer not in a domain Topics on this page: [1] Introduction
[2] Creating a Password Reset Disk (PRD) with the Forgotten Password Wizard [3] The consequences of resetting or blanking your password
1. Introduction1.1. Good practicesThis series would rescue you from having to reinstall Windows XP when you forget your administrator password and to prevent this happening. It also reviews critically and demonstrates some of the other methods so you will have a choice of the tools that best fit your needs. If you cannot logon to Windows at all you will have to resort to using one of the available alternate methods. This is an interesting subject and is not in MCP/MCSE curriculum. Should you lose your Windows XP user account password it is really your own fault by not remembering it or having made a password reset disk beforehand (see below). Also setting a password hint would help if you are forgetful. You should not use the Administrator account for daily routine work in any case but with another administrative account or limited account. This way, if you lose your own account password there is still the Administrator account to fall back on.
1.2. Administrator and administrative user accounts in Windows XP Professional and Home Editions1.2.1. Administrator and administrative user accounts are not the same in Windows XP ProfessionalDon't panic: first ask if your account is the built-in Administrator account (equivalent to Unix/Linux root administrator); this account cannot be deleted (but can be renamed or disabled via Local Security Policy) and is referred to with a capital A in this article as it appears on the Windows XP Start menu (fig. 1) and in User Account when logged on as Administrator (see fig. 2 below). If instead it is a user account with administrative privileges (with a small letter "a" in this article) which you can create or delete after installation, it would be less drastic to lose the password in this scenario because you still have the built-in Administrator account to fall back on.
Fig. 1. Built-in Administrator account in Windows XP Professional.
In factory desktop and laptop computers with Windows XP Professional pre-installed (not as common as with Windows XP Home Edition in factory computers), the Administrator password should be blank when set up by the factory using Sysprep (Windows System Preparation tool). Normally when you start up the computer for the first time, the Sysprep Mini-Setup Wizard runs and prompts you for some customised settings, including the Administrator password. So this is a scenario whereby the Administrator password may be left blank or otherwise. When you manually install Windows XP Professional, Setup will prompt you for the Administrator password. For Windows XP Home Edition, read on.
1.2.2. The Administrator account password is blank in Windows XP Home Edition by defaultThe Administrator account is BLANK (no password) in Windows XP Home Edition by default (whether you install it manually or use Sysprep) and is normally inaccessible except in Safe Mode. So if you haven't set a password (or are not even aware of this account) it should not be a problem if you normally use another administrative user account. In contrast during setup in Windows XP Professional you will be prompted to create a password (it doesn't do that in Windows XP Home Edition during Setup), unless you deliberately chose a blank password during Setup.
1.3. Be prepared: make a Password Reset disk (PRD) nowYou should have prepared a Password Reset disk straight after installation in case you forget the password. If you haven't done so, I strongly urge you to do it now by following the steps below. It is by far the simplest thing to do for prevention for both types of accounts. It, however, cannot be used for domain accounts (which can be hacked via different means).
1.4. Security Account Manager (SAM)If you don't have this password reset disc it means trouble because the registry Security Account Manager (SAM) contains your encrypted password in binary and cannot normally be accessed or changed outside Windows environment. If you use NTFS there is an extra barrier for reading the file in DOS or Linux but it can be done, as will be shown later.
1.5. A few comments on the methodsThe methods used are destructive: they reset a new password or blank it and do not recover the lost one. Therefore it has potentially serious consequences (see below). All the available methods (Linux or DOS based) work for FAT and NTFS. I've only evaluated them on the English US version of Windows XP Professional. I cannot say if they will work equally well in other localised language versions (but they should). The methods for Windows XP in a domain and Windows Server 2003 are not the same and will not be covered here (see the references). Also some of the methods published elsewhere (which applied to Windows NT and 2000) no longer seem to work in Windows XP (presumably because of tightened security) and I will discuss them in the last part. Doing a repair installation would not help because it asks you for the Administrator password during set up. You can of course reformat and reinstall Windows XP but you lose all your data and settings. That is one of the compelling reasons why you should not keep your data in My Documents or in the Windows (boot) partition. You can move My Documents elsewhere or redirect it centrally if joined to a domain. You can move your hard disc temporarily to another Windows XP computer as slave and retrieve your data before reformatting but that is tedious to do. The available methods in broad categories are:
1.6. Windows XP Recovery Console Password authenticationNormally the Administrator account password is required to logon to the Recovery Console, unless this requirement has been cancelled via a policy (read my article on Group Policy). So don't expect to go to the Recovery Console to do anything if the password is forgotten. There is a problem if your Administrator account (blank or otherwise) is not accepted (even though it is normally valid) when trying to logon to the Recovery Console in factory computers due to a bug in the password authentication process when Windows XP is installed using Sysprep (KB 308402). The KB article advised installing SP1 (which didn't solve it when I tried; I haven't tried it after SP2) or use the new set of bootable floppy disks. It has also been reported (but unconfirmed) that using one of the methods described in this series to blank the password can solve this.
1.7. Important: Disclaimer and warningIt's not my intention whatsoever to teach you how to crack other users' passwords or other computers without permission or where it is illegal but just to offer some tips to manage your own password legitimately. Be warned that I shall not in any way be liable for your actions. Also, the instructions in the article are for demonstration purposes and in no way reflect what I do. I am not affiliated with any of the software developers or commercial companies mentioned.
2. Creating a Password Reset Disk (PRD) with the Forgotten Password WizardYou need to make a separate floppy for each account which is logged on. You cannot make all the reset disks from within one account. The disk won't work on another account whether or not a reset disk was made or on another computer. To run the Forgotten Password Wizard, logon to your Administrator or administrative user account. To logon the Administrator account in Windows XP Professional, press Ctrl + Alt + Del twice at the Welcome screen or enter Administrator in the User Name box in the classic logon screen. In Windows XP Home edition, you have to press F8 to go to Safe Mode before the seeing the Administrator account in the Welcome screen (you only need to type the Administrator password if you have set a password before). After you log on, go to Control Panel, User Accounts, click on your account in the bottom; here the Administrator account is used as an example (fig. 2). You can access the Control Panel in Safe Mode in Windows XP Home edition.
Fig. 2. Control Panel, User Accounts
In the next User Accounts window on the left pane, under Related Tasks, click Prevent a forgotten password (fig. 3). This option is only available for the account that you are currently logged on. You cannot make a PRD for other accounts other than the one you're logged on even if you're logged on as Administrator or administrative user.
Fig. 3. Prevent a forgotten password link.
Follow the instructions in the wizard (fig. 4). Note that you only need to do this once even when you change or reset your password later.
Fig. 4. Welcome to the Forgotten Password Wizard.
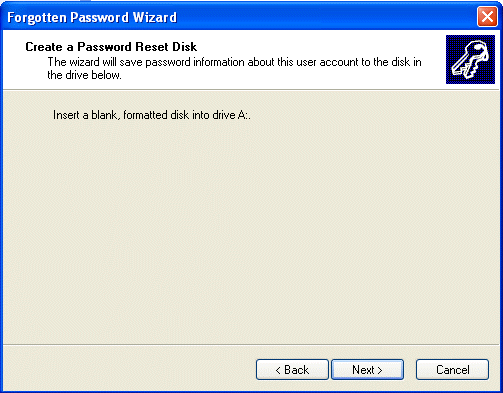
Insert a blank formatted floppy (fig. 5).
Fig. 5. Insert a blank formatted floppy.
You need to know your account password and enter it and click Next (fig. 6).
Fig. 6. Type your current account password.
The file Userkey.psw is written onto the floppy (fig. 7 and 8).
Fig. 7. File is written onto the floppy.
Fig. 8. userkey.psw file
Click Finish (fig. 9) to exit. Label and keep the floppy in a safe place. Repeat the above steps for each account.
Fig. 9. Completing the wizard.
3. The consequences of resetting or blanking your passwordIf you don't reset your password in the normal way but instead crack or blank it by other means you may lose data files or settings such as:
See figures 7 and 11 in Part 2 for illustrations showing such warnings. Encrypted folders using EFS is usually impossible to recover unless you have another recovery agent. One tool (Passware Kit Enterprise, see Part 6) claims it can but I've tried its EFS recovery tool. I will mention SAM again in Part 9 but I should warn you right at the outset. If you try the drastic measure and delete the registry SAM key which stores your user passwords you will lose your user account and everything that ties with it. It is like deleting your user account in the normal way in User Accounts. Even when you re-create your account with the same name, you will not be able to recover your data because your old user folder will have been deleted and a new one created.
To be continued in other parts.
Copyright � 2003-2005 by Kilian. All my articles including graphics are provided "as is" without warranties of any kind. I hereby disclaim all warranties with regard to the information provided. In no event shall I be liable for any damage of any kind whatsoever resulting from the information. The articles are provided in good faith and after some degree of verification but they may contain technical or typographical errors. Links to other web resources may be changed at any time and are beyond the control of the author. Articles may be added, removed, edited or improved at any time. No support is provided by the author. This is not an official support page for any products mentioned. All the products mentioned are trademarks of their companies. Created 2 Mar 2004; last updated 21 June 2006 |
||||||||||