Module
1: The Windows NT 4.0 Environment
| Differences between Windows
95 and Windows NT workstation |
|
Technical area
|
Windows 95
|
Windows NT workstation
|
| Minimum
hardware |
486
with 8-16 MB RAM |
Pentium
with 12-32 MB RAM 12 MB on a RISC-based computer |
| Hard
disk space |
40
MB |
110
MB |
| Software
compatibility |
Very
high |
High:
does not allow apps. to access hardware directly. |
| Hardware
& device compatibility |
Very
high |
High:
supports most devices |
| Installation
and deployment |
Comprehensive
detection code and can configure most |
Less
comprehensive detection code, and static driver support |
| APM
& Plug and Play |
Built-in
(also for laptops) |
Non
built-in (some by OEM) |
| Performance |
Preemptive
multitasking for 32-bit Apps. |
Preemptive
multitasking for all Apps. |
| Reliability/stability |
High,
improved over WFW |
Very
high: all Apps run in protected memory space. |
| Security |
Support
for server-based logon validation |
Complete
protection down to file-level (when using NTFS) |
- Supports 4 microprocessors in a Symmetric Multiprocessing
Environment (SMP). Some implementations by OEM support up to 32 microprocessors.
- 256 inbound RAS connections.
- Supports RAID.
- Integration of IIS (Internet Information Server)
means; Web install and management is simply part of the OS.
- With IIS version 2.0 : Administering web
sites remotely from any computer with an internet browser installed and
providing a fast secure platform for HTTP, FTP and Gopher services.
- Administrative Wizards to help perform tasks.
- File & printer sharing for MAC.
- DNS-, DHCP- and WINS-server.
- Windows NT Directory Services (NTDS) -->
Manages secure distributed directory database and provides services for end
users and network administrators.
| Note: |
Hardware requirements for NTS are:
- 486DX/33,
- 16MB RAM,
- and 125MB disk space.
|
Common features:
- Multi-platform.
- Multitasking and multi-threading operations.
- Security:
- Mandatory logon.
- Discretionary access control.
- Memory protection.
- Auditing.
- Support for following OS:
- MS-DOS
- Win16
- Win32
- OS/2
- POSIX (UNIX)
- Supports 4 GB of RAM, 16 Exabytes of HD-space.
- File systems supported are: FAT, NTFS, and
CDFS.
Differences:
- Windows NT server is tuned for server-based application such as SNA server,
SQL server, SMS and MS exchange server. Windows NT workstation is designed
for multitasking desktop operating system.
- Windows NT workstation has a limit of ten incoming concurrent sessions while
Server’s is limited by licenses.
| Windows NT Architecture Overview |
- Windows NT uses User mode and Kernel mode to
maintain operating efficiency and offering integrity.
- is applicable to Applications and subsystems.
- It has the following limitations:
- No direct access to hardware.
- Limited to assign address space.
- May need to use hard disk space as virtual
RAM.
- Processes at a lower priority level than
Kernel mode.
- Windows NT Executive runs here to protect
executive services.
- Apps cannot directly access the memory of
any kernel mode service.
- Only Kernel mode components can access resources
(i.e. hardware) directly
- Windows NT works underneath user Apps and environment
subsystems to provide support for the applications. These operating components
are in the Windows NT executive.
There are three types of Kernel mode components in the Windows NT Executive:
- Executive services:
- Managers --> are
the various modules that manage I/O, objects, security, processes, Inter
Processes Communications (IPC), virtual memory and window/graphic management.
- Device drivers --> these
are modules that control hardware access.
- Microkernel: Provides most basic
OS system services, such as thread scheduling and interrupt handling.
- Hardware Abstraction Layer (HAL):
Code that isolates most hardware interface differences from Windows NT, making
it more portable.
| The Windows NT Memory Model |
- The memory architecture of Windows NT is a
demand-paged virtual memory system, based on a flat linear 32-bit address
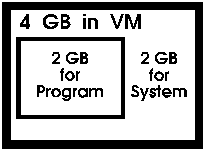
space; which allows each process in Windows NT to have access to up to 4 GB
of memory.
| Virtual Memory Architecture |
- Windows NT gives each application, a private
memory range called "Virtual Memory Space" and mapping that
virtual memory to physical memory.
- Windows NT maps the memory addresses in 4 KB
blocks called Pages. Each virtual memory space has room for 4 GB of
addresses. This space is made up of 1 MB of 4 KB pages.
Each of the pages in the applications virtual
memory space can have one of the following three characteristics:
- Most are empty (or unused by the application).
- Pages used are redirected to physical RAM
by a pointer (invisible for the application).
- Some pages that have not been used recently
contain another pointer to a 4KB section of the paging file on the hard
disk.
Using the Virtual Memory Process, some of the applications code is kept into
RAM while some of it is on the physical disk. The process of managing this
is called: "Demand Paging", and follows these 4 steps:
- Application attempts to store data in memory.
- Virtual Memory Manager intercepts the request,
determines the number of pages to use, and then maps unused physical memory
to any empty address space in the applications Virtual Memory Space as needed.
- If there is not enough physical memory available,
the Virtual Memory Manager uses demand paging to find 4KB pages of RAM that
hasn't been used recently, and copies the data to the paging file (pagefile.sys).
Newly freed RAM is remapped to fulfill the applications request. (i.e. it
gets rid of the old stuff not being used and swaps it to the pagefile for
the stuff the application wants.)
- When the data in the pagefile is needed,
pages are copied back into RAM. The new RAM location is mapped back to the
same virtual address required by the application. ( i.e. just the reverse
of #3)
| Virtual Memory Advantages |
This way of memory addressing makes Windows NT portable, because it is compatible
with the addressing of other microprocessors like:
- MIPS R4000.
- IBM RS6000.
- DEC Alpha AXP.
Computers in a Domain:
|
Advantages
|
Disadvantages
|
| Centralized
account and security administration. |
Requires
at least one Windows NT Server domain controller. |
| Single
user logon provides network-wide resource access. |
Requires
additional planning prior to deployment. |
In a domain Windows NT computers perform
the following tasks:
- User validation, using the directory database.
- Allow resources access to users defined in
the directory database.
- Function as part of an administered group.
The Workgroup model (uses 1 browserlist):
|
Advantages
|
Disadvantages
|
| Does
not require a Windows NT domain controller. |
No
centralized account management. |
| Simple
design and implementation. |
Inefficient
for networks that have many computers. |
| Easy
when using only a few computers in at close range. |
Limited
centralized administrative control. |
- The logon procedure on Windows NT is mandatory
and cannot be disabled. It provides users with individual configurations,
including; desktop and network connections, that are saved when a user logs
of.
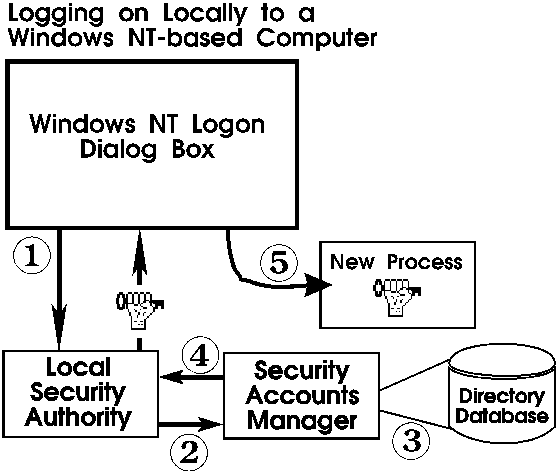
There are five steps to a successful logon process:
- WinLogon requests a user name and password. The user name and password are
sent to the Local Security Authority (LSA) in the security subsystem.
- The LSA queries the Security Accounts Manager (SAM) to see if the user name
and password are authorized
- The SAM checks the user name and password against information in the directory
database.
- If access is approved, the LSA creates an access token with the granted
access rights and passes it back to the WinLogon process.
- The logon process calls for a new process for the user, usually Explorer.exe,
to which the user's token is attached.
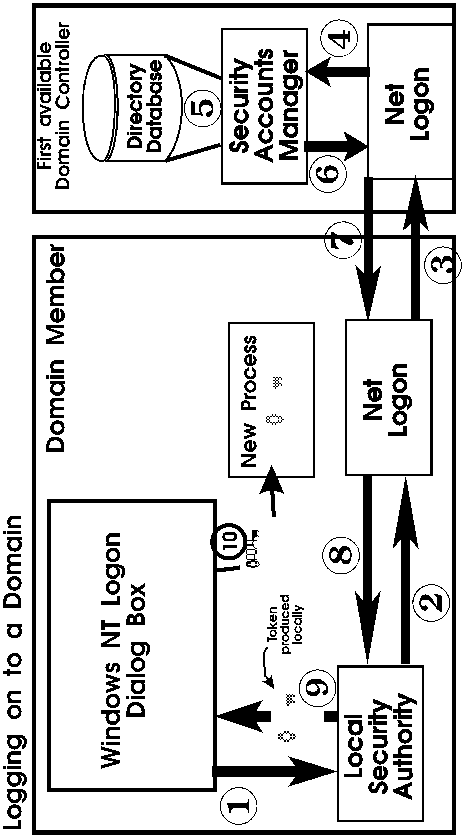
Logging on to a Domain ( see pic at end of module)
There are ten steps to a successful domain logon process:
- WinLogon requests a user name and password. These are sent to the Local
Security Authority (LSA) in the security subsystem.
- The security subsystem passes the request to the client's Net Logon service.
- The client's Net Logon service send the request to the Net Logon service
on the first available domain controller.
- The domain controller's Net Logon service passes the request to the domain
controller's Security Accounts Manager (SAM)
- The SAM queries the domain directory database for username and password
approval.
- The domain controller's SAM passes the result of the logon attempt to the
domain controller's Net Logon service.
- The domain controller's Net Logon service passes the result to the client's
Net Logon service.
- The Net Logon service passes the result to the client's Local Security Authority.
- If access is approved, the client's LSA creates an access token with the
granted access rights and passes it back to the client's WinLogon process.
- WinLogon calls the Win32 subsystem to create a new process for the user,
passing the access token to the subsystem. Win32 attaches the token to the
new process.
| Creating a Computer Account |
- Before computers can logon to a domain, they
must have an account in the domain.
- If you can't create an account and are on a
computer running NTWS or a member server, you will have to use the network
program in the control panel. If the account does not exist yet in the domains
database, select the "create computer account in the domain" option.
Remember: To do this, an account name
that has "Add computer to the domain" rights is required.
 Comments and suggestions? E-mail me at
grantwilson21@yahoo.com
Comments and suggestions? E-mail me at
grantwilson21@yahoo.com
I'm sorry, but I can't answer specific network-related, or exam-related questions. |
| Last Updated: August 6, 2001 |
Grant Wilson, Edmonton, AB
Canada |


